210-255 Exam Questions - Online Test
210-255 Premium VCE File

150 Lectures, 20 Hours
Testking 210-255 Questions are updated and all 210-255 answers are verified by experts. Once you have completely prepared with our 210-255 exam prep kits you will be ready for the real 210-255 exam without a problem. We have Most recent Cisco 210-255 dumps study guide. PASSED 210-255 First attempt! Here What I Did.
Free 210-255 Demo Online For Cisco Certifitcation:
NEW QUESTION 1
Refer to the exhibit.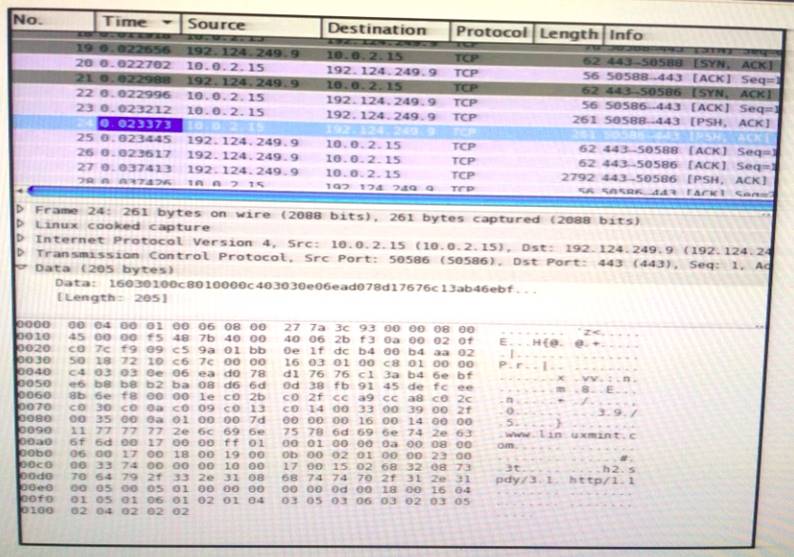
Which application protocol is in this PCAP file?
- A. TCP
- B. SSH
- C. HTTP
- D. SSL
Answer: D
Explanation:
If we are looking at the OSI model then SSL/TLS would sit at the presentation layer as it provides
encryption services, but SSL/TLS also establishes an encrypted communication session therefore SSL/TLS is also seen as part of session layer (layer 5 of the OSI model). It will also guarantee the authenticity of a Server by properly authenticating the required authentication challenges. Authentication works at Layer 7.If we are referring to the TCP/IP model, then it is entirely acceptable that SSL is seen as an application layer protocol as layers 5,6 & 7 of the OSI are mapped to the Application layer in TCP/IP model.TCP is not an application layer protocol – it is seen as the Transport layer protocol in both models.
NEW QUESTION 2
Which HTTP header field is usually used in forensics to identify the type of browser used?
- A. accept-language
- B. user-agent
- C. referrer
- D. host
Answer: B
NEW QUESTION 3
Which file is allocated with 32 bits?
- A. NTFS
- B. FAT32
- C. FAT
- D. ExFAT
Answer: D
NEW QUESTION 4
Which type verification typically consists of using tools to compute the message digest of the original and copies data, then comparing the digests to make sure that they are the same?
- A. evidence collection order
- B. data integrity
- C. data preservation
- D. volatile data collection
Answer: B
NEW QUESTION 5
Which of the following is not an example of the VERIS main schema categories?
- A. Incident tracking
- B. Victim demographics
- C. Incident descriptions
- D. Incident forensics ID
Answer: D
NEW QUESTION 6
Which expression creates a filter on a host IP address or name?
- A. [src|dst] host <host >
- B. [tcp|udp] [src|dst] port<port>
- C. ether [src|dst] host<ehost>
- D. gateway host <host>
Answer: A
Explanation:
https://www.wireshark.org/docs/wsug_html_chunked/ChCapCaptureFilterSection.html
NEW QUESTION 7
Which information must be left out of a final incident report?
- A. server hardware configurations
- B. exploit or vulnerability used
- C. impact and/or the financial loss
- D. how the incident was detected
Answer: A
NEW QUESTION 8
Which regular expression matches "color" and "colour"?
- A. col[0-9]+our
- B. colo?ur
- C. colou?r
- D. ]a-z]{7}
Answer: C
NEW QUESTION 9
Which option is unnecessary for determining the appropriate containment strategy according to NIST.SP800-61 r2?
- A. effectiveness of the strategy
- B. time and resource needed to implement the strategy
- C. need for evidence preservation
- D. attack vector used to compromise the system
Answer: D
NEW QUESTION 10
Refer to the Exhibit.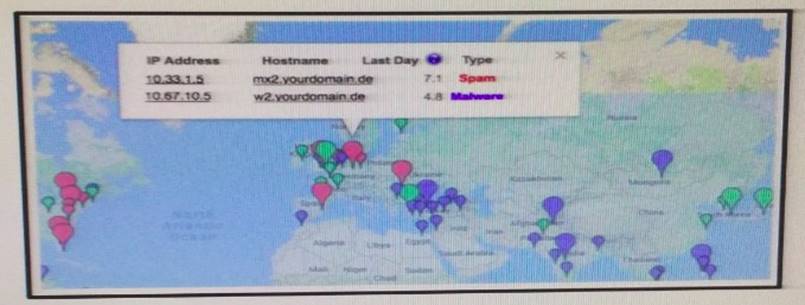
A customer reports that they cannot access your organization's website. Which option is a possible reason that the customer cannot access the website?
- A. The server at 10.33.1.5 is using up too much bandwidth causing a denial- of-service.
- B. The server at 10.67.10.5 has a virus.
- C. A vulnerability scanner has shown that 10.67.10.5 has been compromised.
- D. Web traffic sent from 10.67.10.5 has been identified as malicious by Internet sensors.
Answer: D
Explanation:
Every firewall has its own database where it maintains the website reputation on terms of security, ease of access, performance etc and below certain score (generally 7 in case of Cisco), firewalls block access to the sites. For example, you can visit www.senderbase.org and enter name of any website and you will see the reputation of that website.
NEW QUESTION 11
Which type of analysis assigns values to scenarios to see what the outcome might be in each scenario?
- A. deterministic
- B. exploratory
- C. probabilistic
- D. descriptive
Answer: A
Explanation:
Deterministic Versus Probabilistic Analysis
In deterministic analysis, all data used for the analysis is known beforehand. Probabilistic analysis, on the other hand, is done assuming the likelihood that something will or has happened, but you don’t know exactly when or how.
Probabilistic methods institute powerful tools for use in many kinds of decision-making problems—in this case, cybersecurity event analysis. In this type of analysis, the analysis components suggest a “probabilistic Answer” to the results of the investigation, which is not a definitive result.
Deterministic analysis, you know and obtain “facts” about the incident, breach, affected applications, and so on. For instance, by analyzing applications using port-based analysis and similar methods, you can assume that the process is deterministic—especially when applications conform to the specifications of the standards.
NEW QUESTION 12
Which of the following are examples of some of the responsibilities of a corporate CSIRT and the policies it helps create? (Select all that apply.)
- A. Scanning vendor customer networks
- B. Incident classification and handling
- C. Information classification and protection
- D. Information dissemination
- E. Record retentions and destruction
Answer: BCDE
NEW QUESTION 13
Which CVSS metric describes the conditions that are beyond the attackers control so that an attack can be successful?
- A. User interaction
- B. Attack vector
- C. attack complexity
- D. privileges required
Answer: C
NEW QUESTION 14
When incident data is collected, it is important that evidentiary cross-contamination is prevented. How is this accomplished?
- A. by allowing unrestricted access to impacted devices
- B. by not allowing items of evidence to physically touch
- C. by ensuring power is removed to all devices involved
- D. by not permitting a device to store evidence if it is the evidence itself.
Answer: D
NEW QUESTION 15
Which Security Operations Center's goal is to provide incident handling to a country?
- A. Coordination Center
- B. Internal CSIRT
- C. National CSIRT
- D. Analysis Center
Answer: C
NEW QUESTION 16
Which analyzing technique describe the outcome as well as how likely each outcome is?
- A. deterministic
- B. exploratory
- C. probabilistic
- D. descriptive
Answer: C
NEW QUESTION 17
Refer to the exhibit.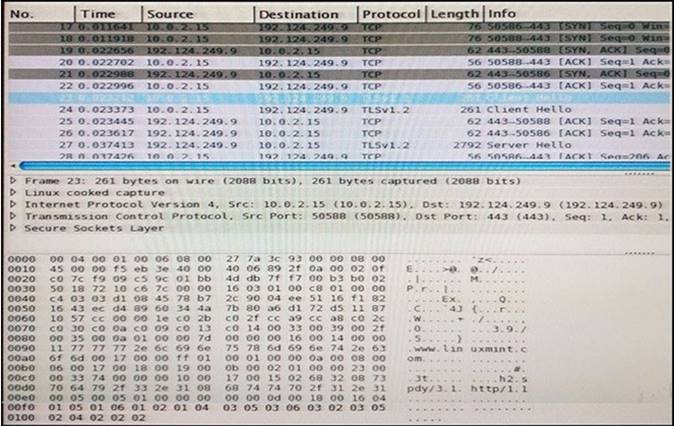
Refer to the exhibit. Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Source address, source port, destination port, destination address, transport protocol, network protocol, application protocol.
NEW QUESTION 18
Which CVSSv3 metric value increases when attacks consume network bandwidth, processor cycles, or disk space?
- A. confidentiality
- B. integrity
- C. availability
- D. complexity
Answer: C
Explanation:
Availability Impact (A): This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability. While the confidentiality and integrity impact metrics apply to the loss of confidentiality or integrity of data such as information and files used by the impacted component, this metric refers to the loss of availability of the impacted component itself, such as a networked service such as web, database, and email. Because availability refers to the accessibility of information resources, attacks that consume network bandwidth, processor cycles, or disk space all impact the availability of an impacted component.
NEW QUESTION 19
What is the process of remediation the network and systems and/or reconstructing so the responsible threat actor can be revealed?
- A. Data analysis
- B. Assets distribution
- C. Evidence collection
- D. Threat actor distribution
Answer: A
NEW QUESTION 20
Which of the following is not an example of reconnaissance?
- A. Searching the robots.txt file
- B. Redirecting users to a source and scanning traffic to learn about the target
- C. Scanning without completing the three-way handshake
- D. Communicating over social media
Answer: B
NEW QUESTION 21
Which file system has 32 bits assigned to the address clusters of the allocation table?
- A. FAT32
- B. NTFS
- C. EXT4
- D. FAT16
Answer: A
NEW QUESTION 22
......
Thanks for reading the newest 210-255 exam dumps! We recommend you to try the PREMIUM Exambible 210-255 dumps in VCE and PDF here: https://www.exambible.com/210-255-exam/ (160 Q&As Dumps)
- All About Precise 300-135 dumps
- A Review Of High quality 200-355 practice test
- What Vivid 300-070 exam dumps Is?
- Up to date Cisco 400-101 examcollection
- Verified CCNP Collaboration 300-075 dumps
- The Avant-garde Guide To 100-105 exam dumps
- Renew Cisco 300-101 exam
- 10 Tips For Latest 300-115 dumps
- All About High Quality 300-510 Exam
- Tested 400-151 Dumps Questions 2021


