GSEC Exam Questions - Online Test
GSEC Premium VCE File

150 Lectures, 20 Hours
Your success in GIAC GSEC is our sole target and we develop all our GSEC braindumps in a way that facilitates the attainment of this target. Not only is our GSEC study material the best you can find, it is also the most detailed and the most updated. GSEC Practice Exams for GIAC GSEC are written to the highest standards of technical accuracy.
Online GIAC GSEC free dumps demo Below:
NEW QUESTION 1
While using Wire shark to investigate complaints of users being unable to login to a web application, you come across an HTTP POST submitted through your web application. The contents of the POST are listed below. Based on what you see below, which of the following would you recommend to prevent future damage to your database?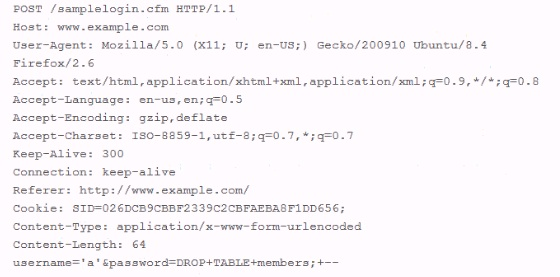
- A. Use ssh to prevent a denial of service attack
- B. Sanitize user inputs to prevent injection attacks
- C. Authenticate users to prevent hackers from using your database
- D. Use https to prevent hackers from inserting malware
Answer: D
NEW QUESTION 2
Which of the following is the reason of using Faraday cage?
- A. To prevent Denial-of-Service (DoS) attack
- B. To prevent shoulder surfing
- C. To prevent mail bombing
- D. To prevent data emanation
Answer: D
NEW QUESTION 3
How are differences in configuration settings handled between Domain and Local Group Policy Objects (GPOs)?
- A. Local and Domain GPOs control different configuration settings, so there will not be conflict
- B. Settings in the domain-wide GPO override conflicting settings in the local GPO on each compute
- C. Settings in the local GPO override conflicting settings when the domain-wide GPO is applie
- D. Precedence depends on which GPO was updated firs
Answer: B
NEW QUESTION 4
You work as a Network Administrator for Secure World Inc. The company has a Linux-based network. You want to run a command with the changed root directory. Which of the following commands will you use?
- A. ls <new root> <command>
- B. chroot <new root> <command>
- C. route <new root> <command>
- D. chdir <new root> <command>
Answer: B
NEW QUESTION 5
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He is currently working on his C based new traceroute program. Since, many processes are running together on the system, he wants to give the highest priority to the cc command process so that he can test his program, remove bugs, and submit it to the office in time. Which of the following commands will John use to give the highest priority to the cc command process?
- A. nice -n 19 cc -c *.c &
- B. nice cc -c *.c &
- C. nice -n -20 cc -c *.c &
- D. nice cc -c *.c
Answer: C
NEW QUESTION 6
When a packet leaving the network undergoes Network Address Translation (NAT), which of the following is changed?
- A. TCP Sequence Number
- B. Source address
- C. Destination port
- D. Destination address
Answer: B
NEW QUESTION 7
Which of the following utilities provides an efficient way to give specific users permission to use specific system commands at the root level of a Linux operating system?
- A. Snort
- B. Apache
- C. SSH
- D. SUDO
Answer: D
NEW QUESTION 8
You work as a Network Administrator for Net World Inc. The company has a Linux-based network. You are optimizing performance and security on your Web server. You want to know the ports that are listening to FTP. Which of the following commands will you use?
- A. netstat -a | grep FTP
- B. FTP netstat -r
- C. FTP netstat -a
- D. netstat -r | grep FTP
Answer: A
NEW QUESTION 9
You work as a Network Administrator for Net Soft Inc. You are designing a data backup plan for your company's network. The backup policy of the company requires high security and easy recovery of data. Which of the following options will you choose to accomplish this?
- A. Take a full backup daily with the previous night's tape taken offsit
- B. Take a full backup daily and use six-tape rotatio
- C. Take a full backup on Monday and an incremental backup on each of the following weekday
- D. Keep Monday's backup offsit
- E. Take a full backup on alternate days and keep rotating the tape
- F. Take a full backup on Monday and a differential backup on each of the following weekday
- G. Keep Monday's backup offsit
- H. Take a full backup daily with one tape taken offsite weekl
Answer: A
NEW QUESTION 10
Included below is the output from a resource kit utility run against local host.
Which command could have produced this output? 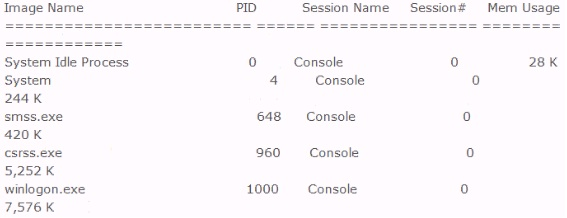
- A. Schtasks
- B. Task kill
- C. SC
- D. Task list
Answer: D
NEW QUESTION 11
Which of the following networking topologies uses a hub to connect computers?
- A. Bus
- B. Ring
- C. Star
- D. Cycle
Answer: C
NEW QUESTION 12
Which port category does the port 110 fall into?
- A. Well known port
- B. Dynamic port
- C. Private port
- D. Application port
Answer: A
NEW QUESTION 13
Which type of risk assessment results are typically categorized as low, medium, or high-risk events?
- A. Technical
- B. Qualitative
- C. Management
- D. Quantitative
Answer: B
NEW QUESTION 14
You work as a Network Administrator for McNeil Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest domain-based network. The company's management has decided to provide laptops to its sales team members. These laptops are equipped with smart card readers. The laptops will be configured as wireless network clients. You are required to accomplish the following tasks:
The wireless network communication should be secured.
The laptop users should be able to use smart cards for getting authenticated. In order to accomplish the tasks, you take the following steps:
Configure 802.1x and WEP for the wireless connections. Configure the PEAP-MS-CHAP v2 protocol for authentication. What will happen after you have taken these steps?
- A. The laptop users will be able to use smart cards for getting authenticate
- B. Both tasks will be accomplishe
- C. None of the tasks will be accomplishe
- D. The wireless network communication will be secure
Answer: D
NEW QUESTION 15
Which of the following hardware devices prevents broadcasts from crossing over subnets?
- A. Bridge
- B. Hub
- C. Router
- D. Modem
Answer: C
NEW QUESTION 16
Which of the below choices should an organization start with when implementing an effective risk management process?
- A. Implement an incident response plan
- B. Define security policy requirements
- C. Conduct periodic reviews
- D. Design controls and develop standards for each technology you plan to deploy
Answer: B
NEW QUESTION 17
What is SSL primarily used to protect you against?
- A. Session modification
- B. SQL injection
- C. Third-patty sniffing
- D. Cross site scripting
Answer: C
NEW QUESTION 18
Which of the following is an advantage of private circuits versus VPNs?
- A. Flexibility
- B. Performance guarantees
- C. Cost
- D. Time required to implement
Answer: B
NEW QUESTION 19
You work as a Network Administrator for NetTech Inc. To ensure the security of files, you encrypt data files using Encrypting File System (EFS).
You want to make a backup copy of the files and maintain security settings. You can backup the files either to a network share or a floppy disk. What will you do to accomplish this?
- A. Copy the files to a network share on an NTFS volum
- B. Copy the files to a network share on a FAT32 volum
- C. Place the files in an encrypted folde
- D. Then, copy the folder to a floppy dis
- E. Copy the files to a floppy disk that has been formatted using Windows 2000 Professiona
Answer: A
NEW QUESTION 20
Which of the following is a standard Unix command that would most likely be used to copy raw file system data for later forensic analysis?
- A. dd
- B. backup
- C. cp
- D. gzip
Answer: A
NEW QUESTION 21
......
P.S. Dumps-hub.com now are offering 100% pass ensure GSEC dumps! All GSEC exam questions have been updated with correct answers: https://www.dumps-hub.com/GSEC-dumps.html (279 New Questions)
- Up To The Immediate Present GIAC Systems And Network Auditor GSNA Sample Question
- Rebirth GIAC Information Security Fundamentals GISF Practice Exam
- Top Tips Of Leading GISF Actual Test
- The Secret Of GIAC GCIH Free Exam Questions
- Guaranteed GIAC GCIA Pdf Exam Online
- The Secret Of GIAC GCIH Test Question
- The Up To The Minute Guide To GCIH Test Question
- Top Tips Of Renew GCIA Prep
- A Review Of Highest Quality GSNA Testing Bible
- What Breathing GSNA Exam Answers Is


