70-744 Exam Questions - Online Test
70-744 Premium VCE File

150 Lectures, 20 Hours
It is more faster and easier to pass the by using . Immediate access to the and find the same core area with professionally verified answers, then PASS your exam with a high score now.
Online 70-744 free questions and answers of New Version:
NEW QUESTION 1
You plan to enable Credential Guard on four servers. Credential Guard secrets will be bound to the TPM.
The servers run Windows Server 2021 and are configured as shown in the following table.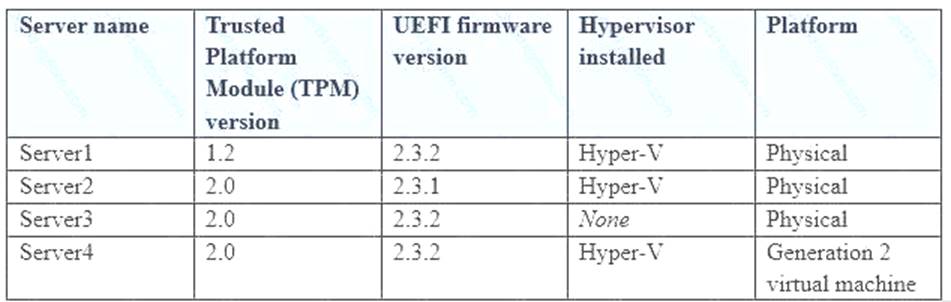
You need to identify which server you must modify to support the planned implementation. Which server should you identify?
- A. Server1
- B. Server2
- C. Server3
- D. Server4
Answer: D
Explanation: References:
https://docs.microsoft.com/en-us/windows/access-protection/credential-guard/credentialguardrequirements
NEW QUESTION 2
You have a guarded fabric and a Host Guardian Service server named HGS1.
You deploy a Hyper-V host named Hyper1, and configure Hyper1 as part of the guarded fabric. You plan to deploy the first shielded virtual machine. You need to ensure that you can run the virtual machine on Hyper1.
What should you do?
- A. On Hyper1, run the Invoke-WebRequest cmdlet, and then run the Import-HgsGuardian cmdlet.
- B. On HGS1, run the Invoke-WebRequest cmdlet, and then run the Import-HgsGuardian cmdlet.
- C. On Hyper1, run the Export-HgsKeyProtectionState cmdlet, and then run the Import-HgsGuardian cmdlet.
- D. On HGS1, run the Export-HgsKeyProtectionState cmdlet, and then run the Import-HgsGuardian cmdlet
Answer: A
Explanation: https://blogs.technet.microsoft.com/datacentersecurity/2021/06/06/step-by-step-creating-shieldedvms- withoutvmm/
The first step is to get the HGS guardian metadata from the HGS server, and use it to create the Key protector.
To do this, run the following PowerShell command
on a guarded host or any machine that can reach the HGS server:
Invoke-WebRequest http://<HGSServer”>FQDN>/KeyProtection/service/metadata/2014- 07/metadata.xml –
OutFile C:\HGSGuardian.xml Shield the VM
Each shielded VM has a Key Protector which contains one owner guardian, and one or more HGS guardians.
The steps below illustrate the process of getting the guardians, create the Key Protector in order to shield the VM.
Run the following cmdlets on a tenant host “Hyper1”:
# SVM is the VM name which to be shielded
$VMName = ‘SVM’
# Turn off the VM first. You can only shield a VM when it is powered off Stop-VM –VMName $VMName
# Create an owner self-signed certificate
$Owner = New-HgsGuardian –Name ‘Owner’ –GenerateCertificates
# Import the HGS guardian
$Guardian = Import-HgsGuardian -Path ‘C:\HGSGuardian.xml’ -Name ‘TestFabric’ – AllowUntrustedRoot
# Create a Key Protector, which defines which fabric is allowed to run this shielded VM
$KP = New-HgsKeyProtector -Owner $Owner -Guardian $Guardian -AllowUntrustedRoot
# Enable shielding on the VM
Set-VMKeyProtector –VMName $VMName –KeyProtector $KP.RawData
# Set the security policy of the VM to be shielded
Set-VMSecurityPolicy -VMName $VMName -Shielded $true
# Enable vTPM on the VM
Enable-VMTPM -VMName $VMName
NEW QUESTION 3
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1.
On Server1, administrators plan to use several scripts that have the .ps1 extension.
You need to ensure that when code is generated from the scripts, an event containing the details of
the code is logged in the Operational log.
Which Group Policy setting or settings should you configure?
- A. Enable Protected Event Logging
- B. Audit Process Creation and Audit Process Termination
- C. Turn on PovverShell Script Block Logging
- D. Turn on PowerShell Transcription
Answer: C
Explanation: https://docs.microsoft.com/en-us/powershell/wmf/5.0/audit_script
The new Detailed Script Tracing feature lets you enable detailed tracking and analysis of Windows PowerShell scripting use on a system.
After you enable detailed script tracing, Windows PowerShell logs all script blocks to the ETW event log,
Microsoft-Windows-PowerShell/Operational.
If a script block creates another script block (for example, a script that calls the Invoke-Expression cmdlet on a string), that resulting script block is logged as well.
Logging of these events can be enabled through the Turn on PowerShell Script Block Logging Group Policy setting (in GPO Administrative Templates -> Windows Components -> Windows PowerShell).
Answer D is incorrect, since Transcription (Start-Transcript -path <FilePath>) uses a custom output location
instead of Event Viewer \ Operational Log
NEW QUESTION 4
Your network contains an Active Directory domain named contoso.com. The domain contains two
servers named Server1 and Server2 that run Windows Server 2021. Server1 is configured as a domain controller.
You configure Server1 as a Just Enough Administration (JEA) endpoint You configure the required JEA rights for a user named User1.
You need to tell User1 how to manage Active Directory objects from Server2. What should you tell User1 to do first on Server2?
- A. From a command prompt, run ntdsutil.exe.
- B. From Windows PowerShell, run the Import-Module cmdlet.
- C. From Windows PowerShell run the Enter-PSSession cmdlet.
- D. Install the management consoles for Active Directory, and then launch Active Directory Users and Computer.
Answer: C
Explanation: References:
https://blogs.technet.microsoft.com/privatecloud/2014/05/14/just-enough-administration-step-bystep/
NEW QUESTION 5
Your network contains an Active Directory domain named contoso.com. All client computers run Windows 10.
You plan to deploy a Remote Desktop connection solution for the client computers.
You have four available servers in the domain that can be configured as Remote Desktop servers. The servers are configured as shown in the following table.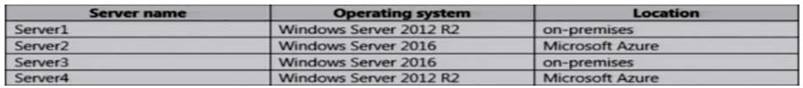
You need to ensure that all Remote Desktop connections can be protected by using Remote Credential Guard.
Solution: You deploy the Remote Desktop connection solution by using Server4. Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation: No, as Server4 is a Windows Server 2012R2 which does not meet the requirements of Remote Credential
Guard.
https://docs.microsoft.com/en-us/windows/access-protection/remote-credential-guard Remote Credential Guard requirements
To use Windows Defender Remote Credential Guard, the Remote Desktop client and remote host must meet the following requirements:
The Remote Desktop client device:
Must be running at least Windows 10, version 1703 to be able to supply credentials.
Must be running at least Windows 10, version 1607 or Windows Server 2021 to use the user’s signed-in
credentials. This requires the user’s account be able to sign in to both the client device and the remote host.
Must be running the Remote Desktop Classic Windows application. The Remote Desktop Universal Windows Platform application doesn’t support Windows Defender Remote Credential Guard.
Must use Kerberos authentication to connect to the remote host. If the client cannot connect to a domain
controller, then RDP attempts to fall back to NTLM.
Windows Defender Remote Credential Guard does not allow NTLM fallback because this would expose
credentials to risk.
The Remote Desktop remote host:
Must be running at least Windows 10, version 1607 or Windows Server 2021. Must allow Restricted Admin connections.
Must allow the client’s domain user to access Remote Desktop connections. Must allow delegation of non-exportable credentials.
NEW QUESTION 6
Your data center contains 10 Hyper-V hosts that host 100 virtual machines.
You plan to secure access to the virtual machines by using the Datacenter Firewall service.
You have four servers available for the Datacenter Firewall service. The servers are configured as shown in the following table.
You need to install the required server roles for the planned deployment Which server role should you deploy? Choose Two.
- A. Server role to deploy: Multipoint Services
- B. Server role to deploy: Network Controller
- C. Server role to deploy: Network Policy and Access Services
- D. Servers on which to deploy the server role: Server20 and Server21
- E. Servers on which to deploy the server role: Server22 and Server23
Answer: BE
Explanation: Datacenter Firewall is a new service included with Windows Server 2021. It is a network layer, 5- tuple (protocol, source and destination port numbers, source and destination IP addresses), stateful, multitenant firewall. When deployed and offered as a service by the serviceprovider, tenant administrators can install and configure firewall policies to help protect their virtual networks from unwanted traffic originating from Internet and intranet networks.
https://docs.microsoft.com/en-us/windows-server/networking/sdn/technologies/networkcontroller/ networkcontroller
Network Controller Features
The following Network Controller features allow you to configure and manage virtual and physical network
devices and services.
i) Firewall Management (Datacenter Firewall)
ii) Software Load Balancer Management
iii) Virtual Network Management
iv) RAS Gateway Management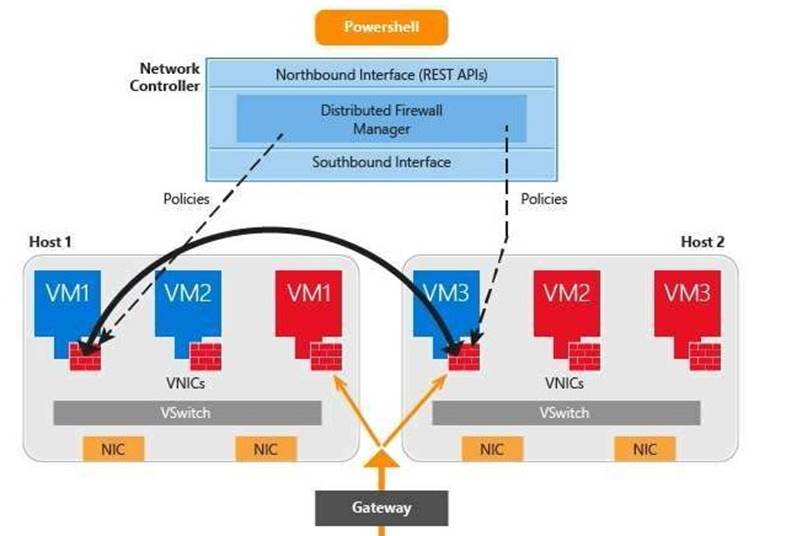
https://docs.microsoft.com/en-us/windows-server/networking/sdn/plan/installation-andpreparationrequirements- for-deploying-network-controller
Installation requirements
Following are the installation requirements for Network Controller.
For Windows Server 2021 deployments, you can deploy Network Controller on one or more computers, one or more VMs, or a combination of computers and VMs.
All VMs and computers planned as Network Controller nodes must be running Windows Server 2021 Datacenter edition.
NEW QUESTION 7
Your network contains an Active Directory domain named contoso.com. The domain contains a certification authority (CA).
You need to implement code integrity policies and sign them by using certificates issued by the CA. You plan to use the same certificate to sign policies on multiple computers.
You duplicate the Code Signing certificate template and name the new template CodeIntegrity. How should you configure the CodeIntegrity template?
- A. Enable the Allow private key to be exported setting and modify the Key Usage extension.
- B. Disable the Allow private key to be exported setting and modify the Application Policies extension.
- C. Disable the Allow private key to be exported setting and disable the Basic Constraints extension.
- D. Enable the Allow private key to be exported setting and enable the Basic Constraints extension
Answer: D
NEW QUESTION 8
Your network contains an Active Directory domain named contoso.com.The domain contains 1,000 client computers that run either Windows 8.1 or Windows 10.
You have a Windows Server Update Services (WSUS) deployment All client computers receive updates from WSUS.
You deploy a new WSUS server named WSUS2.
You need to configure all of the client computers that run Windows 10 to send WSUS reporting data to WSUS2.
What should you configure?
- A. an approval rule
- B. a computer group
- C. a Group Policy object (GPO)
- D. a synchronization rule
Answer: C
Explanation: https://technet.microsoft.com/en-us/library/cc708574(v=ws.10).aspx
Under “Set the intranet update service for detecting updates”, type http://wsus:8530 Under “Set the intranet statistics server”, type http://wsus2:8531
NEW QUESTION 9
Your network contains an Active Directory domain named contoso.com. The functional level of the forest and the domain is Windows Server 2008 R2. The domain contains the servers configured as shown in the following table.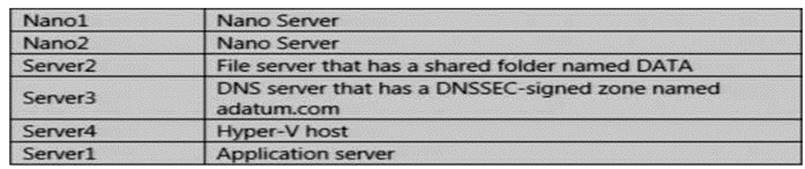
You have an organizational unit (OU) named Marketing that contains the computers in the marketing department.
You have an OU named Finance that contains the computers in the finance department. You have an OU named AppServers that contains application servers.
A Group Policy object (GPO) named GP1 is linked to the Marketing OU. A GPO named GP2 is linked to the
AppServers OU.
You install Windows Defender on Nano1.
You need to configure Nano1 as a Hyper-V Host. Which command should you run?
- A. Add-WindowsFeature Microsoft-NanoServer-Compute-Package
- B. Add-WindowsFeature Microsoft-NanoServer-Guest-Package
- C. Add-WindowsFeature Microsoft-NanoServer-Host-Package
- D. Add-WindowsFeature Microsoft-NanoServer-ShieldedVM-Package
- E. Install-Package Microsoft-NanoServer-Compute-Package
- F. Install-Package Microsoft-NanoServer-Guest-Package
- G. Install-Package Microsoft-NanoServer-Host-Package
- H. Install-Package Microsoft-NanoServer-ShieldedVM-Package
- I. Install-WindowsFeature Microsoft-NanoServer-Compute-Package
- J. Install-WindowsFeatureMicrosoft-NanoServer-Guest-Package
- K. Install-WindowsFeatureMicrosoft-NanoServer-Host-Package
- L. Install-WindowsFeature Microsoft-NanoServer-ShieldedVM-Package
Answer: E
Explanation: https://docs.microsoft.com/en-us/windows-server/get-started/deploy-nano-server#BKMK_online The Nano Server package “Microsoft-NanoServer-Compute-Package” includes the Hyper-V role for a Nano
Server host.
Moreover, the Install-WindowsFeature or Add-WindowsFeature cmdlet are NOT available on a Nano Server.
NEW QUESTION 10
Your network contains an Active Directory domain named contoso.com.
The domain contains two global groups named Group1 and Group2. A user named User1 is a member of Group1
You have an organizational unit (OU) named OU1 that contains the computer accounts of computers that contain sensitive data. A Group Policy object (GPO) named GPO1 is linked to OU1. OU1 contains a computer account named Computer1.
GPO1 has the User Rights Assignment configured as shown in the following table.
You need to prevent User1 from signing in to Computer1. What should you do?
- A. From Default Domain Policy, modify the Allow log on locally user right
- B. On Computer1, modify the Deny log on locally user right.
- C. From Default Domain Policy, modify the Deny log on locally user right
- D. Remove User1 to Group2.
Answer: D
Explanation: https://technet.microsoft.com/en-us/library/cc957048.aspx “Deny log on locally”
Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment
Determines which users are prevented from logging on at the computer.
This policy setting supercedes the Allow Log on locally policy setting if an account is subject to both policies.
Therefore, adding User1 to Group2 will let User1 to inherit both policy, and then prevent User1 to sign in to
Computer1.
NEW QUESTION 11
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this sections, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You manage a file server that runs Windows Server 2021. The file server contains the volumes configured as shown in the following table.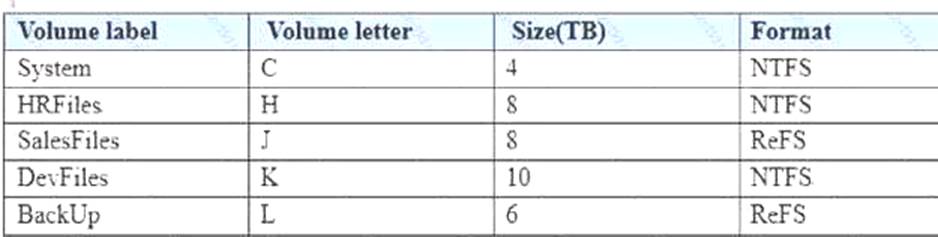
You need to encrypt DevFiles by using BitLocker Drive Encryption (ButLocker). Solution: You run the Lock-BitLocker cmdlet.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
References:
https://docs.microsoft.com/en-us/powershell/module/bitlocker/lock-bitlocker?view=win10-ps
NEW QUESTION 12
The network contains an Active Directory domain named contoso.com. The domain contains the servers configured as shown in the following table.
All servers run Windows Server 2021. All client computers run Windows 10 and are domain members.
All laptops are protected by using BitLocker Drive Encryption (BitLocker).
You have an organizational unit (OU) named OU1 that contains the computer accounts of application servers.
An OU named OU2 contains the computer accounts of the computers in the marketing department. A Group Policy object (GPO) named GP1 is linked to OU1.
A GPO named GP2 is linked to OU2.
All computers receive updates from Server1. You create an update rule named Update1.
You enable deep script block logging for Windows PowerShell.
In which event log will PowerShell code that is generated dynamically appear?
- A. Applications and Services Logs/Microsoft/Windows/PowerShell/Operational
- B. Windows Logs/Security
- C. Applications and Services Logs/Windows PowerShell
- D. Windows Logs/Application
Answer: A
Explanation: https://docs.microsoft.com/en-us/powershell/wmf/5.0/audit_script
While Windows PowerShell already has the LogPipelineExecutionDetails Group Policy setting to log the
invocation of cmdlets, PowerShell’s scripting language has plenty of features that you might want to log and/or audit.
The new Detailed Script Tracing feature lets you enable detailed tracking and analysis of Windows PowerShell scripting use on a system.
After you enable detailed script tracing, Windows PowerShell logs all script blocks to the ETW (event tracing for windows) event log – Microsoft-WindowsPowerShell/Operational.
If a script block creates another script block (for example, a script that calls the Invoke-Expression cmdlet on a string), that resulting script block is logged as well.
Logging of these events can be enabled through the Turn on PowerShell Script Block Logging Group Policy
setting (in Administrative Templates -> Windows Components -> Windows PowerShell).
NEW QUESTION 13
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2021.
A user named User1 is a member of the local Administrators group.
Server1 has the AppLocker rules configured as shown in the exhibit. (Click the Exhibit button.) Exhibit: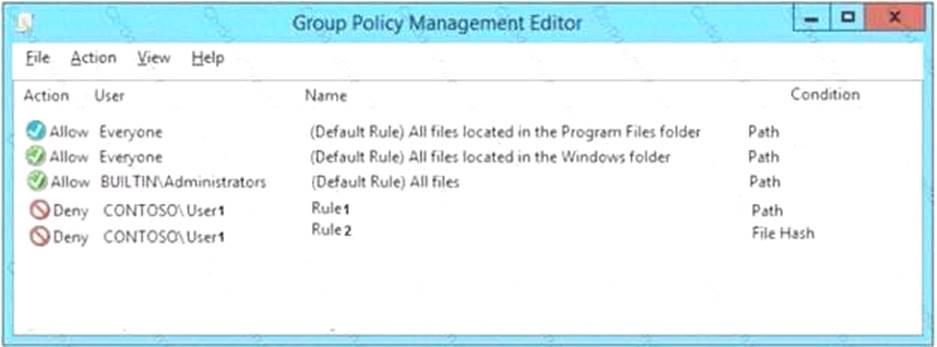
Rule1 and Rule2 are configured as shown in the following table.
You verify that User1 is unable to run App2.exe on Server1.
Which changes will allow User1 to run D:Folder1Program.exe and D:Folder2App2.exe? To answer select the appropriate options in the answer area.
Answer:
Explanation: References:
https://technet.microsoft.com/en-us/library/ee449492(v=ws.11).aspx
NEW QUESTION 14
You implement Log Analytics in Microsoft Operations Management Suite (OMS) on all servers that run Windows Server 2021.
You need to generate a daily report that identifies which servers restarted during the last 24 hours. Which query should you use?
- A. EventLog=Application EventId:6009 Type:Event TimeGenerated>NOW+24HOURS
- B. EventLog=Application EventId:6009 Type:Event TimeGenerated>NOW-24HOURS
- C. EventLog=System EventId:6009 Type:Event TimeGenerated>NOW-24HOURS
- D. EventLog=System EventId:6009 Type:Event TimeGenerated>NOW+24HOURS
Answer: C
Explanation: https://docs.microsoft.com/en-us/azure/log-analytics/log-analytics-log-searches Computer restart events are stored in “System” eventlog instead of Application even log. “NOW-24HOURS” clause matches all events generated in the last 24 hours.
NEW QUESTION 15
You implement Just Enough Administration (JEA) on several file servers that run Windows Server 2021.
The Role Capability file from a server named Server5 contains the following code.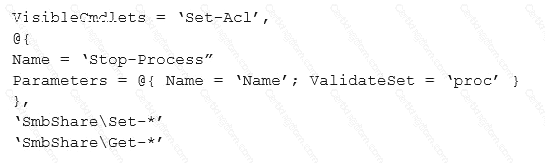
Which action can be performed by a user who connects to Server5?
- A. Create a new file share.
- B. Modify the properties of any share.
- C. Stop any process.
- D. View the NTFS permissions of any folder.
Answer: B
Explanation: https://docs.microsoft.com/en-us/powershell/jea/role-capabilities Focus on the 3rd Visible Cmdlets in this question ‘SmbShare\Set-*’
The PowerShell “SmbShare” module has the following “Set-*” cmdlets, as reported by “Get- Command -Module
SmbShare” command:-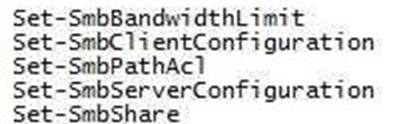
The “Set-SmbShare” cmdlet is then visible on Server5’s JEA endpoint, and allows JEA users to modify the
properties of any file share.
https://technet.microsoft.com/en-us/itpro/powershell/windows/smbshare/set-smbshare
NEW QUESTION 16
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2021. A user named User1 is a member of the local Administrators group. Server1 has the AppLocker rules
configured as shown in follow:
Rule1 and Rule2 are configured as shown in the following table: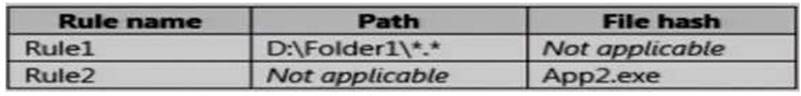
You verify that User1 is unable to run App2.exe on Server1.
Which changes will allow User1 to run D:\Folder1\Program.exe and D:\Folder2\App2.exe? Choose Two.
- A. User1 can run D:\Folder1\Program.exe if Program.exe is moved to another folder
- B. User1 can run D:\Folder1\Program.exe if Program.exe is renamed
- C. User1 can run D:\Folder1\Program.exe if Program.exe is updated
- D. User1 can run D:\Folder2\App2.exe if App2.exe is moved to another folder
- E. User1 can run D:\Folder2\App2.exe if App2.exe is renamed
- F. User1 can run D:\Folder2\App2.exe if App2.exe is upgraded
Answer: AF
Explanation: https://technet.microsoft.com/en-us/library/ee449492(v=ws.11).aspx
For “D:\Folder1\Program.exe”, it is originally explicitly denied due to Rule1, when moving the “Program,exe” out of “D:\Folder1\”, it does not match Rule1.
Assume that “Program.exe” is moved to “D:\Folder2”, it matches an Explicit Allow rule for group “BUILTIN
\Administrators” which User1 is a member of, therefore A is correct.
For “App2”,exe, it matches a Explicit Deny rule using its File Hash (created File content), no matter where you move it to, or how you rename it, it would still match Rule2.
Only changing the file content of App2.exe would let it no longer match the explicit deny hash-based rule
“Rule2”.
By upgrading its version and content, it will generate a new hash. so F is correct.
NEW QUESTION 17
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this sections, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2021.
You need to prevent NTLM authentication on Server1.
Solution: From a Group Policy, you configure the Kerberos Policy. Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
References:
https://www.rootusers.com/implement-ntlm-blocking-in-windows-server-2021/
P.S. Easily pass 70-744 Exam with 176 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam 70-744 Dumps: https://www.surepassexam.com/70-744-exam-dumps.html (176 New Questions)
- What Printable MS-203 Dumps Questions Is
- 10 Tips For Far out 70-410 exam dumps
- How Many Questions Of MS-721 Test Questions
- Microsoft 70-333 Braindumps 2021
- Breathing 70-341 Exam Questions 2021
- All About Actual 70-488 braindumps
- Top Quality 70-640 Study Guides 2021
- What Refined 70-499 dumps Is?
- Microsoft 70-735 Braindumps 2021
- Precise Microsoft 70-499 exam


