GSNA Exam Questions - Online Test
GSNA Premium VCE File

150 Lectures, 20 Hours
Pass4sure offers free demo for GSNA exam. "GIAC Systems and Network Auditor", also known as GSNA exam, is a GIAC Certification. This set of posts, Passing the GIAC GSNA exam, will help you answer those questions. The GSNA Questions & Answers covers all the knowledge points of the real exam. 100% real GIAC GSNA exams and revised by experts!
Online GSNA free questions and answers of New Version:
NEW QUESTION 1
You work as the Network Technician for XYZ CORP. The company has a Linux-based network. You are working on the Red Hat operating system. You want to view only the last 4 lines of a file named /var/log/cron. Which of the following commands should you use to accomplish the task?
- A. tail -n 4 /var/log/cron
- B. tail /var/log/cron
- C. cat /var/log/cron
- D. head /var/log/cron
Answer: A
Explanation:
The tail -n 4 /var/log/cron command will show the last four lines of the file /var/log/cron.
NEW QUESTION 2
Which of the following statements about session tracking is true?
- A. When using cookies for session tracking, there is no restriction on the name of the session tracking cookie.
- B. When using cookies for session tracking, the name of the session tracking cookie must be jsessionid.
- C. A server cannot use cookie as the basis for session tracking.
- D. A server cannot use URL rewriting as the basis for session tracking.
Answer: B
Explanation:
If you are using cookies for session tracking, the name of the session tracking cookie must be jsessionid. A jsessionid can be placed only inside a cookie header. You can use HTTP cookies to store information about a session. The servlet container takes responsibility of generating the session ID, making a new cookie object, associating the session ID into the cookie, and setting the cookie as part of response.
NEW QUESTION 3
You work as a Network Administrator for Tech Perfect Inc. You have a laptop running Windows Vista Ultimate. You want to configure Windows Defender on your laptop so that it does not take any action automatically whenever it scans malicious software. Rather, it should recommend the action and wait for your approval for taking any action. Which of the following actions will you take to accomplish the task?
- A. Clear the Use real-time protection check box in Defender Options
- B. Clear the Automatically scan my computer check box in Defender Options
- C. Select the Create a restore point before applying action to detected items check box in Defender Options
- D. Clear the Apply default actions to items detected during a scan check box in Defender Options.
Answer: D
Explanation:
According to the question, you want to prevent Windows Defender from taking any action automatically during the scanning of your laptop. In order to accomplish this, you will have to clear the Apply default actions to items detected during a scan check box in Defender Options.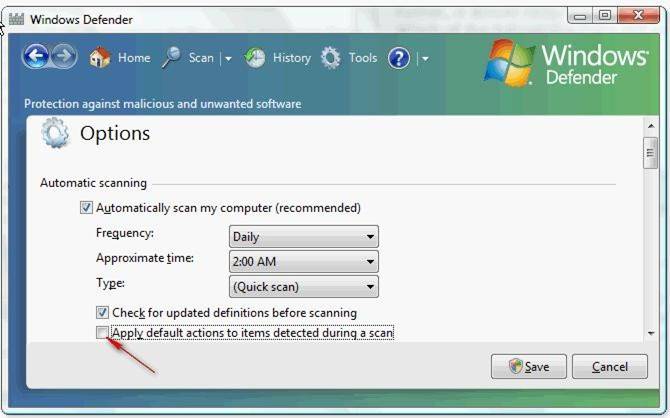
If you clear the Apply default actions to items detected during a scan check box, it will result in Windows Defender only recommending an action to take for detected malicious software.
NEW QUESTION 4
In a network, a data packet is received by a router for transmitting it to another network. In order to make decisions on where the data packet should be forwarded, the router checks with its routing table. Which of the following lists does a router check in a routing table?
- A. Available networks
- B. Available packets
- C. Available protocols
- D. Available paths
Answer: AD
Explanation:
A Routing table stores the actual routes to all destinations; the routing table is populated from the topology table with every destination network that has its successor and optionally feasible successor identified (if unequal-cost load-balancing is enabled using the variance command). The successors and feasible successors serve as the next hop routers for these destinations. Unlike most other distance vector protocols, EIGRP does not rely on periodic route dumps in order to maintain its topology table. Routing information is exchanged only upon the establishment of new neighbor adjacencies, after which only changes are sent. Answer C is incorrect. A routing table does not contain any list of protocols. Answer B is incorrect. A routing table does not contain any list of packets.
NEW QUESTION 5
Which of the following is a type of web site monitoring that is done using web browser emulation or scripted real web browsers?
- A. Route analytics
- B. Passive monitoring
- C. Network tomography
- D. Synthetic monitoring
Answer: D
Explanation:
Synthetic monitoring is an active Web site monitoring that is done using Web browser emulation or scripted real Web browsers. Behavioral scripts (or paths) are created to simulate an action or path that a customer or end-user would take on a site. Those paths are then continuously monitored at specified intervals for availability and response time measures. Synthetic monitoring is valuable because it enables a Webmaster to identify problems and determine if his Web site or Web application is slow or experiencing downtime before that problem affects actual end-users or customers. Answer B is incorrect. Passive monitoring is a technique used to analyze network traffic by capturing traffic from a network by generating a copy of that traffic. It is done with the help of a span port, mirror port, or network tap. Once the data (a stream of frames or packets) has been extracted, it can be used in many ways. Passive monitoring can be very helpful in troubleshooting performance problems once they have occurred. Passive monitoring relies on actual inbound Web traffic to take measurements, so problems can only be discovered after they have occurred. Answer A is incorrect. Route analytics is an emerging network monitoring technology specifically developed to analyze the routing protocols and structures in meshed IP networks. Their main mode of operation is to passively listen to the Layer 3 routing protocol exchanges between routers for the purposes of network discovery, mapping, real-time monitoring, and routing diagnostics. Answer C is incorrect. Network tomography is an important area of network measurement that deals with monitoring the health of various links in a network using end-to-end probes sent by agents located at vantage points in the network/Internet.
NEW QUESTION 6
You have to ensure that your Cisco Router is only accessible via telnet and ssh from the following hosts and subnets: 10.10.2.103 10.10.0.0/24 Which of the following sets of commands will you use to accomplish the task?
- A. access-list 10 permit host 10.10.2.103access-list 10 permit 10.10.0.0 0.0.0.255access-list 10 deny any line vty 0 4 access-class 10 out
- B. access-list 10 permit 10.10.2.103access-list 10 permit 10.10.0.0 0.0.0.255access-list 10 deny any line vty 0 4 access-group 10 in
- C. access-list 10 permit host 10.10.2.103access-list 10 permit 10.10.0.0 0.0.0.255access-list 10 deny any line vty 0 4access-class 10 in
- D. access-list 10 permit host 10.10.2.103access-list 11 permit host 10.10.0.0 255.255.255.0access-list 12 deny any line vty 0 4access-group 10, 11, 12 in
Answer: C
Explanation:
In order to accomplish the task, you will have to run the following sets of commands: access-list 10 permit host 10.10.2.103 access-list 10 permit 10.10.0.0 0.0.0.255 access-list 10 deny any line vty 0 4 access-class 10 in This configuration set meets all the requirements. The ACL is correctly configured and is applied to the VTY lines using the access-class command for inbound connections. Answer D is incorrect. This
configuration actually creates 3 separate ACL's (10, 11, and 12) and also incorrectly attempts to apply the ACL's to the VTY lines. Answer A is incorrect. This configuration is correct except for the access-class command being applied in the outbound direction. When using "access-class out", the router will not match connections coming into the router for Telnet and/or SSH. Instead, it will match connections being generated from the router. Answer B is incorrect. This configuration is correct except for the access-group command. Access-group is used to apply ACLs to an interface. Access-class is used to apply ACLs to VTY lines.
NEW QUESTION 7
Which of the following commands can be used to find out where commands are located?
- A. type
- B. which
- C. env
- D. ls
Answer: AB
Explanation:
The which and type commands can be used to find out where commands are located.
NEW QUESTION 8
What does CSS stand for?
- A. Cascading Style Sheet
- B. Coded System Sheet
- C. Cyclic Style Sheet
- D. Cascading Style System
Answer: A
Explanation:
A Cascading Style Sheet (CSS) is a separate text file that keeps track of design and formatting information, such as colors, fonts, font sizes, and margins, used in Web pages. CSS is used to provide Web site authors greater control on the appearance and presentation of their Web pages. It has codes that are interpreteA, Dpplied by the browser on to the Web pages and their elements. CSS files have .css extension.
There are three types of Cascading Style Sheets: External Style Sheet Embedded Style Sheet Inline Style Sheet
NEW QUESTION 9
Which of the following statements is true about residual risks?
- A. It is the probabilistic risk after implementing all security measures.
- B. It can be considered as an indicator of threats coupled with vulnerability.
- C. It is a weakness or lack of safeguard that can be exploited by a threat.
- D. It is the probabilistic risk before implementing all security measures.
Answer: A
Explanation:
The residual risk is the risk or danger of an action or an event, a method or a (technical) process that still conceives these dangers even if all theoretically possible safety measures would be applied. The formula to calculate residual risk is (inherent risk) x (control risk) where inherent risk is (threats vulnerability). Answer B is incorrect. In information security, security risks are considered as an indicator of threats coupled with vulnerability. In other words, security risk is a probabilistic function of a given threat agent exercising a particular vulnerability and the impact of that risk on the organization. Security risks can be mitigated by reviewing and taking responsible actions based on possible risks. Answer C is incorrect. Vulnerability is a weakness or lack of safeguard that can be exploited by a threat, thus causing harm to the information systems or networks. It can exist in hardware , operating systems, firmware, applications, and configuration files. Vulnerability has been variously defined in the current context as follows: 1.A security weakness in a Target of Evaluation due to failures in analysis, design, implementation, or operation and such. 2.Weakness in an information system or components (e.g. system security procedures, hardware design, or internal controls that could be exploited to produce an information-related misfortune.) 3.The existence of a weakness, design, or implementation error that can lead to an unexpected, undesirable event compromising the security of the system, network, application, or protocol involved.
NEW QUESTION 10
You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router. You run the following command for a router interface: show interface serial0 You get the following output: Serial0 is administratively down, line protocol is down What will be your conclusion after viewing this output?
- A. There is a physical problem either with the interface or the cable attached to it.
- B. The router has no power.
- C. There is a problem related to encapsulation.
- D. The interface is shut down.
Answer: D
Explanation:
According to the question, the output displays that the interface is administratively down. Administratively down means that the interface is shut down. In order to up the interface, you will have to open the interface with the no shutdown command. Answer A is incorrect. Had there been a physical problem with the interface, the output would not have displayed "administratively down". Instead, the output would be as follows: serial0 is down, line protocol is down Answer B is incorrect. You cannot run this command on a router that is powered off. Answer C is incorrect. Encapsulation has nothing to do with the output displayed in the question.
NEW QUESTION 11
Which of the following policies helps reduce the potential damage from the actions of one person?
- A. CSA
- B. Separation of duties
- C. Internal audit
- D. Risk assessment
Answer: B
Explanation:
Separation of duties (SoD) is the concept of having more than one person required to complete a task. It is alternatively called segregation of duties or, in the political realm, separation of powers. Segregation of duties helps reduce the potential damage from the actions of one person. IS or end-user department should be organized in a way to achieve adequate separation of duties. According to ISACA's Segregation of Duties Control matrix, some duties should not be combined into one position. This matrix is not an industry standard, just a general guideline suggesting which positions should be separated and which require compensating controls when combined. Answer A is incorrect. Cisco Security Agent (CSA) is an endpoint intrusion prevention system. It is rule-based and examines system activity and network traffic, determining which behaviors are normal and which may indicate an attack. CSA uses a two or three-tier client- server architecture. The Management Center 'MC' (or Management Console) contains the program logic; an MS SQL database backend is used to store alerts and configuration information; the MC and SQL database may be co-resident on the same system. The Agent is installed on the desktops and/or servers to be protected. The Agent communicates with the Management Center, sending logged events to the Management Center and receiving updates in rules when they occur. Answer C is incorrect. Internal auditing is a profession and activity involved in helping organizations achieve their stated objectives. It does this by using a systematic methodology for analyzing business processes, procedures and activities with the goal of highlighting organizational problems and recommending solutions. Answer D is incorrect. Risk assessment is a step in a risk management process.
NEW QUESTION 12
Which of the following processes are involved under the COBIT framework?
- A. Managing the IT workforce.
- B. Correcting all risk issues.
- C. Conducting IT risk assessments.
- D. Developing a strategic plan.
Answer: ACD
Explanation:
The Control Objectives for Information and related Technology (COBIT) is a set of best practices (framework) for information technology (IT) management, which provides managers, auditors, and IT users with a set of generally accepted measures, indicators, processes and best practices to assist them in maximizing the benefits derived through the use of information technology and developing appropriate IT governance and control in a company. It has the following 11 processes: Developing a strategic plan. Articulating the information architecture. Finding an optimal stage between the IT and the organization's strategy. Designing the IT function to match the organization's needs. Maximizing the return of the IT investment. Communicating IT policies to the user's community. Managing the IT workforce. Obeying external regulations, laws, and contracts. Conducting IT risk assessments. Maintaining a high-quality systems-development process. Incorporating sound project-management techniques. Answer B is incorrect. Correcting all risk issues does not come under auditing processes.
NEW QUESTION 13
Which of the following backup sites takes the longest recovery time?
- A. Mobile backup site
- B. Warm site
- C. Cold site
- D. Hot site
Answer: C
Explanation:
A cold backup site takes the longest recovery time. It is the most inexpensive type of backup site for an organization to operate. It does not include backed up copies of data and information from the original location of the organization, nor does it include hardware already set up. The lack of hardware contributes to the minimal startup costs of the cold site, but requires additional time following the disaster to have the operation running at a capacity close to that prior to the disaster. Answer D is incorrect. A hot site is a duplicate of the original site of the organization, with full computer systems as well as near- complete backups of user data. Real time synchronization between the two sites may be used to completely mirror the data environment of the original site using wide area network links and specialized software. Ideally, a hot site will be up and running within a matter of hours or even less. Answer A is incorrect. Although a mobile backup site provides rapid recovery, it does not provide full recovery in time. Hence, a hot site takes the shortest recovery time. Answer B is incorrect. A warm site is, quite logically, a compromise between hot and cold. These sites will have hardware and connectivity already established, though on a smaller scale than the original production site or even a hot site. Warm sites will have backups on hand, but they may not be complete and may be between several days and a week old. An example would be backup tapes sent to the warm site by courier.
NEW QUESTION 14
You have detected what appears to be an unauthorized wireless access point on your network. However this access point has the same MAC address as one of your real access points and is broadcasting with a stronger signal. What is this called?
- A. Buesnarfing
- B. The evil twin attack
- C. WAP cloning
- D. DOS
Answer: B
Explanation:
In the evil twin attack, a rogue wireless access point is set up that has the same MAC address as one of your legitimate access points. That rogue WAP will often then initiate a denial of service attack on your legitimate access point making it unable to respond to users, so they are redirected to the 'evil twin'. Answer A is incorrect. Blue snarfing is the process of taking over a PD Answer D is incorrect. A DOS may be used as part of establishing an evil twin, but this attack is not specifically for denial of service. Answer C is incorrect. While you must clone a WAP MAC address, the attack is not called WAP cloning.
NEW QUESTION 15
You work as a Network Administrator for Tech Perfect Inc. For security issues, the company requires you to harden its routers. You therefore write the following code: Router#config terminal Router(config) #no ip bootp server Router(config) #no ip name- server Router(config) #no ntp server Router(config) #no snmp server Router(config) #no ip http server Router(config) #^Z Router# What services will be disabled by using this configuration fragment?
- A. BootP service
- B. Finger
- C. CDP
- D. DNS function
Answer: AD
Explanation:
The above configuration fragment will disable the following services from the router: The BootP service The DNS function The Network Time Protocol The Simple Network Management Protocol Hyper Text Transfer Protocol
NEW QUESTION 16
Which of the following is an example of penetration testing?
- A. Configuring firewall to block unauthorized traffic
- B. Implementing HIDS on a computer
- C. Simulating an actual attack on a network
- D. Implementing NIDS on a network
Answer: C
Explanation:
Penetration testing is a method of evaluating the security of a computer system or network by simulating an attack from a malicious source, known as a Black Hat Hacker, or Cracker. The process involves an active analysis of the system for any potential vulnerabilities that may result from poor or improper system configuration, known and/or unknown hardware or software flaws, or operational weaknesses in process or technical countermeasures. This analysis is carried out from the position of a potential attacker, and can involve active exploitation of security vulnerabilities. Any security issues that are found will be presented to the system owner together with an assessment of their impact and often with a proposal for mitigation or a technical solution. The intent of a penetration testing is to determine feasibility of an attack and the amount of business impact of a successful exploit, if discovered. It is a component of a full security of penetration testing.
NEW QUESTION 17
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He begins to perform a pre-attack test before conducting an attack on the We-are-secure server. Which of the following will John perform in the pre-attack phase?
- A. Determining network range
- B. Identifying active machines
- C. Enumeration
- D. Finding open ports and applications
- E. Information gathering
Answer: ABDE
Explanation:
In the pre-attack phase, there are seven steps, which have been defined by the EC-Council, as follows: 1.Information gathering 2.Determining network range 3.Identifying active machines 4.Finding open ports and applications 5.OS fingerprinting 6.Fingerprinting services 7.Mapping the network Answer C is incorrect. In the enumeration phase, the attacker gathers information such as the network user and group names, routing tables, and Simple Network Management Protocol (SNMP) data. The techniques used in this phase are as follows: 1.Obtaining Active Directory information and identifying vulnerable user accounts 2.Discovering NetBIOS names 3.Employing Windows DNS queries 4.Establishing NULL sessions and queries
NEW QUESTION 18
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP- based network. You have configured a firewall on the network. A filter has been applied to block all the ports. You want to enable sending and receiving of emails on the network. Which of the following ports will you open? (Choose two)
- A. 25
- B. 20
- C. 80
- D. 110
Answer: AD
Explanation:
In order to enable email communication, you will have to open ports 25 and 110. Port 25 is used by SMTP to send emails. Port 110 is used by POP3 to receive emails.
NEW QUESTION 19
......
Recommend!! Get the Full GSNA dumps in VCE and PDF From Dumps-files.com, Welcome to Download: https://www.dumps-files.com/files/GSNA/ (New 368 Q&As Version)
- The Update Guide To GISF Exam Answers
- A Review Of Highest Quality GSNA Testing Bible
- All About High Quality GCIH Free Dumps
- The Up To The Minute Guide To GSEC Free Practice Questions
- How Many Questions Of GSEC Practice Question
- What Accurate GCIA Pdf Exam Is
- Guaranteed GIAC GCIA Pdf Exam Online
- Improved GIAC Security Essentials Certification GSEC Practice
- The Up To The Minute Guide To GCIH Test Question
- Improved GISF Answers For GIAC Information Security Fundamentals Certification


