412-79v9 Exam Questions - Online Test
412-79v9 Premium VCE File

150 Lectures, 20 Hours
Act now and download your EC-Council 412-79v9 test today! Do not waste time for the worthless EC-Council 412-79v9 tutorials. Download Update EC-Council EC-Council Certified Security Analyst (ECSA) v9 exam with real questions and answers and begin to learn EC-Council 412-79v9 with a classic professional.
Online 412-79v9 free questions and answers of New Version:
NEW QUESTION 1
An external intrusion test and analysis identify security weaknesses and strengths of the client's systems and networks as they appear from outside the client's security perimeter, usually from the Internet. The goal of an external intrusion test and analysis is to demonstrate the existence of known vulnerabilities that could be exploited by an external attacker.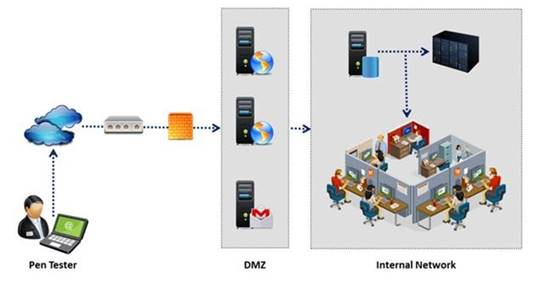
During external penetration testing, which of the following scanning techniques allow you to determine a port’s state without making a full connection to the host?
- A. XMAS Scan
- B. SYN scan
- C. FIN Scan
- D. NULL Scan
Answer: B
NEW QUESTION 2
Which one of the following components of standard Solaris Syslog is a UNIX command that is used to add single-line entries to the system log?
- A. “Logger”
- B. ”/etc/syslog.conf”
- C. “Syslogd”
- D. “Syslogd.conf”
Answer: A
NEW QUESTION 3
TCP/IP model is a framework for the Internet Protocol suite of computer network protocols that defines the communication in an IP-based network. It provides end-to-end connectivity specifying how data should be formatted, addressed, transmitted, routed and received at the destination. This functionality has been organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved.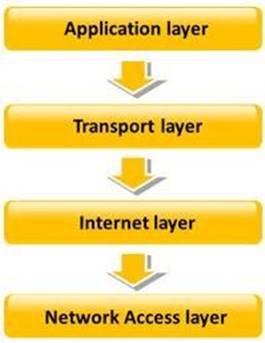
Which of the following TCP/IP layers selects the best path through the network for packets to travel?
- A. Transport layer
- B. Network Access layer
- C. Internet layer
- D. Application layer
Answer: C
NEW QUESTION 4
Identify the person who will lead the penetration-testing project and be the client point of contact.
- A. Database Penetration Tester
- B. Policy Penetration Tester
- C. Chief Penetration Tester
- D. Application Penetration Tester
Answer: C
Explanation:
Reference: http://www.scribd.com/doc/133635286/LPTv4-Module-15-Pre-Penetration-Testing-Checklist-NoRestriction (page 15)
NEW QUESTION 5
SQL injection attack consists of insertion or "injection" of either a partial or complete SQL query via the data input or transmitted from the client (browser) to the web application.
A successful SQL injection attack can: i)Read sensitive data from the database
iii) Modify database data (insert/update/delete)
iii)Execute administration operations on the database (such as shutdown the DBMS) iV)Recover the content of a given file existing on the DBMS file system or write files into the file system
v)Issue commands to the operating system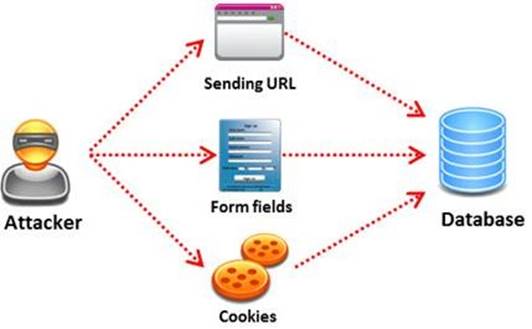
Pen tester needs to perform various tests to detect SQL injection vulnerability. He has to make a list of all input fields whose values could be used in crafting a SQL query, including the hidden fields of POST requests and then test them separately, trying to interfere with the query and to generate an error.
In which of the following tests is the source code of the application tested in a non-runtime environment to detect the SQL injection vulnerabilities?
- A. Automated Testing
- B. Function Testing
- C. Dynamic Testing
- D. Static Testing
Answer: D
Explanation:
Reference: http://ijritcc.org/IJRITCC%20Vol_2%20Issue_5/Removal%20of%20Data%20Vulnerabilities
%20Using%20SQL.pdf
NEW QUESTION 6
Besides the policy implications of chat rooms, Internet Relay Chat (IRC) is frequented by attackers and used as a command and control mechanism. IRC normally uses which one of the following TCP ports?
- A. 6566 TCP port
- B. 6771 TCP port
- C. 6667 TCP port
- D. 6257 TCP port
Answer: C
NEW QUESTION 7
You work as an IT security auditor hired by a law firm in Boston. You have been assigned the responsibility to audit the client for security risks. When assessing the risk to the clients network, what step should you take first?
- A. Analyzing, categorizing and prioritizing resources
- B. Evaluating the existing perimeter and internal security
- C. Checking for a written security policy
- D. Analyzing the use of existing management and control architecture
Answer: C
NEW QUESTION 8
Which of the following statements is true about Multi-Layer Intrusion Detection Systems (mIDSs)?
- A. Decreases consumed employee time and increases system uptime
- B. Increases detection and reaction time
- C. Increases response time
- D. Both a and c
Answer: A
Explanation:
Reference: http://www.symantec.com/connect/articles/multi-layer-intrusion-detection- systems (economic advantages, first para)
NEW QUESTION 9
Which of the following are the default ports used by NetBIOS service?
- A. 135, 136, 139, 445
- B. 134, 135, 136, 137
- C. 137, 138, 139, 140
- D. 133, 134, 139, 142
Answer: A
NEW QUESTION 10
Today, most organizations would agree that their most valuable IT assets reside within applications and databases. Most would probably also agree that these are areas that have the weakest levels of security, thus making them the prime target for malicious activity from system administrators, DBAs, contractors, consultants, partners, and customers.
Which of the following flaws refers to an application using poorly written encryption code to securely encrypt and store sensitive data in the database and allows an attacker to steal or modify weakly protected data such as credit card numbers, SSNs, and other authentication credentials?
- A. SSI injection attack
- B. Insecure cryptographic storage attack
- C. Hidden field manipulation attack
- D. Man-in-the-Middle attack
Answer: B
NEW QUESTION 11
An antenna is a device that is designed to transmit and receive the electromagnetic waves that are generally called radio waves. Which one of the following types of antenna is
developed from waveguide technology?
- A. Leaky Wave Antennas
- B. Aperture Antennas
- C. Reflector Antenna
- D. Directional Antenna
Answer: B
NEW QUESTION 12
Which of the following equipment could a pen tester use to perform shoulder surfing?
- A. Binoculars
- B. Painted ultraviolet material
- C. Microphone
- D. All the above
Answer: A
Explanation:
Reference: http://en.wikipedia.org/wiki/Shoulder_surfing_(computer_security)
NEW QUESTION 13
DNS information records provide important data about:
- A. Phone and Fax Numbers
- B. Location and Type of Servers
- C. Agents Providing Service to Company Staff
- D. New Customer
Answer: B
NEW QUESTION 14
Logs are the record of the system and network activities. Syslog protocol is used for delivering log information across an IP network. Syslog messages can be sent via which one of the following?
- A. UDP and TCP
- B. TCP and SMTP
- C. SMTP
- D. UDP and SMTP
Answer: A
NEW QUESTION 15
What threat categories should you use to prioritize vulnerabilities detected in the pen testing report?
- A. 1, 2, 3, 4, 5
- B. Low, medium, high, serious, critical
- C. Urgent, dispute, action, zero, low
- D. A, b, c, d, e
Answer: B
NEW QUESTION 16
During external penetration testing, which of the following techniques uses tools like Nmap to predict the sequence numbers generated by the targeted server and use this information to perform session hijacking techniques?
- A. TCP Sequence Number Prediction
- B. IPID State Number Prediction
- C. TCP State Number Prediction
- D. IPID Sequence Number Prediction
Answer: A
Explanation:
Reference: http://www.scribd.com/doc/133636402/LPTv4-Module-18-External-Penetration-Testing-NoRestriction (p.43)
NEW QUESTION 17
Which of the following is the range for assigned ports managed by the Internet Assigned Numbers Authority (IANA)?
- A. 3001-3100
- B. 5000-5099
- C. 6666-6674
- D. 0 – 1023
Answer: D
Explanation:
Reference: https://www.ietf.org/rfc/rfc1700.txt (well known port numbers, 4th para)
NEW QUESTION 18
Mason is footprinting an organization to gather competitive intelligence. He visits the company's website for contact information and telephone numbers but does not find any. He knows the entire staff directory was listed on their website 12 months. How can he find the directory?
- A. Visit Google’s search engine and view the cached copy
- B. Crawl and download the entire website using the Surfoffline tool and save them to his computer
- C. Visit the company's partners’ and customers' website for this information
- D. Use WayBackMachine in Archive.org web site to retrieve the Internet archive
Answer: D
NEW QUESTION 19
Which of the following appendices gives detailed lists of all the technical terms used in the report?
- A. Required Work Efforts
- B. References
- C. Research
- D. Glossary
Answer: D
Explanation:
Refere’ http://en.wikipedia.org/wiki/Glossary
NEW QUESTION 20
The SnortMain () function begins by associating a set of handlers for the signals, Snort receives. It does this using the signal () function. Which one of the following functions is used as a programspecific signal and the handler for this calls the DropStats() function to output the current Snort statistics?
- A. SIGUSR1
- B. SIGTERM
- C. SIGINT
- D. SIGHUP
Answer: A
NEW QUESTION 21
By default, the TFTP server listens on UDP port 69. Which of the following utility reports the port status of target TCP and UDP ports on a local or a remote computer and is used to troubleshoot TCP/IP connectivity issues?
- A. PortQry
- B. Netstat
- C. Telnet
- D. Tracert
Answer: A
Explanation:
Reference: http://support.microsoft.com/kb/832919
NEW QUESTION 22
Assessing a network from a hacker's point of view to discover the exploits and vulnerabilities that are accessible to the outside world is which sort of vulnerability assessment?
- A. Network Assessments
- B. Application Assessments
- C. Wireless Network Assessments
- D. External Assessment
Answer: D
Explanation:
Reference: http://controlcase.com/managed_compliance_pci_vulnerability_scan.html
NEW QUESTION 23
Which one of the following acts related to the information security in the US fix the responsibility of management for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
- A. California SB 1386
- B. Sarbanes-Oxley 2002
- C. Gramm-Leach-Bliley Act (GLBA)
- D. USA Patriot Act 2001
Answer: B
NEW QUESTION 24
Which one of the following scans starts, but does not complete the TCP handshake sequence for each port selected, and it works well for direct scanning and often works well through firewalls?
- A. SYN Scan
- B. Connect() scan
- C. XMAS Scan
- D. Null Scan
Answer: A
NEW QUESTION 25
Which of the following is developed to address security concerns on time and reduce the misuse or threat of attacks in an organization?
- A. Vulnerabilities checklists
- B. Configuration checklists
- C. Action Plan
- D. Testing Plan
Answer: A
NEW QUESTION 26
......
P.S. Easily pass 412-79v9 Exam with 203 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader 412-79v9 Dumps: https://www.certleader.com/412-79v9-dumps.html (203 New Questions)
- EC-Council 312-50v9 Study Guides 2021
- Tested EC-Council 312-75 Testing Engine Online
- All About Certified 312-50v11 Actual Test
- The Secret Of EC-Council 312-50v11 Training Tools
- A Review Of Highest Quality 312-49v9 Exam Topics
- A Review Of Best Quality 412-79v10 Free Draindumps
- What Vivid 312-50v11 Testing Material Is
- EC-Council 712-50 Free Practice Questions 2021
- The Renovate Guide To 312-50v10 exam question
- Validated 712-50 Exam Questions 2021


