CEH-001 Exam Questions - Online Test
CEH-001 Premium VCE File

150 Lectures, 20 Hours
Act now and download your GAQM CEH-001 test today! Do not waste time for the worthless GAQM CEH-001 tutorials. Download Most recent GAQM Certified Ethical Hacker (CEH) exam with real questions and answers and begin to learn GAQM CEH-001 with a classic professional.
Online GAQM CEH-001 free dumps demo Below:
NEW QUESTION 1
A circuit level gateway works at which of the following layers of the OSI Model?
- A. Layer 5 - Application
- B. Layer 4 – TCP
- C. Layer 3 – Internet protocol
- D. Layer 2 – Data link
Answer: B
NEW QUESTION 2
BankerFox is a Trojan that is designed to steal users' banking data related to certain banking entities.
When they access any website of the affected banks through the vulnerable Firefox 3.5 browser, the Trojan is activated and logs the information entered by the user. All the information entered in that website will be logged by the Trojan and transmitted to the attacker's machine using covert channel.
BankerFox does not spread automatically using its own means. It needs an attacking user's intervention in order to reach the affected computer.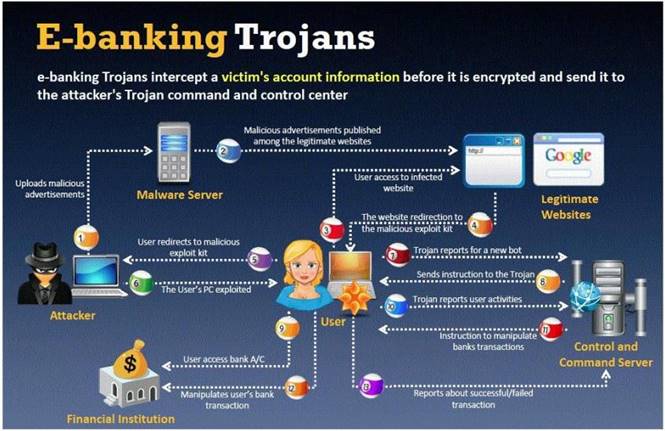
What is the most efficient way an attacker located in remote location to infect this banking Trojan on a victim's machine?
- A. Physical access - the attacker can simply copy a Trojan horse to a victim's hard disk infecting the machine via Firefox add-on extensions
- B. Custom packaging - the attacker can create a custom Trojan horse that mimics the appearance of a program that is unique to that particular computer
- C. Custom packaging - the attacker can create a custom Trojan horse that mimics the appearance of a program that is unique to that particular computer
- D. Custom packaging - the attacker can create a custom Trojan horse that mimics the appearance of a program that is unique to that particular computer
- E. Downloading software from a website? An attacker can offer free software, such as shareware programs and pirated mp3 files
Answer: E
NEW QUESTION 3
An Evil Cracker is attempting to penetrate your private network security. To do this, he must not be seen by your IDS, as it may take action to stop him. What tool might he use to bypass the IDS?
Select the best answer.
- A. Firewalk
- B. Manhunt
- C. Fragrouter
- D. Fragids
Answer: C
Explanation:
Explanations:
Firewalking is a way to disguise a portscan. Thus, firewalking is not a tool, but a method of
conducting a port scan in which it can be hidden from some firewalls. Synamtec Man-Hunt is an IDS, not a tool to evade an IDS.
Fragrouter is a tool that can take IP traffic and fragment it into multiple pieces. There is a legitimate reason that fragmentation is done, but it is also a technique that can help an attacker to evade detection while Fragids is a made-up tool and does not exist.
NEW QUESTION 4
Which method can provide a better return on IT security investment and provide a thorough and comprehensive assessment of organizational security covering policy, procedure design, and implementation?
- A. Penetration testing
- B. Social engineering
- C. Vulnerability scanning
- D. Access control list reviews
Answer: A
NEW QUESTION 5
The intrusion detection system at a software development company suddenly generates multiple alerts regarding attacks against the company's external webserver, VPN concentrator, and DNS servers. What should the security team do to determine which alerts to check first?
- A. Investigate based on the maintenance schedule of the affected systems.
- B. Investigate based on the service level agreements of the systems.
- C. Investigate based on the potential effect of the incident.
- D. Investigate based on the order that the alerts arrived in.
Answer: C
NEW QUESTION 6
A hacker searches in Google for filetype:pcf to find Cisco VPN config files. Those files may contain connectivity passwords that can be decoded with which of the following?
- A. Cupp
- B. Nessus
- C. Cain and Abel
- D. John The Ripper Pro
Answer: C
NEW QUESTION 7
Which of the following is a client-server tool utilized to evade firewall inspection?
- A. tcp-over-dns
- B. kismet
- C. nikto
- D. hping
Answer: A
NEW QUESTION 8
To scan a host downstream from a security gateway, Firewalking:
- A. Sends a UDP-based packet that it knows will be blocked by the firewall to determine how specifically the firewall responds to such packets
- B. Uses the TTL function to send packets with a TTL value set to expire one hop past the identified security gateway
- C. Sends an ICMP ''administratively prohibited'' packet to determine if the gateway will drop the packet without comment.
- D. Assesses the security rules that relate to the target system before it sends packets to any hops on the route to the gateway
Answer: B
Explanation:
Firewalking uses a traceroute-like IP packet analysis to determine whether or not a particular packet can pass from the attacker’s host to a destination host through a packet-filtering device. This technique can be used to map ‘open’ or ‘pass through’ ports on a gateway. More over, it can determine whether packets with various control information can pass through a given gateway.
NEW QUESTION 9
Liza has forgotten her password to an online bookstore. The web application asks her to key in her email so that they can send her the password. Liza enters her email liza@yahoo.com'. The application displays server error. What is wrong with the web application?
- A. The email is not valid
- B. User input is not sanitized
- C. The web server may be down
- D. The ISP connection is not reliable
Answer: B
Explanation:
All input from web browsers, such as user data from HTML forms and cookies, must be stripped of special characters and HTML tags as described in the following CERT advisories:
http://www.cert.org/advisories/CA-1997-25.html http://www.cert.org/advisories/CA-2000-02.html
NEW QUESTION 10
Clive is conducting a pen-test and has just port scanned a system on the network. He has identified the operating system as Linux and been able to elicit responses from ports 23, 25 and 53. He infers port 23 as running Telnet service, port 25 as running SMTP service and port 53 as running DNS service. The client confirms these findings and attests to the current availability of the services. When he tries to telnet to port 23 or 25, he gets a blank screen in response. On typing other commands, he sees only blank spaces or underscores symbols on the screen. What are you most likely to infer from this?
- A. The services are protected by TCP wrappers
- B. There is a honeypot running on the scanned machine
- C. An attacker has replaced the services with trojaned ones
- D. This indicates that the telnet and SMTP server have crashed
Answer: A
Explanation:
TCP Wrapper is a host-based network ACL system, used to filter network access to Internet protocol services run on (Unix-like) operating systems such as Linux or
BSD. It allows host or subnetwork IP addresses, names and/or ident query replies, to be used as tokens on which to filter for access control purposes.
NEW QUESTION 11
Sandra is conducting a penetration test for XYZ.com. She knows that XYZ.com is using wireless networking for some of the offices in the building right down the street. Through social engineering she discovers that they are using 802.11g. Sandra knows that 802.11g uses the same 2.4GHz frequency range as 802.11b. Using NetStumbler and her 802.11b wireless NIC, Sandra drives over to the building to map the wireless networks. However, even though she repositions herself around the building several times, Sandra is not able to detect a single AP.
What do you think is the reason behind this?
- A. Netstumbler does not work against 802.11g.
- B. You can only pick up 802.11g signals with 802.11a wireless cards.
- C. The access points probably have WEP enabled so they cannot be detected.
- D. The access points probably have disabled broadcasting of the SSID so they cannot be detected.
- E. 802.11g uses OFDM while 802.11b uses DSSS so despite the same frequency and 802.11b card cannot see an 802.11g signal.
- F. Sandra must be doing something wrong, as there is no reason for her to not see the signals.
Answer: E
NEW QUESTION 12
Clive has been hired to perform a Black-Box test by one of his clients.
How much information will Clive obtain from the client before commencing his test?
- A. IP Range, OS, and patches installed.
- B. Only the IP address range.
- C. Nothing but corporate name.
- D. All that is available from the client site.
Answer: C
Explanation:
Penetration tests can be conducted in one of two ways: black-box (with no prior knowledge the infrastructure to be tested) or white-box (with complete knowledge of the infrastructure to be tested). As you might expect, there are conflicting opinions about this choice and the value that either approach will bring to a project.
NEW QUESTION 13
This attack technique is used when a Web application is vulnerable to an SQL Injection but the results of the Injection are not visible to the attacker.
- A. Unique SQL Injection
- B. Blind SQL Injection
- C. Generic SQL Injection
- D. Double SQL Injection
Answer: B
NEW QUESTION 14
To see how some of the hosts on your network react, Winston sends out SYN packets to an IP range. A number of IPs respond with a SYN/ACK response. Before the connection is established he sends RST packets to those hosts to stop the session. Winston has done this to see how his intrusion detection system will log the traffic. What type of scan is Winston attempting here?
- A. Winston is attempting to find live hosts on your company's network by using an XMAS scan.
- B. He is utilizing a SYN scan to find live hosts that are listening on your network.
- C. This type of scan he is using is called a NULL scan.
- D. He is using a half-open scan to find live hosts on your network.
Answer: D
NEW QUESTION 15
Fingerprinting an Operating System helps a cracker because:
- A. It defines exactly what software you have installed
- B. It opens a security-delayed window based on the port being scanned
- C. It doesn't depend on the patches that have been applied to fix existing security holes
- D. It informs the cracker of which vulnerabilities he may be able to exploit on your system
Answer: D
Explanation:
When a cracker knows what OS and Services you use he also knows which exploits might work on your system. If he would have to try all possible exploits for all possible Operating Systems and Services it would take too long time and the possibility of being detected increases.
NEW QUESTION 16
Use the traceroute results shown above to answer the following question: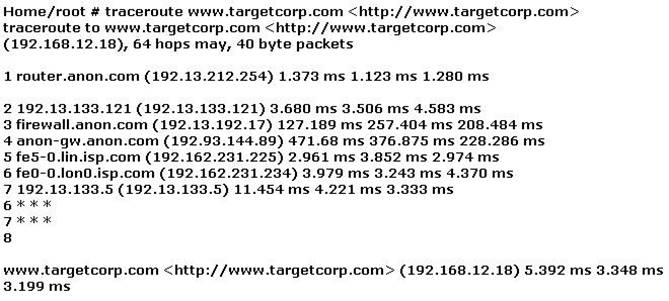
The perimeter security at targetcorp.com does not permit ICMP TTL-expired packets out.
- A. True
- B. False
Answer: A
Explanation:
As seen in the exhibit there is 2 registrations with timeout, this tells us that the firewall filters packets where the TTL has reached 0, when you continue with higher starting values for TTL you will get an answer from the target of the traceroute.
NEW QUESTION 17
......
100% Valid and Newest Version CEH-001 Questions & Answers shared by Dumpscollection.com, Get Full Dumps HERE: https://www.dumpscollection.net/dumps/CEH-001/ (New 878 Q&As)
- How Many Questions Of CLSSGB Exam Question
- The Up To The Immediate Present Guide To CEH-001 Free Dumps
- Most Up-to-date Certified Ethical Hacker (CEH) CEH-001 Simulations
- The Secret Of GAQM CLSSGB Pdf Exam
- How Many Questions Of CEH-001 Test Questions
- The Secret Of GAQM CEH-001 Questions
- Printable GAQM CEH-001 Brain Dumps Online
- The Rebirth Guide To CEH-001 Exam Topics
- The Regenerate Guide To ISO-BCMS-22301 Vce
- Replace CSM-001 Free Practice Questions For Certified Scrum Master (CSM) Certification


