70-744 Exam Questions - Online Test
70-744 Premium VCE File

150 Lectures, 20 Hours
We provide which are the best for clearing 70-744 test, and to get certified by Microsoft Securing Windows Server 2021. The covers all the knowledge points of the real 70-744 exam. Crack your Microsoft 70-744 Exam with latest dumps, guaranteed!
Check 70-744 free dumps before getting the full version:
NEW QUESTION 1
HOTSPOT
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
Your network contains an Active Directory domain named contoso.com. The functional level of the forest and the domain is Windows Server 2008 R2.
The domain contains the servers configured as shown in the following table.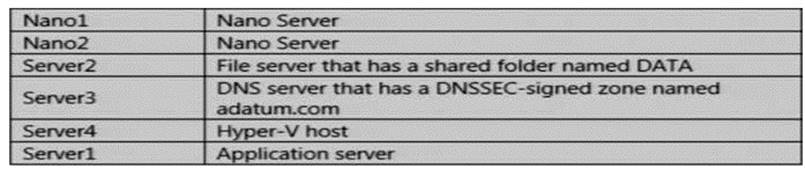
All servers run Windows Server 2021. All client computers run Windows 10.
You have an organizational unit (OU) named Marketing that contains the computers in the marketing department. You have an OU named Finance that contains the computers in the finance department. You have an OU named AppServers that contains application servers. A Group Policy object (GPO) named GP1 is linked to the Marketing OU. A GPO named GP2 is linked to the AppServers OU. You install Windows Defender on Nano1.
End of repeated scenario.
You need to configure Nano1 as a Hyper-V host.
Which command should you run? To answer, select the appropriate options in the answer area.
Answer:
Explanation:
References:
https://docs.microsoft.com/en-us/windows-server/get-started/deploy-nano-server
NEW QUESTION 2
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1 that runs Windows Server 2021.Server1 has a shared folder named Share1. You plan to create a subfolder in Share1 for each domain user.
You need to limit each user to using 100 MB of data in their respective subfolder.
The solution must enable the users to be notified when they use 80 percent of the available space in the subfolder.
Which tool should you use?
- A. File Explorer
- B. Shared Folders
- C. Server Manager
- D. Disk Management
- E. Storage Explorer
- F. Computer Management
- G. System Configuration
- H. File Server Resource Manager (FSRM)
Answer: H
NEW QUESTION 3
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2021. You need to prevent NTLM authentication on Server1.
Solution: From Windows PowerShell, you run the Disable-WindowsOptionalFeature cmdlet. Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation: https://blogs.technet.microsoft.com/filecab/2021/09/16/stop-using-smb1/
On Client, the PowerShell approach (Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol)
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol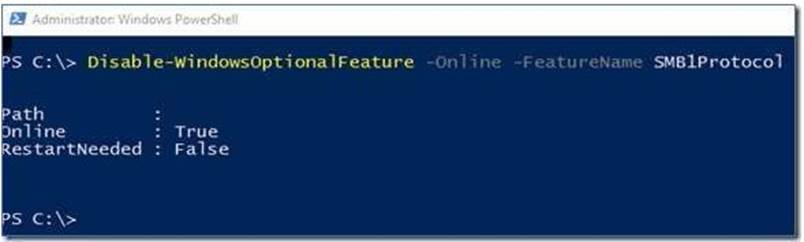
However, the question asks about Server!
On Server, the PowerShell approach (Remove-WindowsFeature FS-SMB1): Remove-WindowsFeature FS-SMB1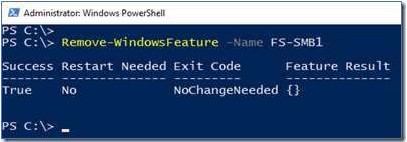
Even if SMB1 is removed, SMB2 and SMB3 could still run NTLM authentication! Therefore, answer is a“NO”.
NEW QUESTION 4
You have two computers configured as shown in the following table.
You need to ensure that the credentials that you use to establish Remote Desktop sessions from Client1 to Server1 are protected by using Remote CredentialGuard.
- A. Join Client1 to the domain.
- B. Remove Server1 from the domain.
- C. Upgrade Server1 to Windows Server 2021 Datacenter.
- D. Upgrade Client1 to Windows 10 Enterpris
Answer: A
Explanation: https://docs.microsoft.com/en-us/windows/access-protection/remote-credential-guard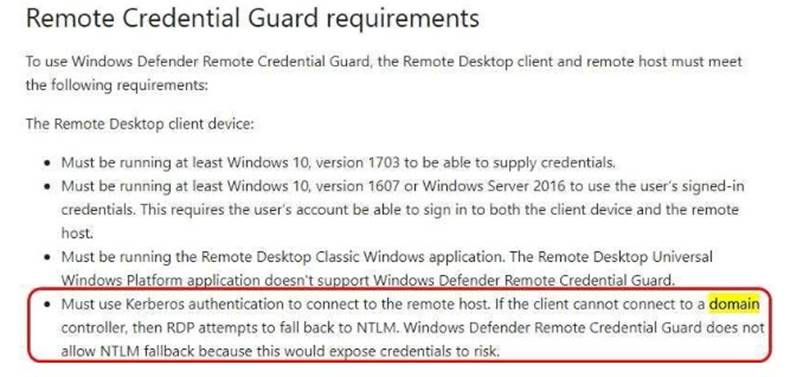
NEW QUESTION 5
Your network contains an Active Directory domain named contoso.com.
You deploy a server named Server1 that runs Windows Server 2021. Server1 is in a workgroup. You need to collect the logs from Server1 by using Log Analytics in Microsoft Operations Management Suite (OMS).
What should you do first?
- A. Join Server1 to the domain.
- B. Create a Data Collector Set.
- C. Install Microsoft Monitoring Agent on Server1.
- D. Create an event subscriptio
Answer: C
Explanation: https://docs.microsoft.com/en-us/azure/log-analytics/log-analytics-windows-agents
You need to install and connect Microsoft Monitoring Agent for all of the computers that you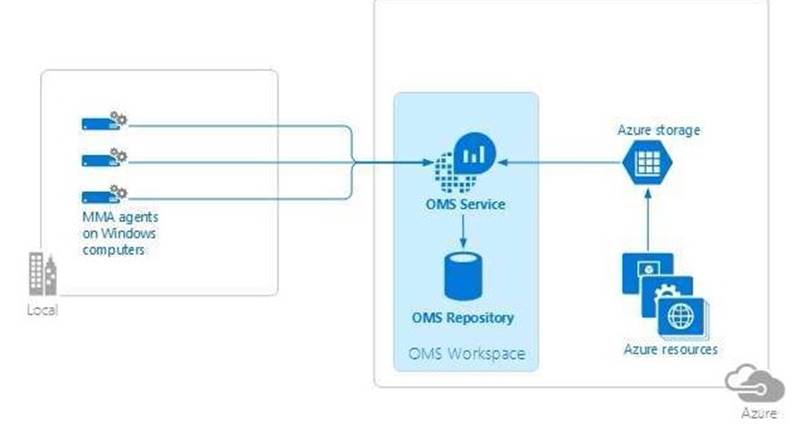
You can install the OMS MMA on stand-alone computers, servers, and virtual machines.
NEW QUESTION 6
The network contains an Active Directory domain named contoso.com. The domain contains the servers configured as shown in the following table.
All servers run Windows Server 2021. All client computers run Windows 10 and are domain members.
All laptops are protected by using BitLocker Drive Encryption (BitLocker).
You have an organizational unit (OU) named OU1 that contains the computer accounts of application servers.
An OU named OU2 contains the computer accounts of the computers in the marketing department. A Group Policy object (GPO) named GP1 is linked to OU1.
A GPO named GP2 is linked to OU2.
All computers receive updates from Server1. You create an update rule named Update1.
You need to prepare the environment to support applying Update1 to the laptops only. What should you do? Choose Two.
- A. Tool to use: Active Directory Administrative Center
- B. Tool to use: Active Directory Users and Computers
- C. Tool to use: Microsoft Intune
- D. Tool to use: Update Services
- E. Type of object to create: A computer group
- F. Type of object to create: A distribution group
- G. Type of object to create: A mobile device group
- H. Type of object to create: A security group
- I. Type of object to create: An OU
Answer: DE
Explanation: https://technet.microsoft.com/en-us/library/cc708458(v=ws.10).aspx
NEW QUESTION 7
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest named contoso.com. All servers run Windows Server 2021. The forest contains 2,000 client computers that run Windows 10. All client computers are deployed from a customized Windows image.
You need to deploy 10 Privileged Access Workstations (PAWs). The solution must ensure that administrators can access several client applications used by all users.
Solution: You deploy one physical computer and configure it as a Hyper-V host that runs Windows Server 2021. You create 10 virtual machines and configure each one as a PAW.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation: References:
https://technet.microsoft.com/en-us/windows-server-docs/security/securing-privilegedaccess/privileged-access-workstations
NEW QUESTION 8
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this sections, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com. The domain contains a computer named Computer1 that runs Windows10.
The network uses the 172.16.0.0/16 address space.
Computer1 has an application named App1.exe that is located in D:Apps. App1.exe is configured to accept connections on TCP port 8080.
You need to ensure that App1.exe can accept connections only when Computer1 is connected to the corporate network.
Solution: You run the New-NetFirewallRule –DisplayName "Rule1" –Direction Inbound
–Program "D:AppsApp1.exe" –Action Allow -Profile Domain command. Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 9
HOTSPOT
Your network contains an Active Directory domain named contoso.com. You have an organizational unit (OU) named Secure that contains all servers.
You install Microsoft Security Compliance Manager (SCM) 4.0 on a server named Server1. You need to export the SCM Pnnt Server Secunty baseline and to deploy the baseline to a server named Server2.
What should you do? To answer, select the appropnate options in the answer area.
Answer:
Explanation: When the security settings is exported from SCM 4 in a GPO (folder) format, with a long GUID name
You have to import it to GPO by using “Group Policy Management”, right-click the GPO and use “Import
Settings” button
Do not confuse with security template .inf files. Only security template .INF file (which is a single file, not a
folder) could be imported to a GPO by Group Policy Object Editor
NEW QUESTION 10
You have a server named Server1 that runs Windows Server 2021. Server1 has the Windows Server Update Services server role installed.
Windows Server Update Services (WSUS) updates for Server1 are stored on a volume named D. The hard disk that contains volume D fails.
You replace the hard disk. You recreate volume D and the WSUS folder hierarchy in the volume. You need to ensure that the updates listed in the WSUS console are available in the WSUS folder. What should you run?
- A. wsusutil.exe /import
- B. wsusutil.exe /reset
- C. Set-WsusServerSynchronization
- D. Invoke-WsusServerCleanup
Answer: B
Explanation: https://technet.microsoft.com/en-us/library/cc720466%28v=ws.10%29.aspx?f=255&MSPPError=- 2147217396
WSUSutil.exe is a tool that you can use to manage your WSUS server from the command line.
WSUSutil.exe
is located in the %drive%\Program Files\Update Services\Tools folder on your WSUS server.
You can run specific commands with WSUSutil.exe to perform specific functions, as summarized in the
following table.
The syntax you would use to run WSUSutil.exe with specific commands follows the table.
NEW QUESTION 11
HOTSPOT
You plan to deploy three encrypted virtual machines that use Secure Boot. The virtual machines will be configured as shown in the following table.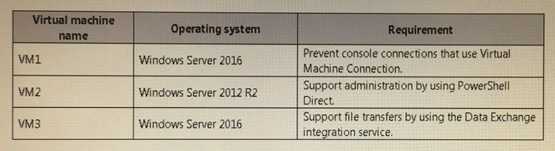
How should you protect each virtual machine? To answer, select the appropriate options in the answer area.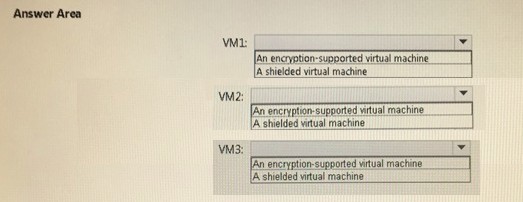
Answer:
Explanation: Shielded VM Prevents Virtual Machine connection and PowerShell Direct, it prevent the Hyper-V host to interact in any means with the Shielded VM.
https://docs.microsoft.com/en-us/windows-server/virtualization/guarded-fabric-shieldedvm/guarded-fabric-andshielded-vms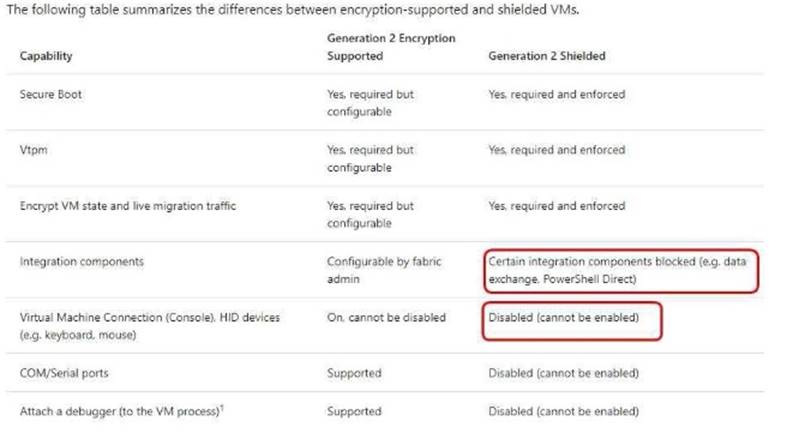
NEW QUESTION 12
The New-CIPolicy cmdlet creates a Code Integrity policy as an .xml file. If you do NOT supply either driver files or rules what will happen?
- A. The cmdlet performs a system scan
- B. An exception/warning is shown because either one is required
- C. Nothing
- D. The cmdlet searches the Code Integrity Audit log for drivers
Answer: A
Explanation: If you do not supply either driver files or rules, this cmdlet performs a system scan similar to the Get- SystemDriver cmdlet.
The cmdlet generates rules based on Level. If you specify the Audit parameter, this cmdlet scans the Code Integrity Audit log instead.
NEW QUESTION 13
Your network contains an Active Directory domain named contoso.com.
You download Microsoft Security Compliance Toolkit 1.0 and all the security baselines.
You need to deploy one of the security baselines to all the computers in an organizational unit (OU) named OU1.
What should you do?
- A. Run 1gpo.exe and specify the /g paramete
- B. From Policy Analyzer, click Add.
- C. From Group Policy Management, create and link a Group Policy object (GPO). Select the GPO and run the Import Settings Wizard.
- D. From Group Policy Management, click Group Policy Objects, and then click Manage Backups…
- E. From Group Policy Management, create and link a Group Policy object (GPO). Run 1gpo.exe and specify the /g parameter.
Answer: B
Explanation:
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/deployment/distributecertificates- to-client-computers-by-using-group-policy
NEW QUESTION 14
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain contains several Hyper-V hosts.
You deploy a server named Server22 to a workgroup. Server22 runs Windows Server 2021. You need to configure Server22 as the primary Host Guardian Service server.
Which three cmdlets should you run in sequence? To answer move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.
Answer:
Explanation: References:
https://docs.microsoft.com/en-us/windows-server/virtualization/guarded-fabric-shieldedvm/ guarded-fabric-setting-up-the-host-guardian-service-hgs
NEW QUESTION 15
Note: This question It part of a series of questions that present the same scenario. Each question In the series contains a unique solution that might meet the stated goats. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to It. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com. The domain contains a computer named Computer1 that runs Windows 10. Computer1 connects to a home network and a corporate network.
The corporate network uses the 17216.0.0/24 address space internally. Computer1 runs an application named App1 that listens to port 8080.
You need to prevent connections to App1 when Computer1 is connected to the home network. Solution: From Group Policy Management you create a software restriction policy.
Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation: Software Restriction Policy does not filter incoming network traffic, what you actually need is Windows Firewall Inbound Rule on the Private profile
References:
https://technet.microsoft.com/en-us/library/hh831534(v=ws.11).aspx
NEW QUESTION 16
HOTSPOT
Your network contains an Active Directory forest named contoso.com. The forest has Microsoft Identity Manager (MIM) 2021 deployed. You implement Privileged Access Management (PAM).
You need to request privileged access from a client computer in contoso.com by using PAM.
How should you complete the Windows PowerShell script? To answer, select the appropriate options in the answer area.
Answer:
Explanation: $PAM = Get-PAMRoleForRequest | ? {$_,DisplayName -eq “CorpAdmins” } New-PAMRequest -role $PAM
References:
https://technet.microsoft.com/en-us/library/mt604089.aspx https://technet.microsoft.com/en-us/library/mt604084.aspx
NEW QUESTION 17
The “Network Security: Restrict NTLM: NTLM authentication in this domain” policy setting allows you to deny or allow NTLM authentication within a domain from this domain controller.
Which value would you choose so that the domain controller will deny all NTLM authentication logon attempts using accounts from this domain to all servers in the domain.
The NTLM authentication attempts will be blocked and will return an NTLM blocked error unless the server name is on the exception list in the Network security: Restrict NTLM: Add server exceptions in this domain policy setting.
- A. Deny for domain accounts
- B. Deny for domain accounts to domain servers
- C. Deny all
- D. Deny for domain servers
Answer: B
100% Valid and Newest Version 70-744 Questions & Answers shared by 2passeasy, Get Full Dumps HERE: https://www.2passeasy.com/dumps/70-744/ (New 176 Q&As)
- What 100% Correct 70-480 pdf Is?
- Microsoft AZ-100 Study Guides 2021
- 10 Tips For Most recent MB6-896 dumps
- What Free 701-100 Pdf Is
- how many questions of 70-467 practice test?
- What Real 70-411 exam dumps Is?
- Certified 70-735 Braindumps 2021
- All About Actual 70-488 braindumps
- The Secret of Microsoft 70-535 exam dumps
- The Up to date Guide To 70-680 dumps


