70-744 Exam Questions - Online Test
70-744 Premium VCE File

150 Lectures, 20 Hours
We provide in two formats. Download PDF & Practice Tests. Pass Microsoft 70-744 Exam quickly & easily. The 70-744 PDF type is available for reading and printing. You can print more and practice many times. With the help of our product and material, you can easily pass the 70-744 exam.
Also have 70-744 free dumps questions for you:
NEW QUESTION 1
Your company has an accounting department.
The network contains an Active Directory domain named contoso.com. The domain contains 10 servers.
You deploy a new server named Server11 that runs Windows Server 2021.
Server11 will host several network applications and network shares used by the accounting department.
You need to recommend a solution for Server11 that meets the following requirements:
-Protects Server11 from address spoofing and session hijacking
-Allows only the computers in We accounting department to connect to Server11 What should you recommend implementing?
- A. AppLocker rules
- B. Just Enough Administration (JEA)
- C. connection security rules
- D. Privileged Access Management (PAM)
Answer: C
Explanation: In IPsec connection security rule, the IPsec protocol verifies the sending host IP address by utilize integrity
functions like Digitally signing all packets.
If unsigned packets arrives Server11, those are possible source address spoofed packets, when using connection security rule in-conjunction with inbound firewall
rules, you can kill those un-signed packets with the action “Allow connection if it is secure” to prevent spoofing and session hijacking attacks.
NEW QUESTION 2
HOTSPOT
The network contains an Active Directory domain named contoso.com. The domain contains the servers configured as shown in the following table.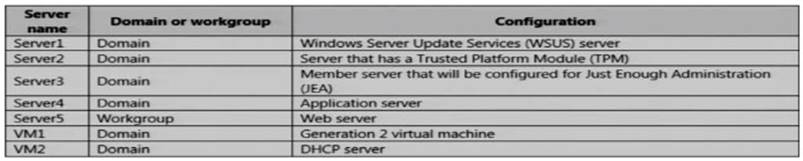
All servers run Windows Server 2021. All client computers run Windows 10 and are domain members.
All laptops are protected by using BitLocker Drive Encryption (BitLocker).You have an organizational unit (OU) named OU1 that contains the computer accounts of application servers.
An OU named OU2 contains the computer accounts of the computers in the marketing department. A Group Policy object (GPO) named GP1 is linked to OU1.
A GPO named GP2 is linked to OU2.
All computers receive updates from Server1. You create an update rule named Update1.
You need to create an Encrypting File System (EFS) data recovery certificate and then add the certificate as an EFS data recovery agent on Server5.
What should you use on Server5? To answer, select the appropriate options in the answer area.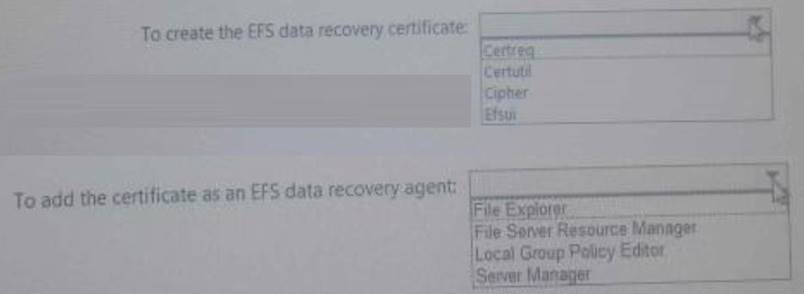
Answer:
Explanation: https://docs.microsoft.com/en-us/windows/threat-protection/windows-informationprotection/ create-and-verifyan-efs-dra-certificatecipher /R
NEW QUESTION 3
Your network contains an Active Directory domain named contoso.com The domain contains five file servers that run Windows Server 2021.
You have an organizational unit (OU) named Finance that contains all of the servers. You create a Group Policy object (GPO) and link the GPO to the Finance OU.
You need to ensure that when a user in the finance department deletes a file from a file server, the event is logged. The solution must log only users who have a manager attribute of Ben Smith. Which audit policy setting should you configure in the GPO?
- A. File system in Global Object Access Auditing
- B. Audit Detailed File Share
- C. Audit Other Account Logon Events
- D. Audit File System in Object Access
Answer: C
NEW QUESTION 4
Note: Thb question Is part of a series of questions that present the same scenario. Each question In the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you willNOTbeabletorrturntoit.Asa result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com. The domain contains multiple Hyper-V hosts.
You need to deploy several critical line-of-business applications to the network to meet the following requirements:
*The resources of the applications must be isolated from the physical host
*Each application must be prevented from accessing the resources of the other applications.
*The configurations of the applications must be accessible only from the operating system that hosts the application.
Solution: You deploy one Windows container to host all of the applications. Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation: References:
https://docs.microsoft.com/en-us/virtualization/windowscontainers/about/
NEW QUESTION 5
Note: This question is part of a series of questions that use the same or similar answer choices. An answer choice may be correct for more than one question in the series. Each question Is independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains an Active Directory domain named contoso.com The domain contains a file server named Server1 that runs Windows Server 2021.
You need to create Work Folders on Server1. Which tool should you use?
- A. File Explorer
- B. Shared Folders
- C. Server Manager
- D. Disk Management
- E. Storage Explorer
- F. Computer Management
- G. System Configuration
- H. File Server Resource Manager (FSRM)
Answer: C
NEW QUESTION 6
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2021. You need to prevent NTLM authentication on Server1.
Solution: From Windows PowerShell, you run the New-ADAuthenticationPolicy cmdlet. Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation: ADDS Authentication Policy does not provide ability to prevent the use of NTLM authentication.
NEW QUESTION 7
Note: This question is port of a series of questions that use the same or similar answer choices. An answer choice may be correct for more than one question In the series. Each question is Independent of the other questions In this series. Information and details provided in a question apply only to that question.
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2021 and a Nano Server named Nano1. Nano1 has two volumes named C and D.
You are signed in to Server1.
You need to configure Data Deduplication on Nano1. Which tool should you use?
- A. File Explorer
- B. Shared Folders
- C. Server Manager
- D. Disk Management
- E. Storage Explorer
- F. Computer Management
- G. System Configuration
- H. File Server Resource Manager (FSRM)
Answer: C
Explanation: Either use PowerShell Remoting to Nano1 and use “Enable-DedupVolume” cmdlet, however ,there is no such choice for this question; or
From Server1, connect it’s server manager to remotely manage Nano1 and enable Data Deduplication for
volumes on Nano1
https://channel9.msdn.com/Series/Nano-Server-Team/Server-Manager-managing-Nano-Server
NEW QUESTION 8
Your network contains an Active Directory domain named contoso.com. The domain contains multiple servers that run multiple applications.
Domain user accounts are used to authenticate access requests to the servers. You plan to prevent NTLM from being used to authenticate to the servers. You start to audit NTLM authentication events for the domain.
You need to view all of the NTLM authentication events and to identify which applications authenticate by using NTLM.
On which computers should you review the event logs and which logs should you review?
- A. Computers on which to review the event logs: Only client computers
- B. Computers on which to review the event logs: Only domain controllers
- C. Computers on which to review the event logs: Only member servers
- D. Event logs to review: Applications and Services Logs\Microsoft\Windows\Diagnostics- Networking\Operational
- E. Event logs to review: Applications and Services Logs\Microsoft\Windows\NTLM\Operational
- F. Event logs to review: Applications and Services Logs\Microsoft\Windows\SMBClient\Security
- G. Event logs to review: Windows Logs\Security
- H. Event logs to review: Windows Logs\System
Answer: AE
Explanation: Do not confuse this with event ID 4776 recorded on domain controller’s security event log!!!
This question asks for implementing NTLM auditing when domain clients is connecting to member servers! See below for further information.
https://docs.microsoft.com/en-us/windows/device-security/security-policy-settings/networksecurity- restrict-ntlmaudit-ntlm-authentication-in-this-domain
Via lab testing, most of the NTLM audit logs are created on Windows 10 clients, except that you use Windows
Server 2021 OS as clients (but this is unusual)
NEW QUESTION 9
Note: This question Is part of a series of questions that use the same or similar answer choices. An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2021.
Server1 has a volume named Volume1.
A central access policy named Policy1 is deployed to the domain. You need to apply Policy1 to Volume1.
Which tool should you use?
- A. File Explorer
- B. Shared Folders
- C. Server Manager
- D. Disk Management
- E. Storage Explorer
- F. Computer Management
- G. System Configuration
- H. File Server Resource Manager (FSRM)
Answer: A
Explanation:
“File Explorer” = “Windows Explorer”.
https://docs.microsoft.com/en-us/windows-server/identity/solution-guides/deploy-a-centralaccess- policy–
demonstration-steps-#BKMK_1.4
NEW QUESTION 10
You have a Hyper-V host named Server1 that runs Windows Server 2021. Server1 hosts the virtual machines configured as shown in the following table.
All the virtual machines have two volumes named C and D.
You plan to implement BitLocker Drive Encryption (BitLocker) on the virtual machines. Which virtual machines can have their volumes protected by using BitLocker? Choose Two.
- A. Virtual machines that can have volume C protected by using BitLocker and a Trusted Platform Module (TPM) protector: VM3 only
- B. Virtual machines that can have volume C protected by using BitLocker and a Trusted Platform Module (TPM) protector: VM1 and VM3 only
- C. Virtual machines that can have volume C protected by using BitLocker and a Trusted Platform Module (TPM) protector: VM2 and VM3 only
- D. Virtual machines that can have volume C protected by using BitLocker and a Trusted Platform Module (TPM) protector: VM2 and VM4 only
- E. Virtual machines that can have volume C protected by using BitLocker and a Trusted Platform Module (TPM) protector: VM2, VM3 and VM4 only
- F. Virtual machines that can have volume C protected by using BitLocker and a Trusted Platform Module (TPM) protector: VM1, VM2, VM3 and VM4
- G. Virtual machines that can have volume D protected by using BitLocker: VM3 only
- H. Virtual machines that can have volume D protected by using BitLocker: VM1 and VM3 only
- I. Virtual machines that can have volume D protected by using BitLocker: VM2 and VM3 only
- J. Virtual machines that can have volume D protected by using BitLocker: VM2 and VM4 only
- K. Virtual machines that can have volume D protected by using BitLocker: VM2, VM3 and VM4 only
- L. Virtual machines that can have volume D protected by using BitLocker: VM1, VM2, VM3 and VM4
Answer: AG
Explanation: https://docs.microsoft.com/en-us/windows-server/virtualization/hyper-v/deploy/upgrade-virtualmachine- versionin-hyper-v-on-windows-or-windows-server
To use Virtual TPM protector for encrypting C: drive, you have to use at least VM Configuration Version 7.0 and Generation 2 Virtual machines.
https://www.howtogeek.com/howto/6229/how-to-use-bitlocker-on-drives-without-tpm/
If you don’t use TPM for protecting a drive, there is no such Virtual TPM or VM Generation, or VM Configuration version requirement, you can even use Bitlocker without TPM Protector with earlier versions of Windows.
NEW QUESTION 11
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario
Your network contains an Active Directory domain named contoso.com. The functional level of the forest and the domain is Windows Server 2008 R2.
The domain contains the servers configured as shown in the following table.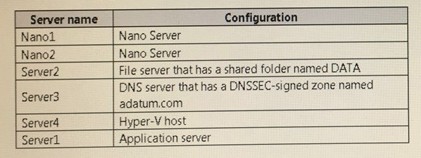
All servers run Windows Server 2021. All client computers run Windows 10.
You have an organizational unit (OU) named Marketing that contains the computers in the marketing department You have an OU named Finance that contains the computers in the finance department You have an OU named AppServers that contains application servers. A Group Policy object (GPO) named GP1 is linked to the Marketing OU. A GPO named GP2 is linked to the AppServers OU. You install Windows Defender on Nano1.
End of repeated scenario
You plan to implement BitLocker Drive Encryption (BitLocker) on the operating system volumes of the application servers.
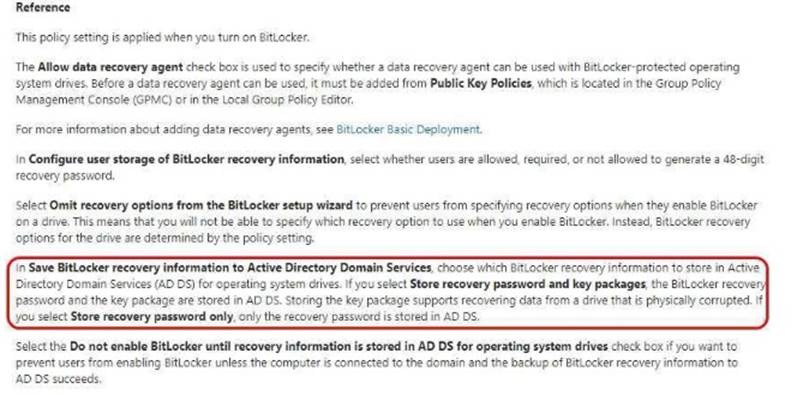
You need to ensure that the BitLocker recovery keys are stored in Active Directory. Which Group Policy setting should you configure?
- A. System cryptography; Force strong key protection (or user keys stored on the computer
- B. Store Bittocker recovery information in Active Directory Domain Services (Windows Server 2008 and Windows Vista)
- C. System cryptography: Use FIPS compliant algorithms for encryption, hashing and signing
- D. Choose how BitLocker-protected operating system drives can be recovered
Answer: D
Explanation: https://technet.microsoft.com/en-us/library/jj679890%28v=ws.11%29.aspx?f=255&MSPPError=- 2147217396#BKMK_rec1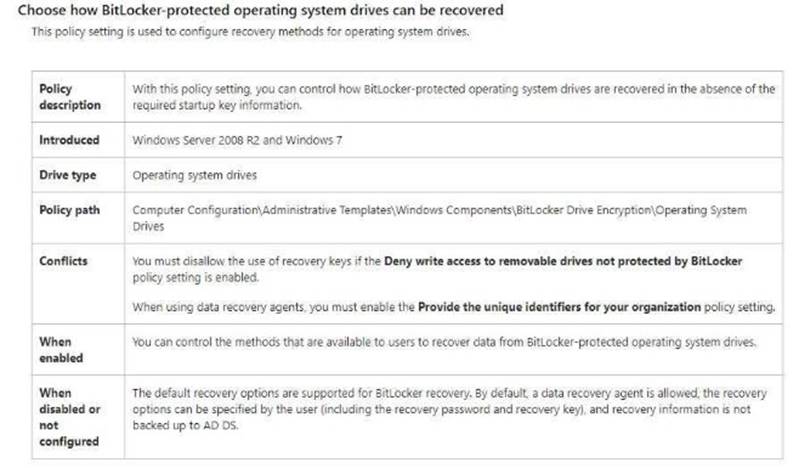
NEW QUESTION 12
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that has Microsoft Security Compliance Manager (SCM) 4.0 installed. The domain contains domain controllers that run Windows Server 2021.
A Group Policy object (GPO) named GPO1 is applied to all of the domain controllers.
GPO1 has a Globally Unique Identifier (GUID) of 7ABCDEFG-1234-5678-90AB-005056123456. You need to create a new baseline that contains the settings from GPO1. What should you do first?
- A. Copy the \\contoso.com\sysvol\contoso.com\Policies\{7ABCDEFG-1234-5678-90AB- 005056123456} folder to Server1.
- B. From Group Policy Management, create a backup of GPO1.
- C. From Windows PowerShell, run the Copy-GPO cmdlet
- D. Modify the permissions of the \\contoso.com\sysvol\contoso.com\Policies\{7ABCDEFG- 1234-5678-90AB-005056123456}
Answer: B
Explanation: https://technet.microsoft.com/en-us/library/hh489604.aspx Import Your GPOs
You can import current settings from your GPOs and compare these to the Microsoft recommended best
practices.
Start with a GPO backup that you would commonly create in the Group Policy Management Console (GPMC).
Take note of the folder to which the backup is saved. In SCM, select GPO Backup, browse to the GPO folder’s Globally Unique Identifier (GUID) and select a name for the GPO when it’s imported.
SCM will preserve any ADM files and GP Preference files (those with non-security settings that SCM doesn’t parse) you’re storing with your GPO backups.
It saves them in a subfolder within the user’s public folder. When you export the baseline as a GPO again, it
also restores all the associated files.
NEW QUESTION 13
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario
Your network contains an Active Directory domain named contoso.com. The functional level of the forest and the domain is Windows Server 2008 R2.
The domain contains the servers configured as shown in the following table.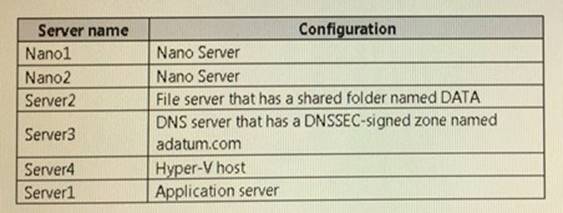
All servers run Windows Server 2021. All client computers run Windows 10.
You have an organizational unit (OU) named Marketing that contains the computers in the marketing department. You have an OU named Finance that contains the computers in the finance department. You have an OU named AppServers that contains application servers. A Group Policy object (GPO) named GP1 is linked to the Marketing OU. A GPO named GP2 is linked to the AppServers OU. You install Windows Defender on Nano1.
End of repeated scenario
You need to ensure that you can deploy a shielded virtual machine to Server4. Which server role should you deploy?
- A. Hyper-V
- B. Device Health Attestation
- C. Network Controller
- D. Host Guardian Service
Answer: D
Explanation: https://blogs.technet.microsoft.com/datacentersecurity/2021/06/06/step-by-step-creating-shieldedvms- withoutvmm/
Shielding an existing VM
Let’s start with the simpler approach. This requires you to have a running VM on a host which is not the
guarded host.
This is important to distinguish, because you are simulating the scenario where a tenant wants to take an
existing, unprotected VM and shield it before moving it to a guarded host.
For clarity, the host machine which is not the guarded host will be referred as the tenant host below. A shielded VM can only run on a trusted guarded host.
The trust is established by the adding the Host Guardian Service server role (retrieved from the HGS server) to the Key Protector which is used to shield
the VM.
That way, the shielded VM can only be started after the guarded host successfully attest against the HGS
server.
In this example, the running VM is named SVM. This VM must be generation 2 and have a supported OS
installed with remote desktop enabled.
You should verify the VM can be connected through RDP first, as it will almost certainly be the primary way to access the VM once it is shielded (unless you have installed other remoting capabilities).
NEW QUESTION 14
Your network contains an Active Directory domain named contoso.com. The domain contains 100 servers.
You deploy the Local Administrator Password Solution (LAPS) to the network You need to view the password of the local administrator of a server named Server5. Which tool should you use?
- A. Active Directory Users and Computers
- B. Computer Management
- C. Accounts from the Settings app
- D. Server Manager
Answer: A
Explanation: Use “Active Directory Users and Computers” to view the attribute value of “ms-MCS-adminpwd” of the Server5 computer account
https://blogs.technet.microsoft.com/askpfeplat/2015/12/28/local-administrator-password-solutionlapsimplementation- hints-and-security-nerd-commentaryincludingmini-threat-model/
NEW QUESTION 15
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2021. You need to prevent NTLM authentication on Server1.
Solution: From a Group Policy, you configure the Security Options. Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 16
You plan to enable Credential Guard on four servers. Credential Guard secrets will be bound to the TPM.
The servers run Windows Server 2021 and are configured as shown in the following table.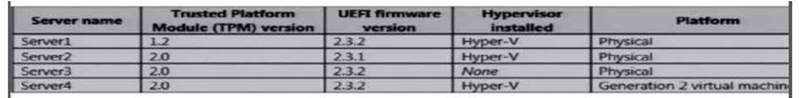
Which of the above server you could enable Credential Guard?
- A. Server1
- B. Server2
- C. Server3
- D. Server4
Answer: D
Explanation: https://docs.microsoft.com/en-us/windows/access-protection/credential-guard/credential-guardrequirements Hardware and software requirements
To provide basic protections against OS level attempts to read Credential Manager domain credentials, NTLM
and Kerberos derived credentials, Windows Defender Credential Guard uses:
-Support for Virtualization-based security (required)
-Secure boot (required)
-TPM 2.0 either discrete or firmware (preferred – provides binding to hardware)-UEFI lock (preferred
– prevents attacker from disabling with a simple registry key change)
NEW QUESTION 17
Your network contains an Active Directory domain named contoso.com.
The domain contains 10 computers that are in an organizational unit (OU) named OU1. You deploy the Local Administrator Password Solution (LAPS) client to the computers.
You link a Group Policy object (GPO) named GPO1 to OU1, and you configure the LAPS password policy
settings in GPO1.
You need to ensure that the administrator passwords on the computers in OU1 are managed by using LAPS.
Which two actions should you perform? Each correct answer presents part of the solution.
- A. Restart the domain controller that hosts the PDC emulator role.
- B. Update the Active Directory Schema.
- C. Enable LDAP encryption on the domain controllers.
- D. Restart the computers.
- E. Modify the permissions on OU1.
Answer: BE
P.S. Surepassexam now are offering 100% pass ensure 70-744 dumps! All 70-744 exam questions have been updated with correct answers: https://www.surepassexam.com/70-744-exam-dumps.html (176 New Questions)
- Microsoft MB2-712 Study Guides 2021
- A Review Of Free 70-533 exam dumps
- 10 Tips For Rebirth 70-534 exam
- Certified AZ-102 Braindumps 2021
- Up To Date PL-900 Software 2021
- How Many Questions Of MS-721 Test Questions
- What Free 701-100 Pdf Is
- Microsoft 70-742 Dumps 2021
- Validated 70-742 Braindumps 2021
- Up To The Immediate Present MS-721 Pdf Exam For Collaboration Communications Systems Engineer Certification


