70-744 Exam Questions - Online Test
70-744 Premium VCE File

150 Lectures, 20 Hours
Act now and download your today! Do not waste time for the worthless tutorials. Download with real questions and answers and begin to learn with a classic professional.
Also have 70-744 free dumps questions for you:
NEW QUESTION 1
HOTSPOT
You have a Hyper-V host named Server1 that runs Windows Server 2021. A new security policy states that all the virtual machines must be encrypted.
Server1 hosts the virtual machines configured as shown in the following table.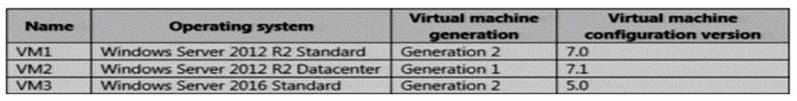
An administrator runs the following commands. Get -VM | Stop-VM
Get -VM | Update-VMVersion Get -VM | Start-VM
For each of the following statements, Select Yes, if the statement is true. Otherwise Select No.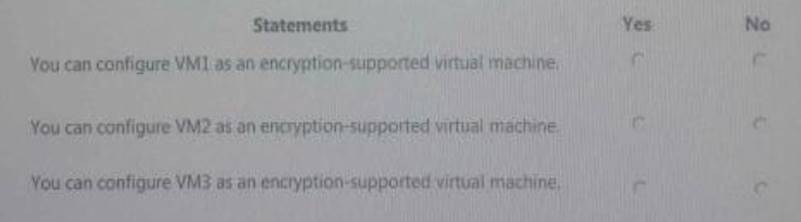
Answer:
Explanation: After the “Update-VMVersion” is executed against all three virtual machines, they become:- VM1 Generation 2 Version 8
VM2 Generation 1 Version 8
VM3 Generation 2 Version 8
Pay attention to VM2, and the question has not mention to use TPM protector. You can configure this VM as Encryption Supported by using a Key Storage Drive added to the virtual machine setting.
Within the guest, there is no Virtual TPM
Then , start Encrypt the C system drive with the guest 2012R2 bitlocker feature
After the encryption is completed:-
NEW QUESTION 2
DRAG DROP
You have two servers named Server1 and Server2 that run Windows Server 2021. The servers are in a workgroup.
You need to create a security template that contains the security settings of Server1 and to apply the template to Server2. The solution must minimize administrative effort.
Which snap-in should you use for each server? To answer, drag the appropriate snap-ins to the correct servers. Each snap-in may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.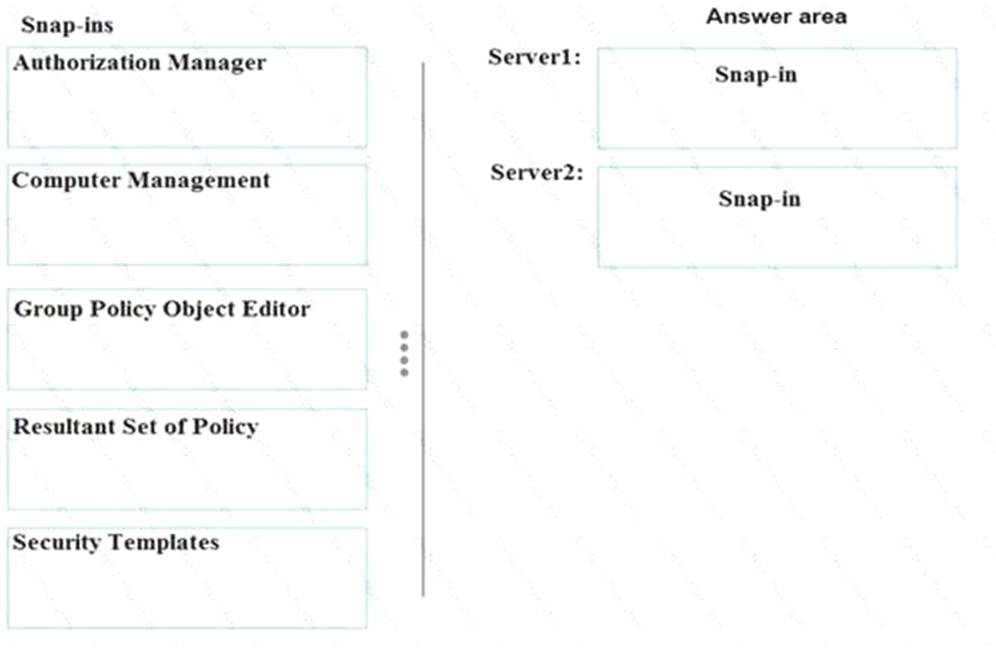
Answer:
Explanation: References:
https://www.windows-server-2012-r2.com/security-templates.html
NEW QUESTION 3
Your network contains an internal network and a perimeter network. The internal network contains an Active Directory forest named contoso.com.
You deploy five servers to the perimeter network.
All of the servers run Windows Server 2021 and are the members of a workgroup.
You need to apply a security baseline named Perimeter.inf to the servers in the perimeter network. What should you use to apply Perimeter.inf?
- A. Local Computer Policy
- B. Security Configuration Wizard (SCW)
- C. Group Policy Management
- D. Server Manager
Answer: A
Explanation: https://docs.microsoft.com/en-us/windows-server/get-started/deprecated-features https://blogs.technet.microsoft.com/secguide/2021/01/21/lgpo-exe-local-group-policy-objectutility- v1-0/
https://msdn.microsoft.com/en-us/library/bb742512.aspx

NEW QUESTION 4
Your network contains an Active Directory forest named corp.contoso.com.
You are implementing Privileged Access Management (PAM) by using a bastion forest named priv.contoso.com.
You need to create shadow groups in priv.contoso.com. Which cmdlet should you use?
- A. New-RoleGroup
- B. New-ADGroup
- C. New-PamRole
- D. New-PamGroup
Answer: D
Explanation: https://social.technet.microsoft.com/wiki/contents/articles/33363.mim-2021-privileged-accessmanagementpam- faq.aspx
https://docs.microsoft.com/en-us/powershell/identitymanager/mimpam/vlatest/new-pamgroup
NEW QUESTION 5
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. The domain has Dynamic Access Control enabled.
Server1 contains a folder named C:Folder1. Folder1 is shared as Share1.
You need to audit all access to the contents of Folder1 from Server2. The solution must minimize the number of event log entries.
Which two audit policies should you enable on Server1? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. Global Object Access- File System
- B. Object Access – Audit Detailed File Share
- C. Object Access – Audit Other Object Access Events
- D. Object Access – Audit File System
- E. Object Access – Audit File Share
Answer: BE
Explanation:
References:
https://docs.microsoft.com/en-us/windows/security/threat-protection/auditing/audit-detailed-fileshare https://docs.microsoft.com/en-us/windows/security/threat-protection/auditing/audit-file-share
NEW QUESTION 6
Your network contains an Active Directory domain named contoso.com. The domain contains 1,000 client computers that run Windows 10.
A security audit reveals that the network recently experienced a Pass-the-Hash attack. The attack was initiated from a client computer and accessed Active Directory objects restricted to the members of the Domain Admins group.
You need to minimize the impact of another successful Pass-the-Hash attack on the domain. What should you recommend?
- A. Instruct all users to sign in to a client computer by using a Microsoft account.
- B. Move the computer accounts of all the client computers to a new organizational unit (OU). Remove the permissions to the new OU from the Domain Admins group.
- C. Instruct all administrators to use a local Administrators account when they sign in to a client computer.
- D. Move the computer accounts of the domain controllers to a new organizational unit (OU). Remove the permissions to the new OU from the Domain Admins group.
Answer: C
Explanation: https://docs.microsoft.com/en-us/windows/access-protection/remote-credential-guard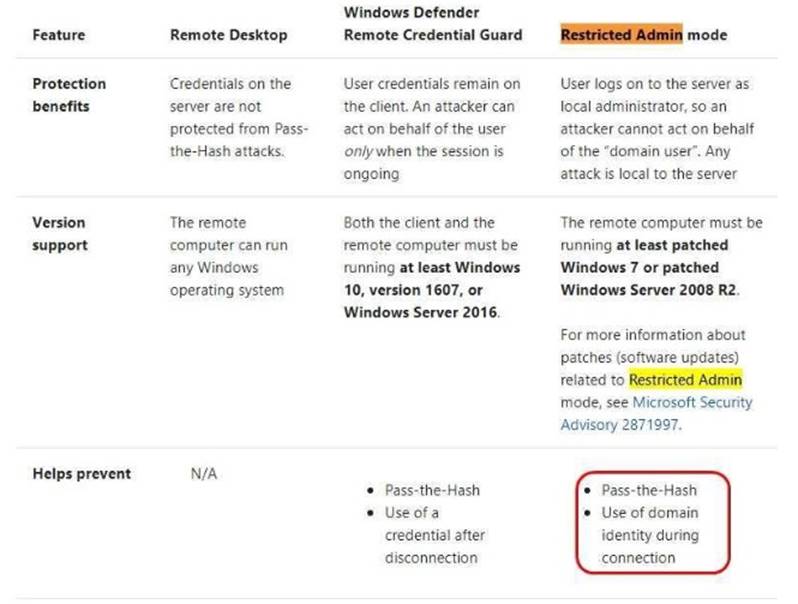
NEW QUESTION 7
You have the servers configured as shown in the following table.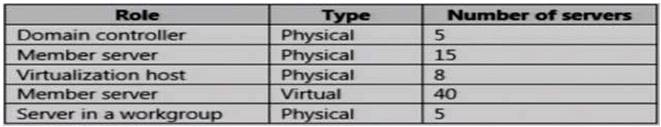
You purchase a Microsoft Azure subscription, and you create three Microsoft Operations
Management Suite (OMS) workspaces named Workspace1, Workspace2, and Workspace3
You need to deploy Microsoft Monitoring Agent to the servers to meet the following requirements:
-Antimalware data from all the servers must be visible in Workspace1.
-Security and audit data from the domain controllers and the virtualization hosts must be visible in Workspace2.
-System update data from all the servers in all the workgroups must be visible in Workspace& How many OMS agents should you deploy?
- A. 10
- B. 33
- C. 73
- D. 45
Answer: C
Explanation: -Antimalware data from all the servers must be visible in Workspace1.
-Security and audit data from the domain controllers and the virtualization hosts must be visible in Workspace2.
-System update data from all the servers in all the workgroups must be visible in Workspace& “All the servers” mean all 5 domain controllers, plus all member servers (physical and virtual, domain and
workgroup) and virtualization hosts, so there are no exemptions.
All servers in the above table mentioned must install OMS Microsoft Monitoring agents
NEW QUESTION 8
Your network contains an Active Directory domain.
Microsoft Advanced Threat Analytics (ATA) is deployed to the domain.
A database administrator named DBA1 suspects that her user account was compromised.
Which three events can you identify by using ATA? Each correct answer presents a complete solution.
- A. Spam messages received by DBA1.
- B. Phishing attempts that targeted DBA1
- C. The last time DBA1 experienced a failed logon attempt
- D. Domain computers into which DBA1 recently signed.
- E. Servers that DBA1 recently accesse
Answer: CDE
Explanation: https://docs.microsoft.com/en-us/advanced-threat-analytics/ata-threats Suspicious authentication failures (Behavioral brute force)
Attackers attempt to use brute force on credentials to compromise accounts. ATA raises an alert when abnormal failed authentication behavior is detected. Abnormal behavior
Lateral movement is a technique often used by attackers, to move between devices and areas in the
victim’s network to gain access to privileged credentials or
sensitive information of interest to the attacker. ATA is able to detect lateral movement by analyzing the
behavior of users, devices and their relationship inside the
corporate network, and detect on any abnormal access patterns which may indicate a lateral movement
performed by an attacker.
https://gallery.technet.microsoft.com/ATA-Playbook-ef0a8e38/view/Reviews ATA Suspicious Activity Playbook Page 35 Action: Attempt to authenticate to DC1
NEW QUESTION 9
The network contains an Active Directory domain named contoso.com. The domain contains the servers configured as shown in the following table.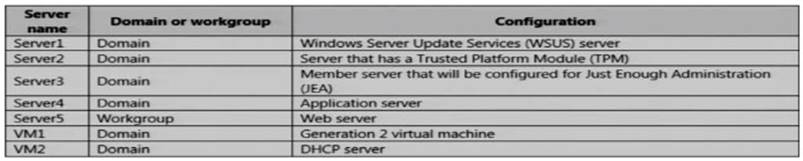
All servers run Windows Server 2021. All client computers run Windows 10 and are domain members.
All laptops are protected by using BitLocker Drive Encryption (BitLocker).You have an organizational unit (OU) named OU1 that contains the computer accounts of application servers.
An OU named OU2 contains the computer accounts of the computers in the marketing department. A Group Policy object (GPO) named GP1 is linked to OU1.
A GPO named GP2 is linked to OU2.
All computers receive updates from Server1. You create an update rule named Update1.
You need to create a Role Capability file on Server3. Which file should you create?
- A. File1.xml
- B. File1.ini
- C. File1.ps1
- D. File1.psrc
Answer: D
NEW QUESTION 10
You enable and configure PowerShell Script Block Logging.
You need to view which script blocks were executed by using Windows PowerShell scripts. What should you do?
- A. View the Microsoft-Windows-PowerShell/Operational event log.
- B. Open the log files in %LocalAppData%\Microsoft\Windows\PowerShell.
- C. View the Windows PowerShell event log.
- D. Open the log files in %SYSTEMROOT%\Log
Answer: A
Explanation: https://docs.microsoft.com/en-us/powershell/wmf/5.0/audit_script
After you enable detailed script tracing, Windows PowerShell logs all script blocks to the event log, MicrosoftWindows-PowerShell/Operational.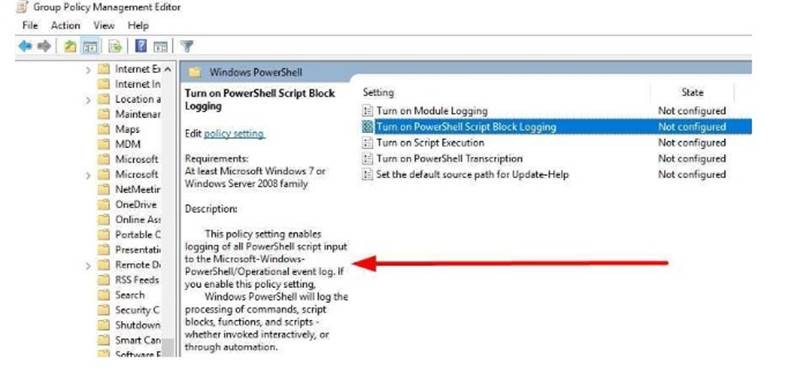
NEW QUESTION 11
You have a Hyper-V host named Server1 that runs Windows Server 2021. Server1 has a generation 2 virtual machine named VM1 that runs Windows 10.
You need to ensure that you can turn on BitLocker Drive Encryption (BitLocker) for drive C: on VM1. What should you do?
- A. From Server1, install the BitLocker feature.
- B. From Server1, enable nested virtualization for VM1.
- C. From VM1, configure the Require additional authentication at startup Group Policy setting.
- D. From VM1, configure the Enforce drive encryption type on fixed data drives Group Policy settin
Answer: C
Explanation: https://www.howtogeek.com/howto/6229/how-to-use-bitlocker-on-drives-without-tpm/
If you don’t use TPM for protecting a drive, there is no such Virtual TPM or VM Generation, or VM Configuration
version requirement, you can even use Bitlocker without TPM Protector with earlier versions of Windows. How to Use BitLocker Without a TPM
You can bypass this limitation through a Group Policy change. If your PC is joined to a business or school
domain, you can’t change the Group Policy setting
yourself. Group policy is configured centrally by your network administrator.
To open the Local Group Policy Editor, press Windows+R on your keyboard, type “gpedit.msc” into the Run
dialog box, and press Enter.
Navigate to Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating
System Drives in the left pane.
Double-click the “Require additional authentication at startup” option in the right pane.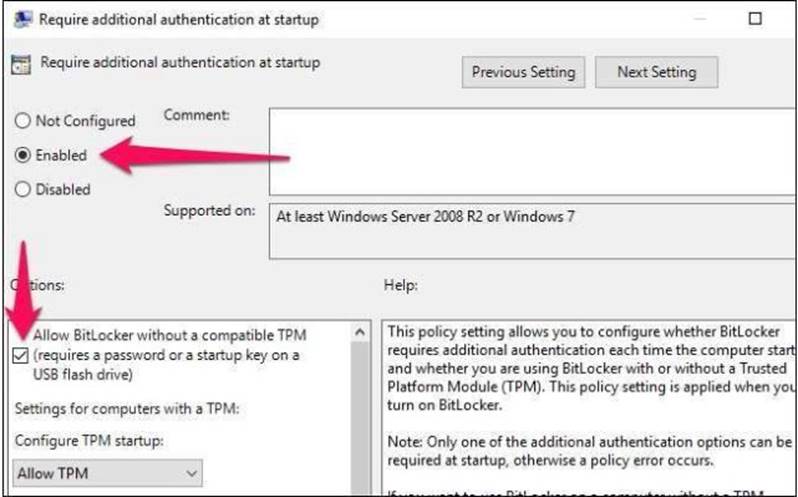
Select “Enabled” at the top of the window, and ensure the “Allow BitLocker without a compatible TPM
(requires a password or a startup key on a USB flash drive)” checkbox is enabled here.
Click “OK” to save your changes. You can now close the Group Policy Editor window. Your change takes effect immediately—you don’t even need to reboot.
NEW QUESTION 12
HOTSPOT
Your network contains an Active Directory domain named adatum.com. The domain contains a file server named Server1 that runs Windows Server 2021.
You have an organizational unit (OU) named OU1 that contains Server1. You create a Group Policy object (GPO) named GPO1 and link GPO1 to OU1.
A user named User1 is a member of group named Group1. The properties of User1 are shown in the User1 exhibit (Click the Exhibit button.)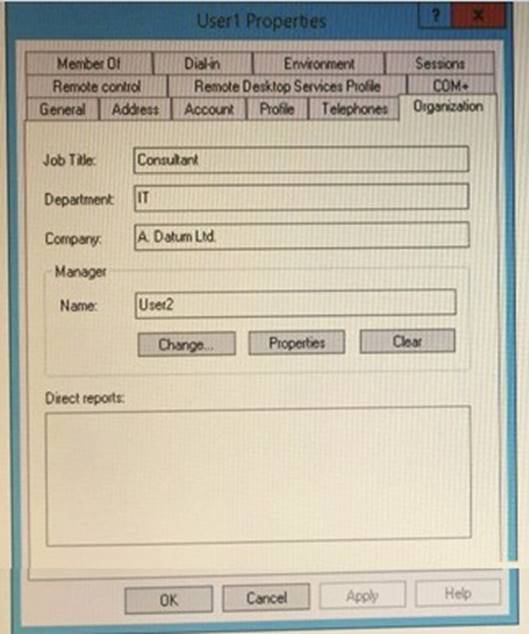
User1 has permissions to two files on Server1 configured as shown in the following table.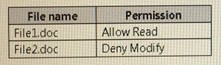
From Auditing Entry for Global File SACL, you configure the advanced audit policy settings in GPO1 as shown in the SACL exhibit (Click the Exhibit button.)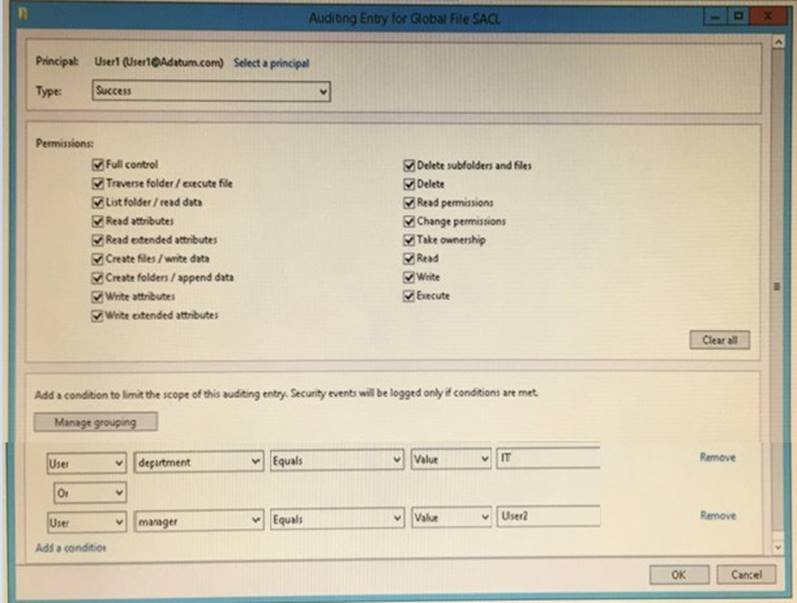
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Answer:
Explanation: From File Explorer, when User1 double-clicks File1.doc. an event will be logged: Yes From File Explorer, when User1 double-clicks File2.doc. an event will be logged: No
From Microsoft Word, when User1 attempts to save changes to File1.doc, an event will be logged: No
From the SACL, only Successful operations by User1 will be logged “Type: Success”.
NEW QUESTION 13
You have a virtual machine named FS1 that runs Windows Server 2021. FS1 has the shared folders shown in the following table.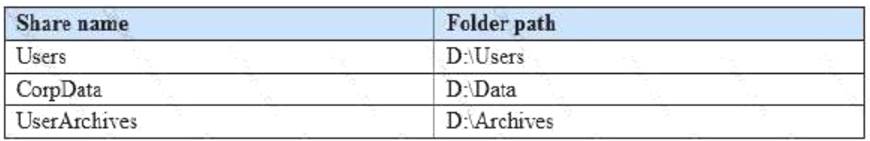
You need to ensure that each user can store 10 GB of files in \FS1Users. What should you do?
- A. From File Explorer, open the properties of volume D, and then modify the Quota settings.
- B. Install the File Server Resource Manager role service, and then create a file screen.
- C. From File Explorer, open the properties of D:Users, and then modify the Advanced sharing settings.
- D. Install the File Server Resource Manager role service, and then create a quota.
Answer: D
Explanation:
References:
https://docs.microsoft.com/en-us/windows-server/storage/fsrm/create-quota
NEW QUESTION 14
Your network contains an Active Directory domain named contoso.com. The domain contains several Hyper-V hosts.
You deploy a server named Server22 to a workgroup. Server22 runs Windows Server 2021. You need to configure Server22 as the primary Host Guardian Service server.
Which three cmdlets should you run in sequence?
- A. Install-HgsServer
- B. Install-Module
- C. Install-Package
- D. Enable-WindowsOptionalFeature
- E. Install-ADDSDomainController
- F. Initialize-HgsServer
Answer: AEF
Explanation: Correct order of actions:
1. Install-ADDSDomainController , as Server22 is a workgroup computer, create a new domain on it first.
2. Install-HgsServer
3. Initialize-HgsServer
https://docs.microsoft.com/en-us/windows-server/virtualization/guarded-fabric-shieldedvm/guarded-fabricsetting-up-the-host-guardian-service-hgs
https://docs.microsoft.com/en-us/windows-server/virtualization/guarded-fabric-shieldedvm/guarded-fabricinstall-hgs-default
Install-HgsServer
https://docs.microsoft.com/en-us/windows-server/virtualization/guarded-fabric-shieldedvm/guarded-fabricinitialize-hgs-tpm-mode-default
Initialize-HgsServer
NEW QUESTION 15
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Serve1, that runs Windows Server 2021.
A technician is testing the deployment of Credential Guard on Server1. You need to verify whether Credential Guard is enabled on Server1. What should you do?
- A. From a command prompt fun the credwiz.exe command.
- B. From Task Manager, review the processes listed on the Details tab.
- C. From Server Manager, click Local Server, and review the properties of Server!
- D. From Windows PowerShell, run the Get-WsManCredSSP cmdle
Answer: B
Explanation: https://yungchou.wordpress.com/2021/10/10/credential-guard-made-easy-in-windows-10-version- 1607/
The same as before, once Credential Guard is properly configured, up and running.
You should find in Task Manager the ‘Credential Guard’ process and ‘lsaiso.exe’ listed in the Details page as below.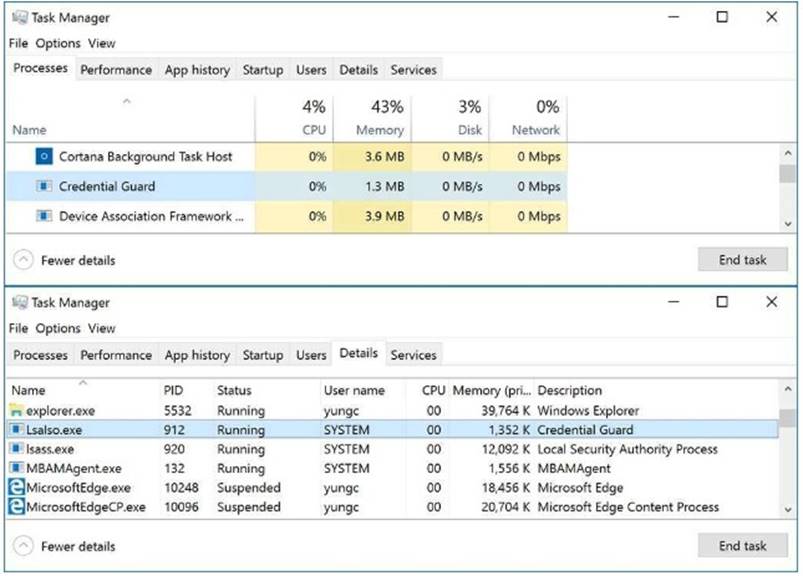
NEW QUESTION 16
You have a server named Server1 that runs Windows Server 2021.
You need to install Security Compliance Manager (SCM) 4.0 on Server1. What should you install on Server1 first?
- A. the .NET Framework 3.5 Features feature
- B. the Active Directory Rights Management Services server role
- C. the Remote Server Administration Tools feature
- D. the Group Policy Management feature
Answer: A
NEW QUESTION 17
Your network contains an Active Directory domain named contoso.com. The domain contains a
server named Server5 that has the Windows Server Update Services server role installed. You need to configure Windows Server Update Services (WSUS) on Server5 to use SSI. You install a certificate in the local Computer store.
Which two tools should you use? Each correct answer presents part of the solution.
- A. Wsusutil
- B. Netsh
- C. Internet Information Services (IIS) Manager
- D. Server Manager
- E. Update Services
Answer: AC
Explanation: By IIS Manager and “wsusutil configuressl” command https://technet.microsoft.com/en-us/library/bb633246.aspx To configure SSL on the WSUS server by using IIS 7.0
1) On the WSUS server, open Internet Information Services (IIS) Manager.
2) Expand Sites, and then expand the Web site for the WSUS server. We recommend that you use the WSUS
Administration custom Web site, but the default Web
site might have been chosen when WSUS was being installed.
3) Perform the following steps on the APIRemoting30, ClientWebService, DSSAuthWebService,
ServerSyncWebService, and SimpleAuthWebService virtual directories that reside under the WSUS Web site.
In Features View, double-click SSL Settings.
On the SSL Settings page, select the Require SSL checkbox. Ensure that Client certificates is set to Ignore.
In the Actions pane, click Apply.
4) Close Internet Information Services (IIS) Manager.
5) Run the following command from <WSUS Installation Folder>\Tools: WSUSUtil.exe configuressl
<Intranet
FQDN of the software update point site system>.
100% Valid and Newest Version 70-744 Questions & Answers shared by 2passeasy, Get Full Dumps HERE: https://www.2passeasy.com/dumps/70-744/ (New 176 Q&As)
- Improved Microsoft 70-464 vce
- What 100% Guarantee 70-461 braindumps Is?
- What Free 701-100 Pdf Is
- Approved Mb-300 Pdf 2021
- 10 Tips For Down to date 70-410 exam question
- Microsoft 70-741 Dumps Questions 2021
- What Free 70-346 exam Is?
- Accurate MB2-713 Exam Questions and Answers 2021
- 10 Tips For Improved 70-463 exam question
- The Secret of Microsoft 70-533 examcollection


