312-50v11 Exam Questions - Online Test
312-50v11 Premium VCE File

150 Lectures, 20 Hours
Act now and download your EC-Council 312-50v11 test today! Do not waste time for the worthless EC-Council 312-50v11 tutorials. Download Renewal EC-Council Certified Ethical Hacker Exam (CEH v11) exam with real questions and answers and begin to learn EC-Council 312-50v11 with a classic professional.
Check 312-50v11 free dumps before getting the full version:
NEW QUESTION 1
Tremp is an IT Security Manager, and he is planning to deploy an IDS in his small company. He is looking for an IDS with the following characteristics: - Verifies success or failure of an attack - Monitors system activities Detects attacks that a network-based IDS fails to detect - Near real-time detection and response - Does not require additional hardware - Lower entry cost Which type of IDS is best suited for Tremp's requirements?
- A. Gateway-based IDS
- B. Network-based IDS
- C. Host-based IDS
- D. Open source-based
Answer: C
NEW QUESTION 2
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From the command prompt, she types the following command.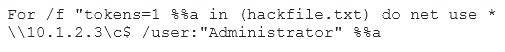
What is Eve trying to do?
- A. Eve is trying to connect as a user with Administrator privileges
- B. Eve is trying to enumerate all users with Administrative privileges
- C. Eve is trying to carry out a password crack for user Administrator
- D. Eve is trying to escalate privilege of the null user to that of Administrator
Answer: C
NEW QUESTION 3
Which of the following tools can be used to perform a zone transfer?
- A. NSLookup
- B. Finger
- C. Dig
- D. Sam Spade
- E. Host
- F. Netcat
- G. Neotrace
Answer: ACDE
NEW QUESTION 4
Nedved is an IT Security Manager of a bank in his country. One day. he found out that there is a security breach to his company's email server based on analysis of a suspicious connection from the email server to an unknown IP Address.
What is the first thing that Nedved needs to do before contacting the incident response team?
- A. Leave it as it Is and contact the incident response te3m right away
- B. Block the connection to the suspicious IP Address from the firewall
- C. Disconnect the email server from the network
- D. Migrate the connection to the backup email server
Answer: C
NEW QUESTION 5
When a normal TCP connection starts, a destination host receives a SYN (synchronize/start) packet from a source host and sends back a SYN/ACK (synchronize acknowledge). The destination host must then hear an ACK (acknowledge) of the SYN/ACK before the connection is established. This is referred to as the "TCP three-way handshake." While waiting for the ACK to the SYN ACK, a connection queue of finite size on the destination host keeps track of connections waiting to be completed. This queue typically empties quickly since the ACK is expected to arrive a few milliseconds after the SYN ACK.
How would an attacker exploit this design by launching TCP SYN attack?
- A. Attacker generates TCP SYN packets with random destination addresses towards a victim host
- B. Attacker floods TCP SYN packets with random source addresses towards a victim host
- C. Attacker generates TCP ACK packets with random source addresses towards a victim host
- D. Attacker generates TCP RST packets with random source addresses towards a victim host
Answer: B
NEW QUESTION 6
What is the known plaintext attack used against DES which gives the result that encrypting plaintext with one DES key followed by encrypting it with a second DES key is no more secure than using a single key?
- A. Man-in-the-middle attack
- B. Meet-in-the-middle attack
- C. Replay attack
- D. Traffic analysis attack
Answer: B
NEW QUESTION 7
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering that NMAP result below, which of the following is likely to be installed on the target machine by the OS? Starting NMAP 5.21 at 2011-03-15 11:06 NMAP scan report for 172.16.40.65 Host is up (1.00s latency). Not shown: 993 closed ports PORT STATE SERVICE 21/tcp open ftp 23/tcp open telnet 80/tcp open http 139/tcp open netbios-ssn 515/tcp open 631/tcp open ipp 9100/tcp open MAC Address: 00:00:48:0D:EE:8
- A. The host is likely a Linux machine.
- B. The host is likely a printer.
- C. The host is likely a router.
- D. The host is likely a Windows machine.
Answer: B
NEW QUESTION 8
Password cracking programs reverse the hashing process to recover passwords. (True/False.)
- A. True
- B. False
Answer: B
NEW QUESTION 9
The collection of potentially actionable, overt, and publicly available information is known as
- A. Open-source intelligence
- B. Real intelligence
- C. Social intelligence
- D. Human intelligence
Answer: A
NEW QUESTION 10
An attacker has installed a RAT on a host. The attacker wants to ensure that when a user attempts to go to "www.MyPersonalBank.com", the user is directed to a phishing site.
Which file does the attacker need to modify?
- A. Boot.ini
- B. Sudoers
- C. Networks
- D. Hosts
Answer: D
NEW QUESTION 11
Which utility will tell you in real time which ports are listening or in another state?
- A. Netstat
- B. TCPView
- C. Nmap
- D. Loki
Answer: B
NEW QUESTION 12
What two conditions must a digital signature meet?
- A. Has to be the same number of characters as a physical signature and must be unique.
- B. Has to be unforgeable, and has to be authentic.
- C. Must be unique and have special characters.
- D. Has to be legible and neat.
Answer: B
NEW QUESTION 13
Which mode of IPSec should you use to assure security and confidentiality of data within the same LAN?
- A. ESP transport mode
- B. ESP confidential
- C. AH permiscuous
- D. AH Tunnel mode
Answer: A
NEW QUESTION 14
If a token and 4-digit personal identification number (PIN) are used to access a computer system and the token performs off-line checking for the correct PIN, what type of attack is possible?
- A. Birthday
- B. Brute force
- C. Man-in-the-middle
- D. Smurf
Answer: B
NEW QUESTION 15
Based on the following extract from the log of a compromised machine, what is the hacker really trying to steal?
- A. har.txt
- B. SAM file
- C. wwwroot
- D. Repair file
Answer: B
NEW QUESTION 16
Joseph was the Web site administrator for the Mason Insurance in New York, who's main Web site was located at www.masonins.com. Joseph uses his laptop computer regularly to administer the Web site. One night, Joseph received an urgent phone call from his friend, Smith. According to Smith, the main Mason Insurance web site had been vandalized! All of its normal content was removed and replaced with an attacker's message ''Hacker Message: You are dead! Freaks!” From his office, which was directly connected to Mason Insurance's internal network, Joseph surfed to the Web site using his laptop. In his browser, the Web site looked completely intact.
No changes were apparent. Joseph called a friend of his at his home to help troubleshoot the problem. The Web site appeared defaced when his friend visited using his DSL connection. So, while Smith and his friend could see the defaced page, Joseph saw the intact Mason Insurance web site. To help make sense of this problem, Joseph decided to access the Web site using hisdial-up ISP. He disconnected his laptop from the corporate internal network and used his modem to dial up the same ISP used by Smith. After his modem connected, he quickly typed www.masonins.com in his browser to reveal the following web page: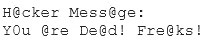
After seeing the defaced Web site, he disconnected his dial-up line, reconnected to the internal network, and used Secure Shell (SSH) to log in directly to the Web server. He ran Tripwire against the entire Web site, and determined that every system file and all the Web content on the server were intact. How did the attacker accomplish this hack?
- A. ARP spoofing
- B. SQL injection
- C. DNS poisoning
- D. Routing table injection
Answer: C
NEW QUESTION 17
Identify the UDP port that Network Time Protocol (NTP) uses as its primary means of communication?
- A. 113
- B. 69
- C. 123
- D. 161
Answer: C
NEW QUESTION 18
Why containers are less secure that virtual machines?
- A. Host OS on containers has a larger surface attack.
- B. Containers may full fill disk space of the host.
- C. A compromise container may cause a CPU starvation of the host.
- D. Containers are attached to the same virtual network.
Answer: A
NEW QUESTION 19
A company’s security policy states that all Web browsers must automatically delete their HTTP browser cookies upon terminating. What sort of security breach is this policy attempting to mitigate?
- A. Attempts by attackers to access the user and password information stored in the company’s SQL database.
- B. Attempts by attackers to access Web sites that trust the Web browser user by stealing the user’s authentication credentials.
- C. Attempts by attackers to access password stored on the user’s computer without the user’s knowledge.
- D. Attempts by attackers to determine the user’s Web browser usage patterns, including when sites were visited and for how long.
Answer: B
NEW QUESTION 20
The Heartbleed bug was discovered in 2014 and is widely referred to under MITRE’s Common Vulnerabilities and Exposures (CVE) as CVE-2014-0160. This bug affects the OpenSSL implementation of the Transport Layer Security (TLS) protocols defined in RFC6520.
What type of key does this bug leave exposed to the Internet making exploitation of any compromised system very easy?
- A. Public
- B. Private
- C. Shared
- D. Root
Answer: B
NEW QUESTION 21
......
Recommend!! Get the Full 312-50v11 dumps in VCE and PDF From Certshared, Welcome to Download: https://www.certshared.com/exam/312-50v11/ (New 254 Q&As Version)
- The Secret of EC-Council 312-50v10 dumps
- how many questions of 312-50v10 pdf?
- Validated 312-50v9 Braindumps 2021
- Breathing EC-Council 312-50v10 pdf
- The Secret Of EC-Council 312-50v11 Training Tools
- EC-Council 712-50 Free Practice Questions 2021
- Validated 712-50 Exam Questions 2021
- A Review Of 100% Guarantee 312-50v10 exam dumps
- The Renovate Guide To 312-50v10 exam question
- EC-Council 712-50 Braindumps 2021


