H12-711_V3.0 Exam Questions - Online Test
H12-711_V3.0 Premium VCE File

150 Lectures, 20 Hours
It is more faster and easier to pass the HUAWEI H12-711_V3.0 exam by using Pinpoint HUAWEI HCIA-Security V3.0 questuins and answers. Immediate access to the Most recent H12-711_V3.0 Exam and find the same core area H12-711_V3.0 questions with professionally verified answers, then PASS your exam with a high score now.
Online H12-711_V3.0 free questions and answers of New Version:
NEW QUESTION 1
Which of the following is the correct order for incident response management?
* 1. detect
* 2. Report
* 3. ease
* 4. Lessons Learned
* 5. repair
* 6. recover
* 7. response
- A. 1-3-2-7-5-6-4
- B. 1-3-2-7-6-5-4
- C. 1-2-3-7-6-5-4
- D. 1-7-3-2-6-5-4
Answer: D
NEW QUESTION 2
Which of the following statements about electronic evidence sources is false?
- A. Facsimile data and mobile phone recordings are electronic evidence related to communication technology.
- B. Movies and TV series are electronic evidence related to network technology.
- C. Database operation records and operating system logs are electronic evidence related to computers•
- D. OS logs,e-mail, chat records can be used as a source of electronic evidence
Answer: B
NEW QUESTION 3
Vulnerabilities that have not yet been discovered are0 dayVulnerability
- A. True
- B. False
Answer: B
NEW QUESTION 4
An enterprise wants to build a server system and requires the following functions: 1. The enterprise needs to have its own dedicated mailbox, and the sending and receiving of emails needs to go through the enterprise's server; 2. The server must provide file transfer and access services. Users in different departments of the enterprise provide accounts with different permissions: 3. When the enterprise accesses the internal webpage of the enterprise, the enterprise can directly enter the domain name in the browser to access. To meet the above requirements, which of the following servers do enterprises need to deploy? ( )*
- A. Time synchronization server
- B. FTP server (I)
- C. DNS server
- D. Mail server
Answer: BCD
NEW QUESTION 5
aboutNATThe configuration commands for the address pool are as follows:no-patThe meaning of the parameters is: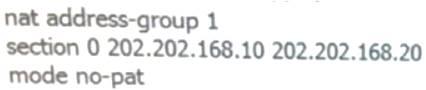
- A. no address translation
- B. port multiplexing
- C. Do not translate source ports
- D. Do not convert destination port
Answer: C
NEW QUESTION 6
Which of the following options areSSL VPNfunction? (multiple choice)
- A. User Authentication
- B. port scan
- C. File Sharing
- D. WEBrewrite
Answer: AC
NEW QUESTION 7
aboutVGMPDescription of the managed preemption function, which of the following is false?
- A. By default,VGMPThe preemption function of the management group is enabled
- B. By default,VGMPThe preemption delay time of the management group is40s
- C. Preemption means that when the original faulty master device recovers, its priority will be restore
- D. At this time, it can preempt its own state as the master device again.
- E. whenVRRPBackup group added toVGMPAfter managing the group,VRRPThe original preemption function on the backup group fails
Answer: B
NEW QUESTION 8
Execute the command on the firewall and display the above information. Which of the following descriptions is correct? (multiple choice)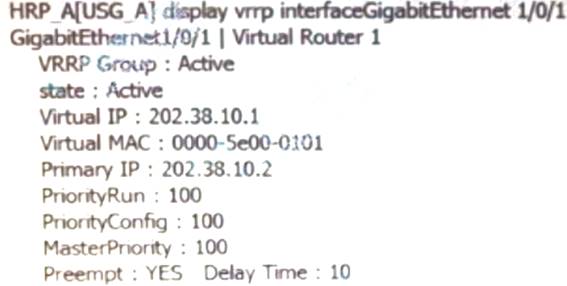
- A. this firewallVGMPgroup status isActive
- B. this firewallG1/0/1virtual interfaceIPaddress is202.38.10.2
- C. this firewallVRIDfor1ofVRRPThe priority of the backup group is100
- D. When the main deviceUSG_AWill not switch in the event of a failure
Answer: ABC
NEW QUESTION 9
In the ______ view of the firewall, you can use the reboot command to restart the firewall.[fill in the blank]*
Solution:
user
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 10
Which of the following options is correct regarding the matching conditions of a security policy? (multiple choice)
- A. matching condition"source security zone"is an optional parameter
- B. matching condition"period"is an optional parameter
- C. matching condition"application"is an optional parameter
- D. matching condition"Serve"is an optional parameter
Answer: ABCD
NEW QUESTION 11
In the TCP/P protocol core, which of the following protocols works at the application layer? ( )[Multiple choice]*
- A. IGMP
- B. ICMP
- C. RIP
- D. ARP
Answer: C
NEW QUESTION 12
When the user uses the session authentication method to trigger the firewall built-inPortalDuring authentication, users do not actively perform identity authentication, advanced service access, and device push"redirect"to the certification page
- A. True
- B. False
Answer: A
NEW QUESTION 13
Which of the following does not belong to the log format of the firewall? ( )[Multiple choice]
- A. binary format
- B. netflow format
- C. ASCII encoding format
- D. Syslog format
Answer: C
NEW QUESTION 14
Digital envelope technology means that the sender uses the receiver's public key to encrypt the data and then sends the ciphertext to the receiver.
- A. True
- B. False
Answer: A
NEW QUESTION 15
The direction of the traffic can be seen in the _____ of the firewall.[fill in the blank]*
Solution:
session table
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
Which of the following security measures does the monitor correspond to?
- A. Intrusion Detection System
- B. Encrypted VPN
- C. Access control system
- D. Firewall
Answer: A
NEW QUESTION 17
Which of the following is true about the security policy configuration command?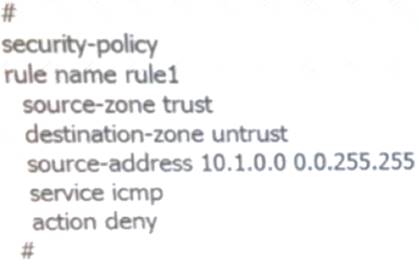
- A. prohibited fromtrustRegional accessuntrustarea and the destination address is 10.1.10.10hostICMPmessage
- B. prohibited fromtrustRegional accessuntrustarea and the destination address is10.1.0.0/16All hosts on the segmentICMPmessage
- C. prohibited fromtrustRegional accessuntrustregion and the source address is10.1.0.0/16All hosts from the network segmentICMPmessage
- D. prohibited fromtrustRegional accessuntrustregion and the source address is10.2.10.10All hosts from hostICMPmessage
Answer: C
NEW QUESTION 18
The trigger modes of the Portali authentication built in the firewall include pre-authentication and ( ) authentication. (fill in the blank)
Solution:
Conversation
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 19
aboutAHandESPSecurity protocol, which of the following options is true? (multiple choice)
- A. AHCan provide encryption and authentication functions
- B. ESPCan provide encryption and authentication functions
- C. AH The protocol number is51
- D. ESPThe protocol number is51
Answer: BC
NEW QUESTION 20
......
Recommend!! Get the Full H12-711_V3.0 dumps in VCE and PDF From Downloadfreepdf.net, Welcome to Download: https://www.downloadfreepdf.net/H12-711_V3.0-pdf-download.html (New 492 Q&As Version)
- The Update Guide To H19-308 Test Engine
- The Updated Guide To H12-221 Actual Exam
- A Review Of Simulation H12-811_V1.0 Prep
- Best Quality H12-211 Exam Questions 2021
- Replace H12-311 Courses 2021
- What High Quality H12-811_V1.0 Actual Exam Is
- A Review Of Virtual H12-711 Answers
- Pinpoint H19-301 Preparation 2021
- The Renew Guide To H12-711_V3.0 Braindumps
- How Many Questions Of H12-811_V1.0 Exam Question


