CEH-001 Exam Questions - Online Test
CEH-001 Premium VCE File

150 Lectures, 20 Hours
We provide real CEH-001 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass GAQM CEH-001 Exam quickly & easily. The CEH-001 PDF type is available for reading and printing. You can print more and practice many times. With the help of our GAQM CEH-001 dumps pdf and vce product and material, you can easily pass the CEH-001 exam.
GAQM CEH-001 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Your computer is infected by E-mail tracking and spying Trojan. This Trojan infects the computer with a single file - emos.sys
Which step would you perform to detect this type of Trojan?
- A. Scan for suspicious startup programs using msconfig
- B. Scan for suspicious network activities using Wireshark
- C. Scan for suspicious device drivers in c:\windows\system32\drivers
- D. Scan for suspicious open ports using netstat
Answer: C
NEW QUESTION 2
Exhibit: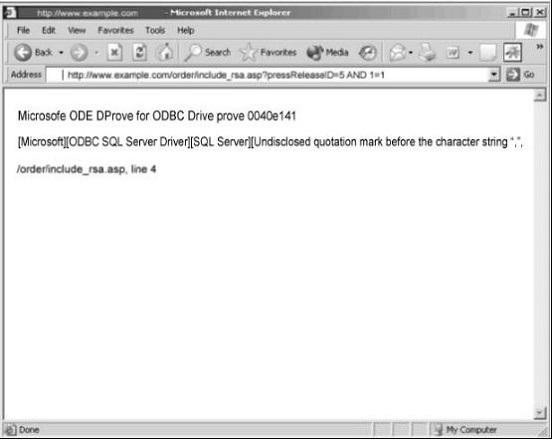
You are conducting pen-test against a company’s website using SQL Injection techniques. You enter “anuthing or 1=1-“ in the username filed of an authentication form. This is the output returned from the server.
What is the next step you should do?
- A. Identify the user context of the web application by running_ http://www.example.com/order/include_rsa_asp?pressReleaseID=5 ANDUSER_NAME() = ‘dbo’
- B. Identify the database and table name by running: http://www.example.com/order/include_rsa.asp?pressReleaseID=5 ANDascii(lower(substring((SELECT TOP 1 name FROM sysobjects WHERE xtype=’U’), 1))) > 109
- C. Format the C: drive and delete the database by running: http://www.example.com/order/include_rsa.asp?pressReleaseID=5 AND xp_cmdshell ‘format c: /q /yes ‘; drop database myDB; --
- D. Reboot the web server by running: http://www.example.com/order/include_rsa.asp?pressReleaseID=5AND xp_cmdshell ‘iisreset –reboot’; --
Answer: A
NEW QUESTION 3
Which of the following is a primary service of the U.S. Computer Security Incident Response Team (CSIRT)?
- A. CSIRT provides an incident response service to enable a reliable and trusted single point of contact for reporting computer security incidents worldwide.
- B. CSIRT provides a computer security surveillance service to supply a government with important intelligence information on individuals travelling abroad.
- C. CSIRT provides a penetration testing service to support exception reporting on incidents worldwide by individuals and multi-national corporations.
- D. CSIRT provides a vulnerability assessment service to assist law enforcement agencies with profiling an individual's property or company's asset.
Answer: A
NEW QUESTION 4
WWW wanderers or spiders are programs that traverse many pages in the World Wide Web by recursively retrieving linked pages. Search engines like Google, frequently spider web pages for indexing. How will you stop web spiders from crawling certain directories on your website?
- A. Place robots.txt file in the root of your website with listing of directories that you don't want to be crawled
- B. Place authentication on root directories that will prevent crawling from these spiders
- C. Enable SSL on the restricted directories which will block these spiders from crawling
- D. Place "HTTP:NO CRAWL" on the html pages that you don't want the crawlers to index
Answer: A
NEW QUESTION 5
A pentester is using Metasploit to exploit an FTP server and pivot to a LAN. How will the pentester pivot using Metasploit?
- A. Issue the pivot exploit and set the meterpreter.
- B. Reconfigure the network settings in the meterpreter.
- C. Set the payload to propagate through the meterpreter.
- D. Create a route statement in the meterpreter.
Answer: D
NEW QUESTION 6
Bob wants to prevent attackers from sniffing his passwords on the wired network. Which of the following lists the best options?
- A. RSA, LSA, POP
- B. SSID, WEP, Kerberos
- C. SMB, SMTP, Smart card
- D. Kerberos, Smart card, Stanford SRP
Answer: D
Explanation:
Kerberos, Smart cards and Stanford SRP are techniques where the password never leaves the computer.
NEW QUESTION 7
What is the primary drawback to using advanced encryption standard (AES) algorithm with a 256 bit key to share sensitive data?
- A. Due to the key size, the time it will take to encrypt and decrypt the message hinders
- B. efficient communication.
- C. To get messaging programs to function with this algorithm requires complex configurations.
- D. It has been proven to be a weak cipher; therefore, should not be trusted to protect sensitive data.
- E. It is a symmetric key algorithm, meaning each recipient must receive the key through a different channel than the message.
Answer: D
NEW QUESTION 8
John is using a special tool on his Linux platform that has a signature database and is therefore able to detect hundred of vulnerabilities in UNIX, Windows, and commonly-used web CGI scripts. Additionally, the database detects DDoS zombies and Trojans. What would be the name of this multifunctional tool?
- A. nmap
- B. hping
- C. nessus
- D. make
Answer: C
Explanation:
Nessus is the world's most popular vulnerability scanner, estimated to be used by over 75, 000 organizations world-wide. Nmap is mostly used for scanning, not for detecting vulnerabilities. Hping is a free packet generator and analyzer for the TCP/IP protocol and make is used to automatically build large applications on the *nix plattform.
NEW QUESTION 9
You are the security administrator for a large network. You want to prevent attackers from running any sort of traceroute into your DMZ and discovering the internal structure of publicly accessible areas of the network. How can you achieve this?
- A. There is no way to completely block tracerouting into this area
- B. Block UDP at the firewall
- C. Block TCP at the firewall
- D. Block ICMP at the firewall
Answer: A
NEW QUESTION 10
Which of the following techniques can be used to mitigate the risk of an on-site attacker from connecting to an unused network port and gaining full access to the network? (Choose three.)
- A. Port Security
- B. IPSec Encryption
- C. Network Admission Control (NAC)
- D. 802.1q Port Based Authentication
- E. 802.1x Port Based Authentication
- F. Intrusion Detection System (IDS)
Answer: ACE
NEW QUESTION 11
While testing the company's web applications, a tester attempts to insert the following test script into the search area on the company's web sitE.
<script>alert(" Testing Testing Testing ")</script>
Afterwards, when the tester presses the search button, a pop-up box appears on the screen with the text: "Testing Testing Testing". Which vulnerability has been detected in the web application?
- A. Buffer overflow
- B. Cross-site request forgery
- C. Distributed denial of service
- D. Cross-site scripting
Answer: D
NEW QUESTION 12
Which of the following Exclusive OR transforms bits is NOT correct?
- A. 0 xor 0 = 0
- B. 1 xor 0 = 1
- C. 1 xor 1 = 1
- D. 0 xor 1 = 1
Answer: C
NEW QUESTION 13
On a Linux device, which of the following commands will start the Nessus client in the background so that the Nessus server can be configured?
- A. nessus +
- B. nessus *s
- C. nessus &
- D. nessus -d
Answer: C
NEW QUESTION 14
Which of the following is NOT part of CEH Scanning Methodology?
- A. Check for Live systems
- B. Check for Open Ports
- C. Banner Grabbing
- D. Prepare Proxies
- E. Social Engineering attacks
- F. Scan for Vulnerabilities
- G. Draw Network Diagrams
Answer: E
NEW QUESTION 15
Eve decides to get her hands dirty and tries out a Denial of Service attack that is relatively new to her. This time she envisages using a different kind of method to attack Brownies Inc. Eve tries to forge the packets and uses the broadcast address. She launches an attack similar to that of fraggle. What is the technique that Eve used in the case above?
- A. Smurf
- B. Bubonic
- C. SYN Flood
- D. Ping of Death
Answer: A
Explanation:
A fraggle attack is a variation of the smurf attack for denial of service in which the attacker sends spoofed UDP packets instead of ICMP echo reply (ping) packets to the broadcast address of a large network.
NEW QUESTION 16
Anonymizer sites access the Internet on your behalf, protecting your personal information from disclosure. An anonymizer protects all of your computer's identifying information while it surfs for you, enabling you to remain at least one step removed from the sites you visit.
You can visit Web sites without allowing anyone to gather information on sites visited by you. Services that provide anonymity disable pop-up windows and cookies, and conceal visitor's IP address.
These services typically use a proxy server to process each HTTP request. When the user requests a Web page by clicking a hyperlink or typing a URL into their browser, the service retrieves and displays the information using its own server. The remote server (where the requested Web page resides) receives information on the anonymous Web surfing service in place of your information.
In which situations would you want to use anonymizer? (Select 3 answers)
- A. Increase your Web browsing bandwidth speed by using Anonymizer
- B. To protect your privacy and Identity on the Internet
- C. To bypass blocking applications that would prevent access to Web sites or parts of sites that you want to visit.
- D. Post negative entries in blogs without revealing your IP identity
Answer: BCD
NEW QUESTION 17
......
P.S. Easily pass CEH-001 Exam with 878 Q&As Dumpscollection.com Dumps & pdf Version, Welcome to Download the Newest Dumpscollection.com CEH-001 Dumps: https://www.dumpscollection.net/dumps/CEH-001/ (878 New Questions)
- The Rebirth Guide To CEH-001 Exam Topics
- Replace CSM-001 Free Practice Questions For Certified Scrum Master (CSM) Certification
- The Secret Of GAQM CLSSGB Pdf Exam
- Printable GAQM CEH-001 Brain Dumps Online
- How Many Questions Of CEH-001 Test Questions
- Most Up-to-date Certified Ethical Hacker (CEH) CEH-001 Simulations
- How Many Questions Of CLSSGB Exam Question
- The Up To The Immediate Present Guide To CEH-001 Free Dumps
- Leading Certified Lean Six Sigma Green Belt (CLSSGB) CLSSGB Sample Question
- The Secret Of GAQM CEH-001 Questions


