70-744 Exam Questions - Online Test
70-744 Premium VCE File

150 Lectures, 20 Hours
Want to know features? Want to lear more about experience? Study . Gat a success with an absolute guarantee to pass Microsoft 70-744 (Securing Windows Server 2021) test on your first attempt.
Free 70-744 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
You are building a guarded fabric. You need to configure Admin-trusted attestation. Which cmdlet should you use?
- A. Add-HgsAttestationHostGroup
- B. Add-HgsAttestationTpmHost
- C. Add-HgsAttestationCIPolicy
- D. Add-HgsAttestationTpmPolicy
Answer: A
Explanation: Authorize Hyper-V hosts using Admin-trusted attestation
https://docs.microsoft.com/en-us/windows-server/virtualization/guarded-fabric-shieldedvm/ guarded-fabric-addhost-information-for-admin-trusted-attestation
NEW QUESTION 2
Your network contains an Active Directory domain named contoso.com. The domain contains a computer named Computer1 that runs Windows 10. The network uses the 172.16.0.0/16 address space.
Computer1 has an application named App1.exe that is located in D:\Apps\. App1.exe is configured to accept connections on TCP port 8080.
You need to ensure that App1.exe can accept connections only when Computer1 is connected to the corporate network.
Solution: You configure an inbound rule that allows the TCP protocol on port 8080, uses a scope of 172.16.0.0/16 for local IP addresses, and applies to a private profile.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation: “You need to ensure that App1.exe can accept connections only when Computer1 is connected to the corporate network.”, you should create the firewall rule for “Domain” profile instead, not the “Private” profile.
https://technet.microsoft.com/en-us/library/getting-started-wfas-firewall-profilesipsec( v=ws.10).aspx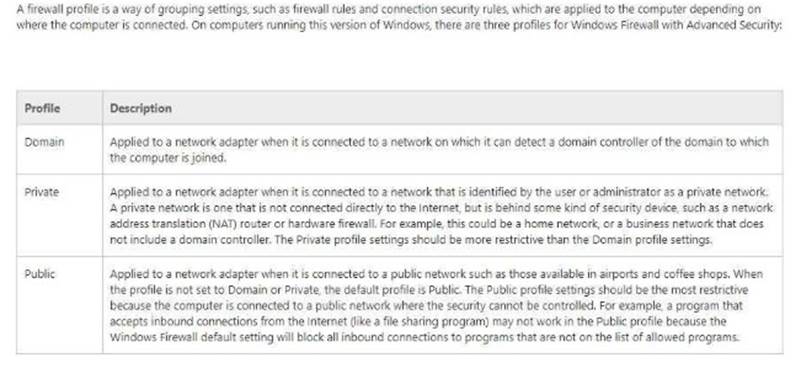
NEW QUESTION 3
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2021.
The local administrator credentials of Server1 are managed by using the Local Administrator Password Solution (LAPS).
You need to retrieve the password of the Administrator account on Server1. What should you do?
- A. From Windows PowerShell on Server1, run the Get-ADFineGrainedPasswordPolicy cmdlet and specify the -Credential parameter.
- B. From Windows PowerShell on Server1, run the Get-ADUser cmdlet and specify the -Credential parameter.
- C. From Active Directory Users and Computers, open the properties at Server1 and view the value at the msMcs-AdmPwd attribute
- D. From Active Directory Users and Computers, open the properties of Administrator and view the value of the userPassword attribute
Answer: C
Explanation: The “ms-Mcs-AdmPwd” attribute of a computer account in Active Directory Users and Computers stores the local Administrator password of a computer, which is configured by LAPS.
NEW QUESTION 4
Your network contains an Active Directory forest named contoso.com. The forest functional level is Windows Server 2012. All servers run Windows Server 2021.
You create a new bastion forest named admin.contoso.com. The forest functional level of admin.contoso.com is Windows Server 2012 R2.
You need to implement a Privileged Access Management (PAM) solution.
Which two actions should you perform? Each correct answer presents part of the solution.
- A. Raise the forest functional level of admm.contoso.com.
- B. Deploy Microsoft Identify Management (MIM) 2021 to admin.contoso.com.
- C. Configure contoso.com to trust admin.contoso.com.
- D. Deploy Microsoft Identity Management (MIM) 2021 to contoso.com.
- E. Raise the forest functional level of contoso.com.
- F. Configure admin.contoso.com to trust contoso.co
Answer: DE
Explanation: https://docs.microsoft.com/en-us/microsoft-identity-manager/pam/deploy-pam-with-windowsserver- 2021
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/windows-server-2021-functionallevels
For the bastion forest which deploys MIM, you should raise the Forest Functional Level to “Windows Server
2021?
NEW QUESTION 5
Note: This question is part of a series of questions that present the same scenario. Each question In the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to It. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest named contoso.com. All servers run Windows Server 2021. The forest contains 2#W client computers that run Windows 10. All client computers are deployed (rom a customized Windows image.
You need to deploy 10 Privileged Access Workstations (PAWs). The solution must ensure that administrators can access several client applications used by all users.
Solution: You deploy 10 physical computers and configure each will as a virtualization host. You deploy the operating system on each host by using the customized Windows image. On each host you create a guest virtual machine and configure the virtual machine as a PAW.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation: References:
https://technet.microsoft.com/en-us/windows-server-docs/security/securing-privilegedaccess/privileged-access-workstations
NEW QUESTION 6
HOTSPOT
Your network contains an Active Directory domain named contoso.com. You plan to deploy an application named App1.exe.
You need to verify whether Control Flow Guard is enabled for App1.exe.
Which command should you run? To answer, select the appropriate options in the answer area.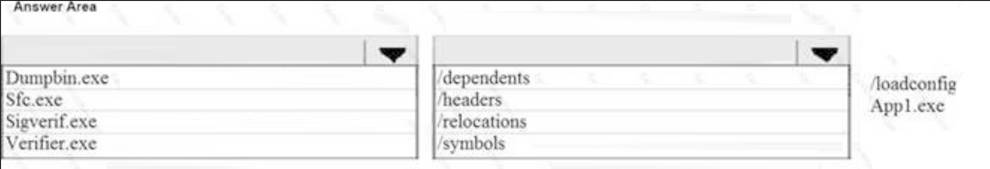
Answer:
Explanation: https://msdn.microsoft.com/en-us/library/windows/desktop/mt637065(v=vs.85).aspx
Control Flow Guard (CFG) is a highly-optimized platform security feature that was created to combat memory corruption vulnerabilities.
By placing tight restrictions on where an application can execute code from, it makes it much harder for explogts to execute arbitrary code through vulnerabilities such as buffer overflows.To verify if Control Flow Guard is enable for a certain application executable:-
Run the dumpbin.exe tool (included in the Visual Studio 2015 installation) from the Visual Studio command
prompt with the /headers and /loadconfig options: dumpbin.exe /headers /loadconfig test.exe.
The output for a binary under CFG should show that the header values include “Guard”, and that the load
config values include “CF Instrumented” and “FID table present”.1
NEW QUESTION 7
Your network contains an Active Directory domain named contoso.com. All servers in the domain run Windows Server 2021.All client computers run Windows 10.
Your company has deployed the Local Administrator Password Solution (LAPS).
Client computers in the finance department are located in an organizational unit (OU) named Finance.
Each finance computer has a custom administrative account named FinAdmin. You discover that the FinAdmin accounts are not managed by LAPS.
You need to ensure that the FinAdmin accounts are managed by LAPS. What should you do?
- A. On the finance computers, register the AdmPwd.ps Windows PowerShell module and then run the ResetAdmPwdPassword cmdlet
- B. Modify the Password Policy in a Group Policy object (GPO).
- C. Modify the LAPS settings in a Group Policy object (GPO).
- D. On the finance computer
- E. rename the FinAdmin accounts to Administrato
Answer: C
Explanation: Use the GPO Setting “Name of administrator account to manage” for LAPS to manage secondary administrative accounts which is not named as “Administrator”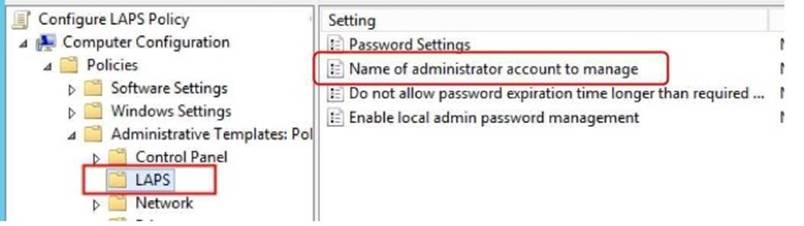
NEW QUESTION 8
Your network contains an Active Directory forest named contoso.com. The forest functional level is Windows Server 2012.
The forest contains 20 member servers that are configured as file servers. All domain controllers run Windows Server 2021.
You create a new forest named contosoadmin.com.
You need to use the Enhanced Security Administrative Environment (ESAE) approach for the administration of the resources in contoso.com.
Which two actions should you perform? Each correct answer presents part of the solution.
- A. From the properties of the trust, enable selective authentication.
- B. Configure contosoadmin.com to trust contoso.com.
- C. Configure contoso.com to trust contosoadmin.com.
- D. From the properties of the trust, enable forest-wide authentication.
- E. Configure a two-way trust between both forest
Answer: AC
Explanation: https://docs.microsoft.com/en-us/windows-server/identity/securing-privileged-access/securingprivilegedaccess- reference-material#ESAE_BM
Trust configurations – Configure trust from managed forests(s) or domain(s) to the administrative forest
A one-way trust is required from production environment to the admin forest. This can be a domain trust or a forest trust.
The admin forest/domain (contosoadmin.com) does not need to trust the managed domains/forests (contoso.com) to manage Active Directory, though additional applications may require a two-way trust relationship, security validation, and testing.
Selective authentication should be used to restrict accounts in the admin forest to only logging on to the
appropriate production hosts.
NEW QUESTION 9
Your network contains an Active Directory domain named contoso.com. The domain contains multiple servers that run either Windows Server 2012 or Windows Server 2012 R2.
You plan to implement Just Enough Administration (JEA) to manage all of the servers.
What should you install on each server to ensure that the servers can be managed by using JEA?
- A. Remote Server Administration Tools (RSAT)
- B. Microsoft .NET Framework 3.5 Service Pack 1 (SP1)
- C. Management Odata Internet Information Services (IIS) Extension
- D. Windows Management Framework 5.0
Answer: D
Explanation: https://msdn.microsoft.com/en-us/library/dn896648.aspx Get JEA
The current release of JEA is available on the following platforms: Windows Server
Windows Server 2021 Technical Preview 5 and higher
Windows Server 2012 R2, Windows Server 2012, and Windows Server 2008 R2* with Windows Management Framework 5.0 installed
NEW QUESTION 10
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2021. All client computers run Windows 10.
The relevant objects in the domain are configured as shown in the following table.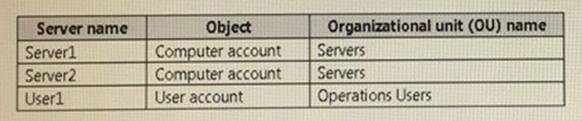
You need to assign User1 the right to restore files and folders on Server1, and Server2. Solution: You add User1 to the Backup Operators group on Server1 and Server2. Does this meet the goal?
- A. Yes
- B. No
Answer: A
Explanation: https://technet.microsoft.com/en-us/library/cc771990(v=ws.11).aspx Backup Operators
Members of this group can back up and restore files on a computer, regardless of any permissions that
protect those files.
This is because the right to perform a backup takes precedence over all file permissions. Members of this
group cannot change security settings.
NEW QUESTION 11
Your network contains an Active Directory domain named contoso.com. You are deploying Microsoft Advanced Threat Analytics (ATA).
You create a user named User1.
You need to configure the user account of User1 as a Honeytoken account. Which information must you use to configure the Honeytoken account?
- A. the SAM account name of User1
- B. the Globally Unique Identifier (GUID) of User1
- C. the SID of User1
- D. the UPN of User1
Answer: C
Explanation: https://docs.microsoft.com/en-us/advanced-threat-analytics/ata-prerequisites A user account of a user who has no network activities.
This account is configured as the ATA Honeytoken user.
To configure the Honeytoken user you need the SID of the user account, not the username.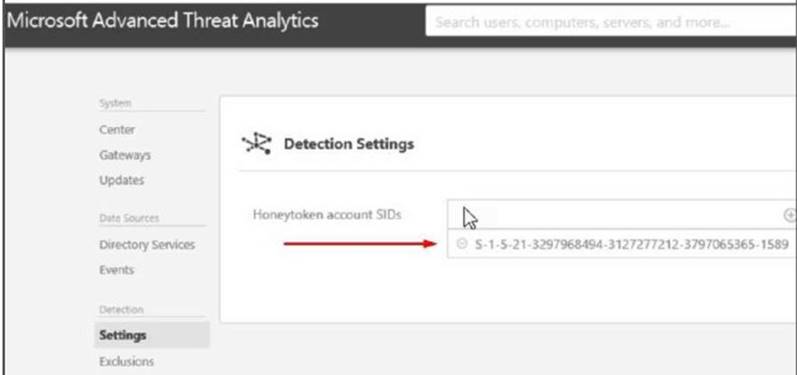
https://docs.microsoft.com/en-us/advanced-threat-analytics/install-ata-step7
ATA also enables the configuration of a Honeytoken user, which is used as a trap for malicious actors
– any
authentication associated with this (normally dormant) account will trigger an alert.
NEW QUESTION 12
Your network contains an Active Directory domain named contoso.com. The domain contains a computer named Computer1 that runs Windows 10. The network uses the 172.16.0.0/16 address space.
Computer1 has an application named App1.exe that is located in D:\Apps\. App1.exe is configured to accept connections on TCP port 8080.
You need to ensure that App1.exe can accept connections only when Computer1 is connected to the corporate network.
Solution: You run the New-NetFirewallRule –DisplayName “Rule1” –Direction Inbound –LocalPort 8080 –Protocol TCP –Action allow –Profile Domain Command.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 13
You network contains an Active Directory forest named contoso.com.
All domain controllers run Windows Server 2021 Member servers run either Windows Server 2012 R2 or Windows Server 2021.
Client computers run either Windows 8.1 or Windows 10.
You need to ensure that when users access files in shared folders on the network, the files are encrypted when they are transferred over the network.
Solution: You enable access-based enumeration on all the file shares. Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation: Access-Based Enumeration does not help encrypting network file transfer.
NEW QUESTION 14
Your network contains an Active Directory domain named contoso.com. The domain contains two DNS servers that run Windows Server 2021. The servers host two zones named contoso.com and admin.contoso.com. You sign both zones.
You need to ensure that all client computers in the domain validate the zone records when they query the zone.
What should you deploy?
- A. a Microsoft Security Compliance Manager (SCM) policy
- B. a zone transfer policy
- C. a Name Resolution Policy Table (NRPT)
- D. a connection security rule
Answer: C
Explanation: You should use Group Policy NRPT to for a DNS Client to perform DNSSEC validation of DNS zone records.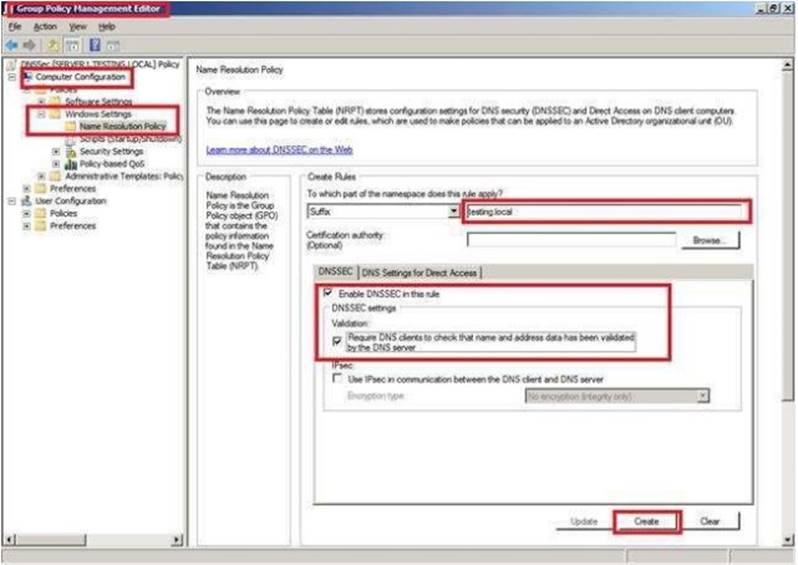
NEW QUESTION 15
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to It. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2021. All client computers run Windows 10.
The relevant objects in the domain are configured as shown in the following table.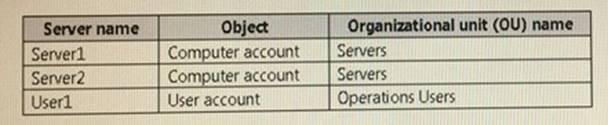
You need to assign User1 the right to restore files and folders on Server1 and Server2.
Solution: You create a Group Policy object (GPO), you link the GPO to the Servers OU, and then you modify the Users Rights Assignment in the GPO.
Does this meet the goat?
- A. Yes
- B. No
Answer: B
Explanation: References:
https://technet.microsoft.com/en-us/library/cc771990(v=ws.11).aspx
NEW QUESTION 16
You have the Windows Server 2021 operating system images as following table.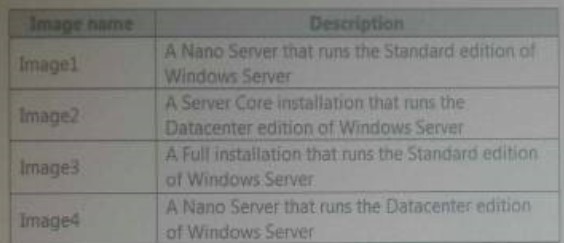
Your company’s security policy states that you must minimize the attack surface when provisioning new servers.
You need to deploy a Host Guardian Service cluster. Which image should you use for the deployment?
- A. image1
- B. image2
- C. image3
- D. image4
Answer: C
Explanation: https://docs.microsoft.com/en-us/windows-server/virtualization/guarded-fabric-shieldedvm/ guarded-fabricprepare-for-hgs
Prerequisites
Hardware: HGS can be run on physical or virtual machines, but physical machines are recommended. If you want to run HGS as a three-node physical cluster (for availability), you must have three physical servers.
(As a best practice for clustering, the three servers should have very similar hardware.)
Operating system: Windows Server 2021, Standard or Datacenter edition. <—- so you cannot use Server Core or Nano Server for running Host
Guardian Service.
Server Roles: Host Guardian Service and supporting server roles.
Configuration permissions/privileges for the fabric (host) domain: You will need to configure DNS forwarding
between the fabric (host) domain and the HGS domain.
If you are using Admin-trusted attestation (AD mode), you will need to configure an Active Directory trust
between the fabric domain and the HGS domain.
NEW QUESTION 17
HOTSPOT
Your network contains two Active Directory forests named adatum.com and priv.adatum.com. You deploy Microsoft Identity Manager (MIM) 2021 to the priv.adatum.com domain, and you implement Privileged Access Management (PAM).
You create a PAM role named Group1 as shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.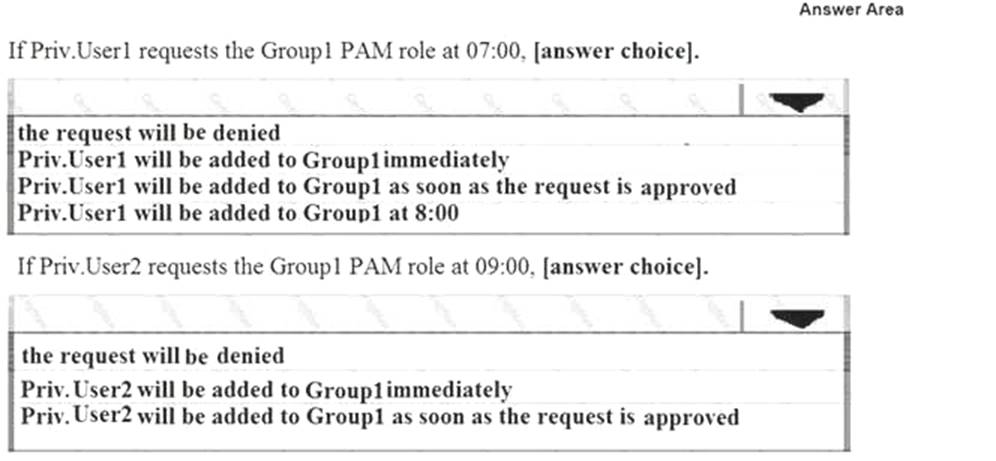
Answer:
Explanation: References:https://tlktechidentitythoughts.wordpress.com/2021/09/07/mim-2021-setting-upprivileged- access-management-pam-in-an-existing-domain-using-the-built-in-pam-tool/
100% Valid and Newest Version 70-744 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/70-744-dumps.html (New 176 Q&As)
- Approved 70-744 Braindumps 2021
- Microsoft 70-333 Study Guides 2021
- The Most up-to-date Guide To 70-410 exam question
- Replace 70-412 Exam Study Guides With New Update Exam Questions
- The Updated Guide To 70-535 exam
- how many questions of 70-464 examcollection?
- Microsoft 70-743 Free Practice Questions 2021
- Microsoft 70-640 Dumps 2021
- Microsoft 70-743 Free Practice Questions 2021
- High quality 70-743 Exam Dumps 2021


