GSEC Exam Questions - Online Test
GSEC Premium VCE File

150 Lectures, 20 Hours
It is impossible to pass GIAC GSEC exam without any help in the short term. Come to Examcollection soon and find the most advanced, correct and guaranteed GIAC GSEC practice questions. You will get a surprising result by our Update GIAC Security Essentials Certification practice guides.
Free GSEC Demo Online For GIAC Certifitcation:
NEW QUESTION 1
Which of the following is TRUE regarding the ability of attackers to eavesdrop on wireless communications?
- A. Eavesdropping attacks cannot be performed through concrete wall
- B. Eavesdropping attacks can take place from miles awa
- C. Eavesdropping attacks are easily detected on wireless network
- D. Eavesdropping attacks require expensive device
Answer: B
NEW QUESTION 2
In PKI, when someone wants to verify that the certificate is valid, what do they use to decrypt the signature?
- A. Receiver's digital signature
- B. X.509 certificate CA's private key
- C. Secret passphrase
- D. CA's public key
Answer: D
NEW QUESTION 3
Which of the following is a Layer 3 device that will typically drop directed broadcast traffic?
- A. Hubs
- B. Bridges
- C. Routers
- D. Switches
Answer: C
NEW QUESTION 4
Which of the following is NOT a recommended best practice for securing Terminal Services and Remote Desktop?
- A. Require TLS authentication and data encryption whenever possibl
- B. Make sure to allow all TCP 3389 traffic through the external firewal
- C. Group Policy should be used to lock down the virtual desktops of thin-client user
- D. Consider using IPSec or a VPN in addition to the RDP encryption if you are concerned about future RDP vulnerabilitie
Answer: B
NEW QUESTION 5
Which of the following groups represents the most likely source of an asset loss through the inappropriate use of computers?
- A. Visitors
- B. Customers
- C. Employees
- D. Hackers
Answer: C
NEW QUESTION 6
You are responsible for technical support at a company. One of the employees complains that his new laptop cannot connect to the company wireless network. You have verified that he is entering a valid password/passkey. What is the most likely problem?
- A. A firewall is blocking hi
- B. His laptop is incompatibl
- C. MAC filtering is blocking hi
- D. His operating system is incompatibl
Answer: C
NEW QUESTION 7
Which Host-based IDS (HIDS) method of log monitoring utilizes a list of keywords or phrases that define the events of interest for the analyst, then takes a list of keywords to watch for and generates alerts when it sees matches in log file activity?
- A. Passive analysis
- B. Retroactive analysis
- C. Exclusive analysis
- D. Inclusive analysis
Answer: D
NEW QUESTION 8
Which of the following is an advantage of a Host Intrusion Detection System (HIDS) versus a Network Intrusion Detection System (NIDS)?
- A. Ability to detect malicious traffic after it has been decrypted by the host
- B. Ability to decrypt network traffic
- C. Ability to listen to network traffic at the perimeter
- D. Ability to detect malicious traffic before it has been decrypted
Answer: A
NEW QUESTION 9
An employee attempting to use your wireless portal reports receiving the error shown below. Which scenario is occurring?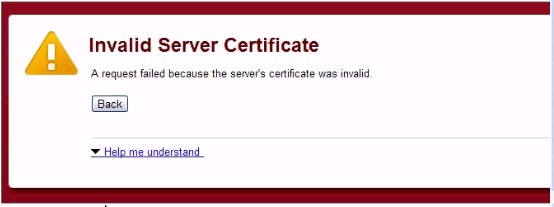
- A. A denial-of-service attack is preventing a response from the porta
- B. Another access point is deauthenticating legitimate client
- C. The encrypted data is being intercepted and decrypte
- D. Another access point is attempting to intercept the dat
Answer: D
NEW QUESTION 10
You ask your system administrator to verify user compliance with the corporate policies on password strength, namely that all passwords will have at least one numeral, at least one letter, at least one special character and be 15 characters long. He comes to you with a set of compliance tests for use with an offline password cracker. They are designed to examine the following parameters of the password:
* they contain only numerals
* they contain only letters
* they contain only special characters
* they contain only letters and numerals
" they contain only letters and special characters
* they contain only numerals and special characters
Of the following, what is the benefit to using this set of tests?
- A. They are focused on cracking passwords that use characters prohibited by the password policy
- B. They find non-compliant passwords without cracking compliant password
- C. They are focused on cracking passwords that meet minimum complexity requirements
- D. They crack compliant and non-compliant passwords to determine whether the current policy is strong enough
Answer: B
NEW QUESTION 11
Which of the following is an advantage of an Intrusion Detection System?
- A. It is a mature technolog
- B. It is the best network securit
- C. It never needs patchin
- D. It is a firewall replacemen
Answer: A
NEW QUESTION 12
Your organization has broken its network into several sections/segments, which are separated by firewalls, ACLs and VLANs. The purpose is to defend segments of the network from potential attacks that originate in a different segment or that attempt to spread across segments.
This style of defense-in-depth protection is best described as which of the following?
- A. Uniform protection
- B. Protected enclaves
- C. Vector-oriented
- D. Information-centric
Answer: B
NEW QUESTION 13
Which of the following statements about the authentication concept of information security management is true?
- A. It ensures the reliable and timely access to resource
- B. It ensures that modifications are not made to data by unauthorized personnel or processe
- C. It determines the actions and behaviors of a single individual within a system, and identifies that particular individua
- D. It establishes the users' identity and ensures that the users are who they say they ar
Answer: D
NEW QUESTION 14
When designing wireless networks, one strategy to consider is implementing security mechanisms at all layers of the OSI model. Which of the following protection mechanisms would protect layer 1?
- A. Hardening applications
- B. Limit RF coverage
- C. Employing firewalls
- D. Enabling strong encryption
Answer: B
NEW QUESTION 15
You work as a Network Administrator for Rick International. The company has a TCP/IP-based network. A user named Kevin wants to set an SSH terminal at home to connect to the company's network. You have to configure your company's router for it. By default, which of the following standard ports does the SSH protocol use for connection?
- A. 443
- B. 22
- C. 21
- D. 80
Answer: B
NEW QUESTION 16
Which of the following statements about DMZ are true?
Each correct answer represents a complete solution. Choose two.
- A. It is the boundary between the Internet and a private networ
- B. It is an anti-virus software that scans the incoming traffic on an internal networ
- C. It contains company resources that are available on the Internet, such as Web servers and FTP server
- D. It contains an access control list (ACL).
Answer: AC
NEW QUESTION 17
Which of the following statements about the integrity concept of information security management are true?
Each correct answer represents a complete solution. Choose three.
- A. It ensures that unauthorized modifications are not made to data by authorized personnel or processe
- B. It determines the actions and behaviors of a single individual within a system
- C. It ensures that internal information is consistent among all subentities and also consistent with the real-world, external situatio
- D. It ensures that modifications are not made to data by unauthorized personnel or processe
Answer: ACD
NEW QUESTION 18
Which of the following items are examples of preventive physical controls? Each correct answer represents a complete solution. Choose three.
- A. Biometric access controls
- B. Closed-circuit television monitors
- C. Fire extinguishers
- D. Locks and keys
Answer: ACD
NEW QUESTION 19
There are three key factors in selecting a biometric mechanism. What are they?
- A. Reliability, encryption strength, and cost
- B. Encryption strength, authorization method, and cost
- C. Reliability, user acceptance, and cost
- D. User acceptance, encryption strength, and cost
Answer: C
NEW QUESTION 20
You have set up a local area network for your company. Your firewall separates your network into several sections: a DMZ with semi-public servers (web, dns, email) and an intranet with private servers. A penetration tester gains access to both sections and installs sniffers in each. He is able to capture network traffic for all the devices in the private section but only for one device (the device with the sniffer) in the DMZ. What can be inferred about the design of the system?
- A. You installed a router in the private section and a switch in the DMZ
- B. You installed a hub in the private section and a switch in the DMZ
- C. You installed a switch in the private section and a hub in the DMZ
- D. You installed a switch in the private section and a router in the DMZ
Answer: B
NEW QUESTION 21
......
Recommend!! Get the Full GSEC dumps in VCE and PDF From Dumps-hub.com, Welcome to Download: https://www.dumps-hub.com/GSEC-dumps.html (New 279 Q&As Version)
- A Review Of Best Quality GSEC Simulations
- What Breathing GSNA Exam Answers Is
- How Many Questions Of GCIA Pdf
- The Secret Of GIAC GCIH Free Exam Questions
- The Up To The Minute Guide To GSEC Free Practice Questions
- Rebirth GIAC Information Security Fundamentals GISF Practice Exam
- Top Tips Of Updated GSNA Preparation
- Far Out GCIA Braindump For GIAC Certified Intrusion Analyst Certification
- Improved GIAC Security Essentials Certification GSEC Practice
- All About High Quality GCIH Free Dumps


