H12-711_V3.0 Exam Questions - Online Test
H12-711_V3.0 Premium VCE File

150 Lectures, 20 Hours
Proper study guides for Rebirth HUAWEI HCIA-Security V3.0 certified begins with HUAWEI H12-711_V3.0 preparation products which designed to deliver the Free H12-711_V3.0 questions by making you pass the H12-711_V3.0 test at your first time. Try the free H12-711_V3.0 demo right now.
Check H12-711_V3.0 free dumps before getting the full version:
NEW QUESTION 1
If there is no hard disk installed on the firewall, when a network intrusion event is found, the event will be recorded in the () log. (fill in the blank)
Solution:
Logbuffer
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 2
Social engineering is a means of harm such as deception, harm, etc., through psychological traps such as psychological weaknesses, instinctive reactions, curiosity, trust, and greed of victims.
- A. True
- B. False
Answer: A
NEW QUESTION 3
Please match the whole worm attack process and attack description.[fill in the blank]*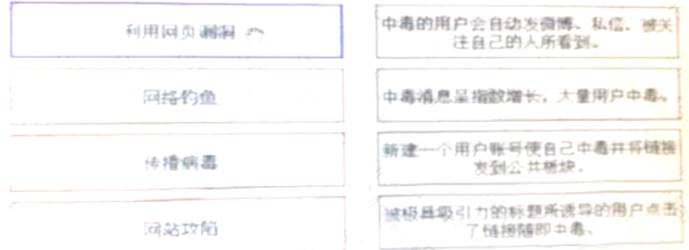
Solution:
Exploiting web page loopholes: Create a new user account to poison yourself and post the link to the public section, Phishing: Users induced by attractive titles click on the link and then get poisoned, and rebroadcast the virus: Poisoned users will automatically post Weibo , private messages, and are seen by people who follow them. Website compromise: Poisoning news is growing exponentially. A large number of users are poisoned)
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 4
againstARPDescription of spoofing attack, which of the following is false
- A. ARPThe implementation mechanism only considers normal business interactions, and does not perform any verification on abnormal business interactions or malicious behaviors
- B. ARPSpoofing attacks can only be done byARPReply to achieve, can not passARPrequest fulfillment
- C. When a host sends normalARPWhen the request is made, the attacker will preemptively answer, causing the host to establish an erroneousIPandMACMapping relations
- D. ARPStatic binding is the solutionARPA scheme of spoofing attack, mainly used in scenarios with small network scale
Answer: B
NEW QUESTION 5
The steps of the security assessment method do not include which of the following?
- A. Manual audit
- B. Penetration testing
- C. Questionnaire
- D. data analysis
Answer: D
NEW QUESTION 6
The digital certificate fairs the public key through a third-party organization, thereby ensuring the
non-repudiation of data transmission. Therefore, to confirm the correctness of the public key, only the certificate of the communicating party is required.
- A. True
- B. False
Answer: B
NEW QUESTION 7
Digital envelope technology means that the sender uses the receiver's public key to encrypt the data, and then sends the ciphertext to the receiver ( )[Multiple choice]*
- A. TRUE
- B. FALSE
Answer: B
NEW QUESTION 8
existClient-Initiated VPNDuring the configuration, it is generally recommended to plan the address pool and the headquarters network address as different network segments. Otherwise, the proxy forwarding function needs to be enabled on the gateway device.
- A. True
- B. False
Answer: B
NEW QUESTION 9
The reason why NAPT can realize one-to-many address translation is that the ______ is also translated when the address is translated, so multiple private addresses can share the same public address.[fill in the blank]*
Solution:
port
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 10
Which of the following options are correct regarding configuring firewall security zones? (multiple choice)
- A. The firewall has four security zones by default, and the priority of the four security zones cannot be modified
- B. A firewall can have up to12safe area
- C. Firewall can create two security zones of the same priority
- D. When data flows between different security zones, the security check of the device will be triggered and the corresponding security policy will be implemented
Answer: AD
NEW QUESTION 11
______ - The goal is to provide a rapid, composed and effective response in emergency situations, thereby enhancing the ability of the business to recover immediately from a disruptive event.[fill in the blank]*
Solution:
business continuity plan
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 12
About firewall gateways forHTTPWhich of the following statements is false about the protocol's antivirus response?
- A. When the gateway device blocksHTTPAfter connecting, push to the clientwebpage and generate log
- B. Response methods include announcement and blocking
- C. In alarm mode, the device only generates logs, which is not correct.HTTPThe files transmitted by the protocol are processed and sent out
- D. Blocking means that the device is disconnected from theHTTPserver connection and block file transfer
Answer: B
NEW QUESTION 13
According to the logical architecture of the HiSec solution, please drag the HiSec solutions on the left to the right box and arrange them in order from top to bottom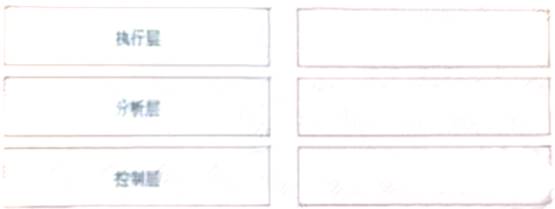
Solution:
analyzers, controllers, actuators
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 14
Which of the following options is not part of the quintuple range?
- A. sourceIP
- B. sourceMAC
- C. PurposeIP
- D. destination port
Answer: B
NEW QUESTION 15
Which of the following descriptions about digital fingerprints in digital signatures is wrong?
- A. The receiver needs to use the sender's public key to unlock the digital signature to obtain the digital fingerprint.
- B. It is the data obtained by the sender after calculating the plaintext information through the HASH algorithm.
- C. The receiver will use the sender's public key to calculate the generated data fingerprint and compare it with the received digital fingerprint.
- D. Digital fingerprints are also known as information digests.
Answer: C
NEW QUESTION 16
Digital certificate technology solves the problem that the public key owner cannot be determined in digital signature technology
- A. True
- B. False
Answer: A
NEW QUESTION 17
Evidence identification needs to address the verification of the integrity of the evidence and determine whether it meets the applicable standards. Which of the following statements is correct about the criteria for identification of evidence?
- A. The relevance standard means that if the telephony evidence can have a substantial impact on the facts of the case to a certain extent, the court should rule that it is relevant.
- B. The standard of objectivity means that the acquisition, storage, and submission of electronic evidence should be legal, and not constitute a serious violation of basic rights such as national interests, social welfare, and personal privacy.
- C. The standard of legality is to ensure that the content of electronic evidence remains unchanged from the initial acquisition and collection to the submission and use as litigation evidence.
- D. The standard of fairness refers to the evidentiary material obtained by the legal subject through legal means, which has evidential capacity.
Answer: A
NEW QUESTION 18
Digital certificates can be divided into local certificates,CACertificates, root certificates, self-signed certificates, etc.
- A. True
- B. False
Answer: A
NEW QUESTION 19
Drag the warning level of the network security emergency response on the left into the box on the right, and arrange it from top to bottom in order of severity.[fill in the blank]*
Solution:
3124
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 20
......
Recommend!! Get the Full H12-711_V3.0 dumps in VCE and PDF From Dumps-hub.com, Welcome to Download: https://www.dumps-hub.com/H12-711_V3.0-dumps.html (New 492 Q&As Version)
- What Download H12-811_V1.0 Free Exam Questions Is
- The Abreast Of The Times Guide To H12-711_V3.0 Testing Material
- All About 100% Guarantee H12-711_V3.0 Exam Engine
- HUAWEI H12-211 Dumps Questions 2021
- The Renew Guide To H12-711_V3.0 Braindumps
- A Review Of Refined H12-811_V1.0 Training Tools
- Pinpoint H19-301 Preparation 2021
- HUAWEI H12-211 Braindumps 2021
- The Secret Of HUAWEI H12-811_V1.0 Free Practice Test
- What Exact H12-811_V1.0 Question Is


