CEH-001 Exam Questions - Online Test
CEH-001 Premium VCE File

150 Lectures, 20 Hours
Master the CEH-001 Certified Ethical Hacker (CEH) content and be ready for exam day success quickly with this Pass4sure CEH-001 vce. We guarantee it!We make it a reality and give you real CEH-001 questions in our GAQM CEH-001 braindumps.Latest 100% VALID GAQM CEH-001 Exam Questions Dumps at below page. You can use our GAQM CEH-001 braindumps and pass your exam.
Check CEH-001 free dumps before getting the full version:
NEW QUESTION 1
Which of the following are password cracking tools? (Choose three.)
- A. BTCrack
- B. John the Ripper
- C. KerbCrack
- D. Nikto
- E. Cain and Abel
- F. Havij
Answer: BCE
NEW QUESTION 2
One of your junior administrator is concerned with Windows LM hashes and password cracking. In your discussion with them, which of the following are true statements that you would point out?
Select the best answers.
- A. John the Ripper can be used to crack a variety of passwords, but one limitation is that the output doesn't show if the password is upper or lower case.
- B. BY using NTLMV1, you have implemented an effective countermeasure to password cracking.
- C. SYSKEY is an effective countermeasure.
- D. If a Windows LM password is 7 characters or less, the hash will be passed with the following characters, in HEX- 00112233445566778899.
- E. Enforcing Windows complex passwords is an effective countermeasure.
Answer: ACE
Explanation:
Explanations:
John the Ripper can be used to crack a variety of passwords, but one limitation is that the output doesn't show if the password is upper or lower case. John the Ripper is a very effective password cracker. It can crack passwords for many different types of operating systems. However, one limitation is that the output doesn't show if the password is upper or lower case. BY using NTLMV1, you have implemented an effective countermeasure to password cracking. NTLM Version 2 (NTLMV2) is a good countermeasure to LM password cracking (and therefore a correct answer). To do this, set Windows 9x and NT systems to "send NTLMv2 responses only". SYSKEY is an effective countermeasure. It uses 128 bit encryption on the local copy of the Windows SAM. If a Windows LM password is 7 characters or less, the has will be passed with the following characters: 0xAAD3B435B51404EE
Enforcing Windows complex passwords is an effective countermeasure to password cracking. Complex passwords are- greater than 6 characters and have any 3 of the following 4 items: upper case, lower case, special characters, and numbers.
NEW QUESTION 3
While performing data validation of web content, a security technician is required to restrict malicious input. Which of the following processes is an efficient way of restricting malicious input?
- A. Validate web content input for query strings.
- B. Validate web content input with scanning tools.
- C. Validate web content input for type, length, and range.
- D. Validate web content input for extraneous queries.
Answer: C
NEW QUESTION 4
Lauren is performing a network audit for her entire company. The entire network is comprised of around 500 computers. Lauren starts an ICMP ping sweep by sending one IP packet to the broadcast address of the network, but only receives responses from around five hosts. Why did this ping sweep only produce a few responses?
- A. Only Windows systems will reply to this scan.
- B. A switched network will not respond to packets sent to the broadcast address.
- C. Only Linux and Unix-like (Non-Windows) systems will reply to this scan.
- D. Only servers will reply to this scan.
Answer: C
NEW QUESTION 5
Windows LAN Manager (LM) hashes are known to be weak. Which of the following are known weaknesses of LM? (Choose three)
- A. Converts passwords to uppercase.
- B. Hashes are sent in clear text over the network.
- C. Makes use of only 32 bit encryption.
- D. Effective length is 7 characters.
Answer: ABD
Explanation:
The LM hash is computed as follows.
1. The user’s password as an OEM string is converted to uppercase.
2. This password is either null-padded or truncated to 14 bytes.
3. The “fixed-length” password is split into two 7-byte halves.
4. These values are used to create two DES keys, one from each 7-byte half.
5. Each of these keys is used to DES-encrypt the constant ASCII string “KGS!@#$%”, resulting in two 8-byte ciphertext values.
6. These two ciphertext values are concatenated to form a 16-byte value, which is the LM hash.
The hashes them self are sent in clear text over the network instead of sending the password in clear text.
NEW QUESTION 6
Which of the following parameters enables NMAP's operating system detection feature?
- A. NMAP -sV
- B. NMAP -oS
- C. NMAP -sR
- D. NMAP -O
Answer: D
NEW QUESTION 7
Which of the following is a hashing algorithm?
- A. MD5
- B. PGP
- C. DES
- D. ROT13
Answer: A
NEW QUESTION 8
Exhibit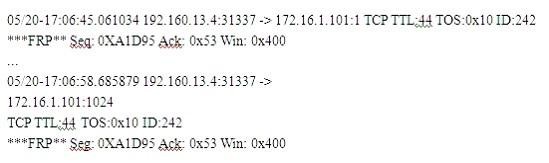
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.)
Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
What is odd about this attack? Choose the best answer.
- A. This is not a spoofed packet as the IP stack has increasing numbers for the three flags.
- B. This is back orifice activity as the scan comes form port 31337.
- C. The attacker wants to avoid creating a sub-carries connection that is not normally valid.
- D. These packets were crafted by a tool, they were not created by a standard IP stack.
Answer: B
Explanation:
Port 31337 is normally used by Back Orifice. Note that 31337 is hackers spelling of ‘elite’, meaning ‘elite hackers’.
NEW QUESTION 9
Bluetooth uses which digital modulation technique to exchange information between paired devices?
- A. PSK (phase-shift keying)
- B. FSK (frequency-shift keying)
- C. ASK (amplitude-shift keying)
- D. QAM (quadrature amplitude modulation)
Answer: A
NEW QUESTION 10
In what stage of Virus life does a stealth virus gets activated with the user performing certain actions such as running an infected program?
- A. Design
- B. Elimination
- C. Incorporation
- D. Replication
- E. Launch
- F. Detection
Answer: E
NEW QUESTION 11
In which step Steganography fits in CEH System Hacking Cycle (SHC)
- A. Step 2: Crack the password
- B. Step 1: Enumerate users
- C. Step 3: Escalate privileges
- D. Step 4: Execute applications
- E. Step 5: Hide files
- F. Step 6: Cover your tracks
Answer: E
NEW QUESTION 12
What port number is used by LDAP protocol?
- A. 110
- B. 389
- C. 464
- D. 445
Answer: B
NEW QUESTION 13
Which of the following tools can be used to perform a zone transfer?
- A. NSLookup
- B. Finger
- C. Dig
- D. Sam Spade
- E. Host
- F. Netcat
- G. Neotrace
Answer: ACDE
Explanation:
There are a number of tools that can be used to perform a zone transfer. Some of these include: NSLookup, Host, Dig, and Sam Spade.
NEW QUESTION 14
Blane is a network security analyst for his company. From an outside IP, Blane performs an XMAS scan using Nmap. Almost every port scanned does not illicit a response. What can he infer from this kind of response?
- A. These ports are open because they do not illicit a response.
- B. He can tell that these ports are in stealth mode.
- C. If a port does not respond to an XMAS scan using NMAP, that port is closed.
- D. The scan was not performed correctly using NMAP since all ports, no matter what their state, will illicit some sort of response from an XMAS scan.
Answer: A
NEW QUESTION 15
A security administrator notices that the log file of the company`s webserver contains suspicious entries: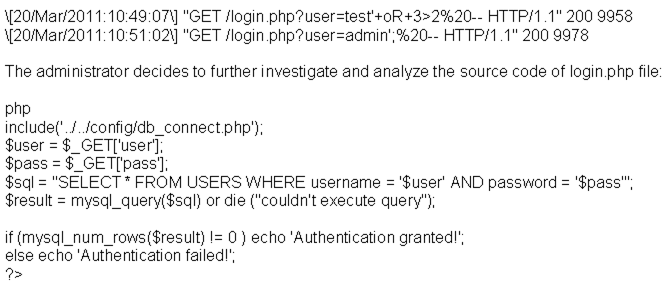
Based on source code analysis, the analyst concludes that the login.php script is vulnerable to
- A. command injection.
- B. SQL injection.
- C. directory traversal.
- D. LDAP injection.
Answer: B
NEW QUESTION 16
This kind of password cracking method uses word lists in combination with numbers and special characters:
- A. Hybrid
- B. Linear
- C. Symmetric
- D. Brute Force
Answer: A
Explanation:
A Hybrid (or Hybrid Dictionary) Attack uses a word list that it modifies slightly to find passwords that are almost from a dictionary (like St0pid)
NEW QUESTION 17
......
P.S. Easily pass CEH-001 Exam with 878 Q&As Downloadfreepdf.net Dumps & pdf Version, Welcome to Download the Newest Downloadfreepdf.net CEH-001 Dumps: https://www.downloadfreepdf.net/CEH-001-pdf-download.html (878 New Questions)
- The Up To The Immediate Present Guide To CEH-001 Free Dumps
- The Secret Of GAQM CEH-001 Questions
- The Regenerate Guide To ISO-BCMS-22301 Vce
- How Many Questions Of CLSSGB Exam Question
- How Many Questions Of CEH-001 Test Questions
- The Secret Of GAQM CLSSGB Pdf Exam
- Leading Certified Lean Six Sigma Green Belt (CLSSGB) CLSSGB Sample Question
- Most Up-to-date Certified Ethical Hacker (CEH) CEH-001 Simulations
- Replace CSM-001 Free Practice Questions For Certified Scrum Master (CSM) Certification
- Printable GAQM CEH-001 Brain Dumps Online


