70-744 Exam Questions - Online Test
70-744 Premium VCE File

150 Lectures, 20 Hours
for Microsoft certification, Real Success Guaranteed with Updated . 100% PASS 70-744 Securing Windows Server 2021 exam Today!
Free demo questions for Microsoft 70-744 Exam Dumps Below:
NEW QUESTION 1
You deploy the Host Guardian Service (HGS).
You have several Hyper-V hosts that have older hardware and Trusted Platform Modules (TPMs) version 1.2.
You discover that the Hyper-V hosts cannot start shielded virtual machines.
You need to configure HGS to ensure that the older Hyper-V hosts can host shielded virtual machines. What should you do?
- A. Run the Set-HgsServer cmdlet and specify the -TrustTpm parameter.
- B. Run the Set-HgsServer cmdlet and specify the -TrustActiveDirectory parameter.
- C. Run the Clear-HgsServer cmdlet and specify the -Clustername parameter
- D. Run the Clear-HgsServer cmdlet and specify the -Force parameter.
- E. It is not possible to enable older Hyper-V hosts to run Shielded virtual machines
Answer: E
Explanation: Requirements and Limitations
There are several requirements for using Shielded VMs and the HGS:
One bare metal host: You can deploy the Shielded VMs and the HGS with just one host. However,
Microsoft
recommends that you cluster HGS for high availability.
Windows Server 2021 Datacenter Edition: The ability to create and run Shielded VMs and the HGS is only
supported by Windows Server 2021 Datacenter Edition.
For Admin-trusted attestation mode: You only need to have server hardware capable of running Hyper-V in
Windows Server 2021 TP5 or higher.
For TPM-trusted attestation: Your servers must have TPM 2.0 and UEFI 2.3.1 and they must boot in UEFI
mode. The hosts must also have secure boot enabled. Hyper-V role: Must be installed on the guarded host. HGS Role: Must be added to a physical host. Generation 2 VMs.
A fabric AD domain.
An HGS AD, which in Windows Server 2021 TP5 is a separate AD infrastructure from your fabric AD.
NEW QUESTION 2
Encryption-supported VMs are intended for use where the fabric administrators are fully trusted. For example, an enterprise might deploy a guarded fabric in order to ensure VM disks are encrypted at-rest for compliance purposes.
Shielded VMs are intended for use in fabrics where the data and state of the VM must be protected from both fabric administrators and untrusted software that might be running on the Hyper-V hosts. Is the Virtual Machine Connection (Console), HID devices (e.g. keyboard, mouse) ON or OFF for Encryption Supported VM’s?
- A. Off
- B. On
Answer: B
NEW QUESTION 3
DRAG DROP
You configure Just Enough Administration (JEA).
You need to ensure that a non-administrator user can perform the following actions:
-Restart Internet Information Services (IIS)
-Restart a custom service named Service1.
How should you complete the role configuration file? To answer, select the appropriate options in the answer area.
Answer:
Explanation: VisibleExternalCommands = ‘C:\Windows\system32\iisreset.exe’
VisibleCmdlets = @{ Name ‘Restart-service’ ; Parameters @{ Name = ‘Name’; ValidateSet = ‘Service1’}}
https://docs.microsoft.com/en-us/powershell/jea/role-capabilities
NEW QUESTION 4
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer
choices, but the text of the scenario is exactly the same in each question in this series. Start of repeated scenario
Your network contains an Active Directory domain named contoso.com. The functional level of the forest and the domain is Windows Server 2008 R2.
The domain contains the servers configured as shown in the following table.
All servers run Windows Server 2021. All client computers run Windows 10.
You have an organizational unit (OU) named Marketing that contains the computers in the marketing department You have an OU named finance that contains the computers in the finance department You have an OU named AppServers that contains application servers. A Group Policy object (GPO) named GP1 is linked to the Marketing OU. A GPO named GP2 is linked to the AppServers OU. You install Windows Defender on Nano1.
End of repeated scenario
You need to exclude D:Folder1 on Nano1 from being scanned by Windows Defender. Which cmdlet should you run?
- A. Set-StorageSetting
- B. Set-FsrmFileScreenException
- C. Set-MpPreference
- D. Set-DtcAdvancedSetting
Answer: C
Explanation: https://technet.microsoft.com/en-us/itpro/powershell/windows/defender/set-mppreference
NEW QUESTION 5
You have a server named Server1 that runs Windows Server 2021.
You need to identify whether IPsec tunnel authorization is configured on Server1. Which cmdlet should you use?
- A. Get-NetIPSecRule
- B. Get-NetFirewallRule
- C. Get-NetFirewallProfile
- D. Get-NetFirewallSetting
- E. Get-NetFirewallPortFilter
- F. Get-NetFirewallAddressFilter
- G. Get-NetFirewallSecurityFilter
- H. Get-NetFirewallApplicationFilter
Answer: A
Explanation: https://technet.microsoft.com/en-us/itpro/powershell/windows/netsecurity/get-netipsecrule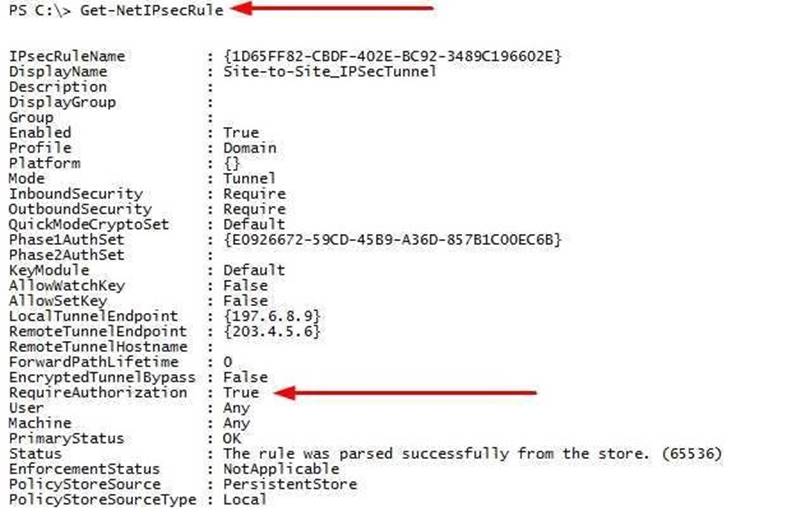
NEW QUESTION 6
Note: The question is part of a series of questions th« present the same scenario. Each question In the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to It. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest named contoso.com. All servers run Windows Server 2021. The forest contains 2,000 client computers that run Windows 10. All client computers are deployed from a customized Windows image.
You need to deploy 10 Privileged Access Workstations (PAWs). The solution must ensure that administrators can access several client applications used by all users.
Solution: You deploy 10 physical computers and configure them as PAWs. You deploy 10 additional computers and configure them by using the customized Windows image.
Does this meet the goal?
- A. Yes
- B. No
Answer: A
Explanation: References:
https://technet.microsoft.com/en-us/windows-server-docs/security/securing-privilegedaccess/privileged-access-workstations
NEW QUESTION 7
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2021.
You have an organizational unit (OU) named Administration that contains the computer account of Server1.
You import the Active Directory module to Server1.
You create a Group Policy object (GPO) named GPO1. You link GPO1 to the Administration OU. You need to log an event each time an Active Directory cmdlet executed successfully from Server1. What should you do?
- A. From Advanced Audit Policy in GPO1. configure auditing for other privilege use events.
- B. Run the Add-NetEventProvider -Name “Microsoft-Active-Directory” -MatchAnyKeyword PowerShell command.
- C. From Advanced Audit Policy in GPO1, configure auditing for directory service changes.
- D. From Administrative Templates in GPO1, configure a Windows PowerShell polic
Answer: D
Explanation: In the following GPO location, you can enable the setting “Turn on Module Logging” to record an
event each
time the PowerShell executes a cmdlet of a specific PowerShell module, for example “ActiveDirectory”.
“Computer Configuration\Administrative Templates\Windows Components\Windows PowerShell”
NEW QUESTION 8
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2021.
The hardware configuration on Server1 meets the requirements for Credential Guard. You need to enable Credential Guard on Server1.
What should you do? To answer, select the appropriate options in the answer area.
Answer:
Explanation: References:
https://docs.microsoft.com/en-us/windows/access-protection/credential-guard/credential-guardrequirements https://docs.microsoft.com/en-us/windows/access-protection/credential-guard/credential-guardmanage# hardware-readiness-tool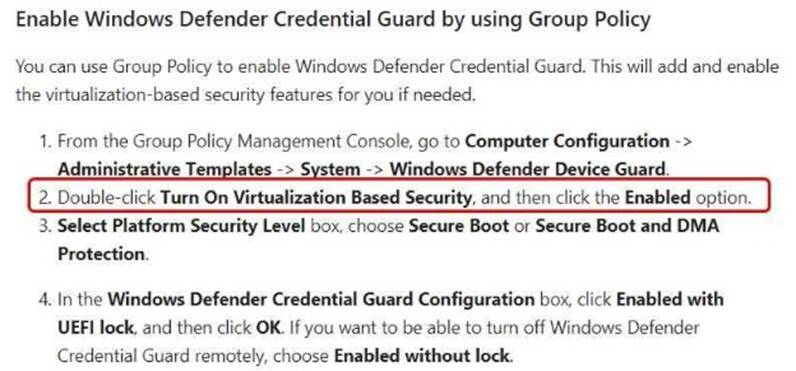
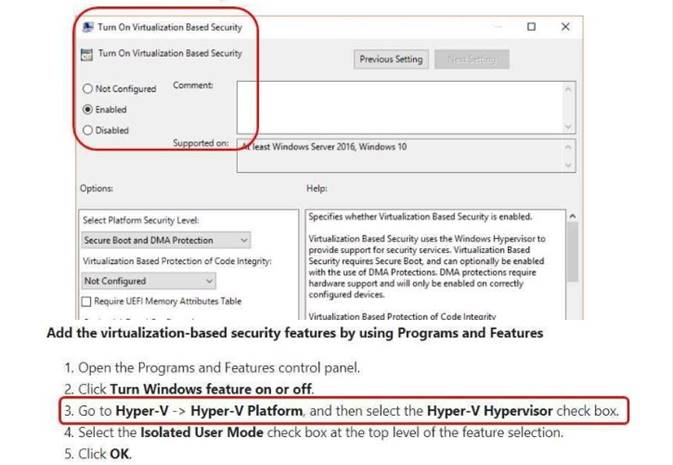
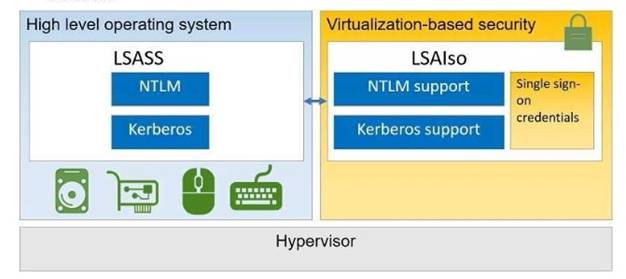
NEW QUESTION 9
Your network contains several secured subnets that are disconnected from the Internet.
One of the secured subnets contains a server named Server1 that runs Windows Server 2021.
You implement Log Analytics in Microsoft Operations Management Suite (OMS) for the servers that connect to the Internet.
You need to ensure that Log Analytics can collect logs from Server1.
Which two actions should you perform? Each correct answer presents part of the solution.
- A. Install the OMS Log Analytics Forwarder on a server that has Internet connectivity.
- B. Create an event subscription on a server that has Internet connectivity.
- C. Create a scheduled task on Server1.
- D. Install the OMS Log Analytics Forwarder on Server1.
- E. Install Microsoft Monitoring Agent on Server1.
Answer: AE
Explanation: https://docs.microsoft.com/en-us/azure/log-analytics/log-analytics-oms-gateway OMS Log Analytics Forwarder = OMS Gateway
If your IT security policies do not allow computers on your network to connect to the Internet, such as point of sale (POS) devices, or servers supporting IT services, but you need to connect them to OMS to manage and monitor them, they can be configured to communicate directly with the OMS Gateway (previous called “OMS Log Analytics Fowarder”) to receive configuration and forward data on their behalf.
You have to also install Microsoft Monitoring Agent on Server1 to generate and send events to the OMS
Gateway,since Server1 does not have direct Internet connectivity.
NEW QUESTION 10
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1.
Server1 is configured as shown in the following table.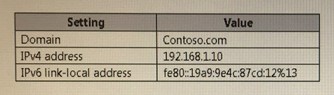
You plan to create a pilot deployment of Microsoft Advanced Threat Analytics (ATA). You need to install the ATA Center on Server1.
What should you do first?
- A. Install Microsoft Security Compliance Manager (SCM).
- B. Obtain an SSL certificate.
- C. Assign an additional IPv4 address.
- D. Remove Server1 from the domai
Answer: B
Explanation: https://docs.microsoft.com/en-us/advanced-threat-analytics/ata-prerequisites
ATA Center which is the first component to be deployed on Server1, requires the use of SSL protocol to
communicate with ATA Gateway
To ease the installation of ATA, you can install self-signed certificates during installation.
Post deployment you should replace the self-signed with a certificate from an internal Certification Authority tobe used by the ATA Center.
Make sure the ATA Center and ATA Gateways have access to your CRL distribution point.
If the they don’t have Internet access, follow the procedure to manually import a CRL, taking care to install the all the CRL distribution points for the whole chain.
NEW QUESTION 11
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this sections, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com. All servers run Windows
Server 2021. All client computers run Windows 10.
The relevant objects in the domain are configured as shown in the following table.
You need to assign User1 the right to restore files and folders on Server1 and Server2. Solution: You add User1 to the Backup Operators group in contoso.com.
Does this meet the goal?
- A. Yes
- B. No
Answer: A
Explanation: References:
https://technet.microsoft.com/en-us/library/cc771990(v=ws.11).aspx users.
The solution would let User1 to backup files and folders on domain controllers for contoso.com instead.
NEW QUESTION 12
You have a server named Server1 that runs Windows Server 2021.
You need to identify whether any inbound rules on Server1 require that users be authenticated
before they can connect to the server. Which cmdlet should you use?
- A. Get-NetIPSecRule
- B. Get-NetFirewallRule
- C. Get-NetFirewallProfile
- D. Get-NetFirewallSetting
- E. Get-NetFirewallPortFilter
- F. Get-NetFirewallAddressFilter
- G. Get-NetFirewallApplicationFilter
Answer: B
Explanation: The complete cmdlet to perform the required action:-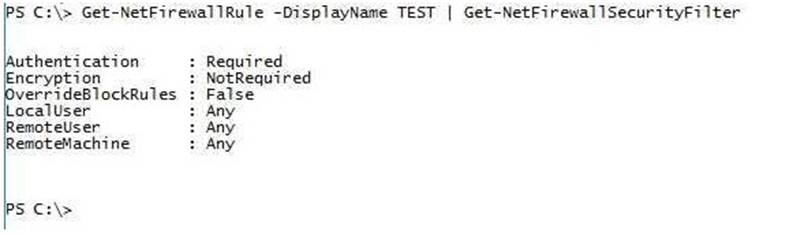
NEW QUESTION 13
Your network contains an Active Directory domain named conioso.com. The domain contains 1,000 client computers that run Windows 8.1 and 1,000 client computers that run Windows 10.
You deploy a Windows Server Update Services (WSUS) server. You create a computer group tor each organizational unit (OU) that contains client computers. You configure all of the client computers to receive updates from WSUS.
You discover that all of the client computers appear m the Unassigned Computers computer group in the Update Services console.
You need to ensure that the client computers are added automatically to the computer group that corresponds to the location of the computer account in Active Directory.
Which two actions should you perform? Each correct answer presents part of the solution.
- A. From Group Policy objects (GPOs), configure the Enable client-side targeting setting.
- B. From the Update Services console, configure the Computers option.
- C. From Active Directory Users and Computers, create a domain local distribution group for each WSUS computer group.
- D. From Active Directory Users and Computers, modify the flags attnbute of each OU.
- E. From the Update Services console, run the WSUS Server Configuration Wizar
Answer: AB
NEW QUESTION 14
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario b repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario
Your network contains an Active Directory domain named contoso.com. The functional level of the forest and the domain is Windows Server 2008 R2.
The domain contains the servers configured as shown m the following table.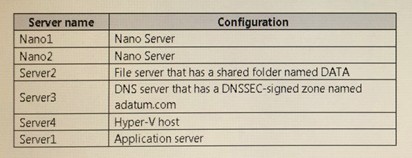
All servers run Windows Server 2021. All client computers run Windows 10.
You have an organizational unit (OU) named Marketing that contains the computers in the marketing department You have an OU named Finance that contains the computers in the finance department You have an OU named AppServers that contains application servers. A Group Policy object (GPO) named GP1 is linked to the Marketing OU. A GPO named GP2 is linked to the AppServers OU. You install Windows Defender on Nano1.
End of repeated scenario
You need to disable SMB 1.0 on Server2. What should you do?
- A. From File Server Resource Manager, create a classification rule.
- B. From the properties of each network adapter on Server2. modify the bindings.
- C. From Windows PowerShell, run the Set -SmbClientConfiguration cmdlet.
- D. From Server Manager, remove a Windows feature.
Answer: D
Explanation: https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1-smbv2-andsmbv3- inwindows-and-windows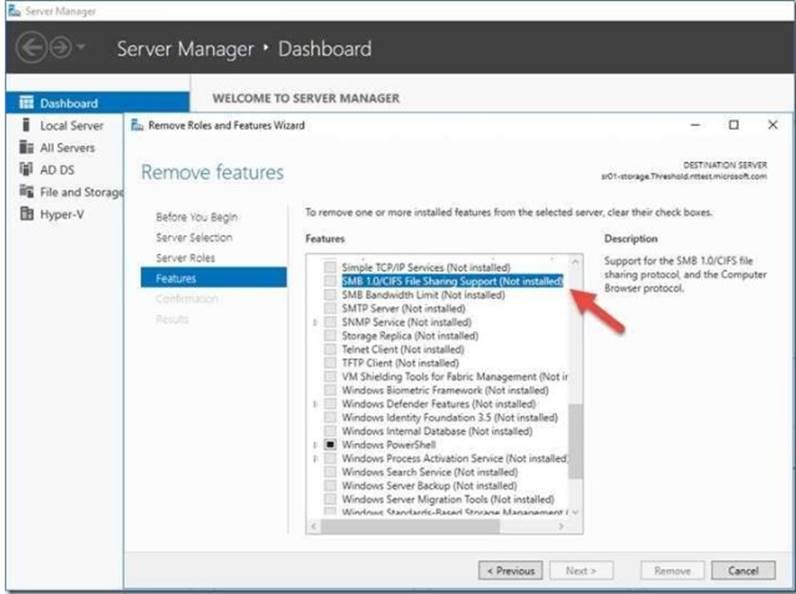
NEW QUESTION 15
You have a server named Server1 that runs Windows Server 2021.
You need to identify whether ICMP traffic is exempt from IPsec on Server1. Which cmdlet should you use?
- A. Get-NetIPSecRule
- B. Get-NetFirewallRule
- C. Get-NetFirewallProfile
- D. Get-NetFirewallSetting
- E. Get-NetFirewallPortFilter
- F. Get-NetFirewallAddressFilter
- G. Get-NetFirewallSecurityFilter
- H. Get-NetFirewallApplicationFilter
Answer: D
Explanation: The Get-NetFirewallSetting cmdlet retrieves the global firewall settings of the target computer. The NetFirewallSetting object specifies properties that apply to the firewall and IPsec settings, no matter which
network profile is currently in use.
The global configurations include viewing the active profile, exemptions, specified certification validation levels, and user and computer authorization lists.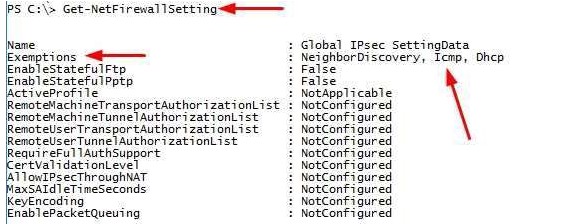
NEW QUESTION 16
You have a server named Server1 that runs Windows Server 2021. You need to view all of the inbound rules on Server1.
Which cmdlet should you use?
- A. Get-NetIPSecRule
- B. Get-NetFirewallRule
- C. Get-NetFirewallProfile
- D. Get-NetFirewallSetting
- E. Get-NetFirewallPortFilter
- F. Get-NetFirewallAddressFilter
- G. Get-NetFirewallSecurityFilter
- H. Get-NetFirewallApplicationFilter
Answer: B
Explanation: Get-NetFirewallRule -Direction Inbound <— view inbound rules for all profiles The following examples shows inbound rule for specific firewall profile.
Get-NetFirewallRule -Direction Inbound | where {$_.Profile -eq “Domain”} Get-NetFirewallRule -Direction Inbound | where {$_.Profile -eq “Public”} Get-NetFirewallRule -Direction Inbound | where {$_.Profile -eq “Private”}
NEW QUESTION 17
Your network contains an Active Directory domain named contoso.com. The domain contains five servers. All servers run Windows Server 2021.
A new secunty policy states that you must modify the infrastructure to meet the following requirements:
*Limit the nghts of administrators.
*Minimize the attack surface of the forest
*Support Multi-Factor authentication for administrators.
You need to recommend a solution that meets the new secunty policy requirements. What should you recommend deploying?
- A. an administrative forest
- B. domain isolation
- C. an administrative domain in contoso.com
- D. the Local Administrator Password Solution (LAPS)
Answer: A
Explanation: You have to “-Minimize the attack surface of the forest”, then you must create another forest for administrators.
https://docs.microsoft.com/en-us/windows-server/identity/securing-privileged-access/securingprivilegedaccess- reference-material#ESAE_BM
This section contains an approach for an administrative forest based on the Enhanced Security Administrative
Environment (ESAE) reference architecture deployed
by Microsoft’s cybersecurity professional services teams to protect customers against cybersecurity attacks.
Dedicated administrative forests allow organizations to host administrative accounts, workstations, and groups in an environment that has stronger security controls than the production environment.
P.S. Easily pass 70-744 Exam with 176 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy 70-744 Dumps: https://www.2passeasy.com/dumps/70-744/ (176 New Questions)
- Top Quality MCSE 70-464 exam
- High quality AZ-100 Exam Dumps 2021
- Microsoft MB2-712 Exam Questions 2021
- Microsoft AZ-301 Exam Questions and Answers 2021
- The Rebirth Guide To SC-900 Free Exam
- Microsoft 70-333 Free Practice Questions 2021
- A Review Of Pinpoint AZ-304 Prep
- Microsoft 70-765 Dumps 2021
- Improved 70-533 Exam Study Guides With New Update Exam Questions
- What Downloadable PL-100 Exam Question Is


