350-701 Exam Questions - Online Test
350-701 Premium VCE File

150 Lectures, 20 Hours
Master the 350-701 Implementing and Operating Cisco Security Core Technologies content and be ready for exam day success quickly with this Actualtests 350-701 practice exam. We guarantee it!We make it a reality and give you real 350-701 questions in our Cisco 350-701 braindumps.Latest 100% VALID Cisco 350-701 Exam Questions Dumps at below page. You can use our Cisco 350-701 braindumps and pass your exam.
Check 350-701 free dumps before getting the full version:
NEW QUESTION 1
Which exfiltration method does an attacker use to hide and encode data inside DNS requests and queries?
- A. DNS tunneling
- B. DNSCrypt
- C. DNS security
- D. DNSSEC
Answer: A
Explanation:
Reference: https://learn-umbrella.cisco.com/cloud-security/dns-tunneling
NEW QUESTION 2
Refer to the exhibit.
What is a result of the configuration?
- A. Traffic from the DMZ network is redirected.
- B. Traffic from the inside network is redirected.
- C. All TCP traffic is redirected.
- D. Traffic from the inside and DMZ networks is redirected.
Answer: D
NEW QUESTION 3
Why would a user choose an on-premises ESA versus the CES solution?
- A. Sensitive data must remain onsite.
- B. Demand is unpredictable.
- C. The server team wants to outsource this service.
- D. ESA is deployed inline.
Answer: A
NEW QUESTION 4
An engineer configured a new network identity in Cisco Umbrella but must verify that traffic is being routed through the Cisco Umbrella network. Which action tests the routing?
- A. Ensure that the client computers are pointing to the on-premises DNS servers.
- B. Enable the Intelligent Proxy to validate that traffic is being routed correctly.
- C. Add the public IP address that the client computers are behind to a Core Identity.
- D. Browse to http://welcome.umbrella.com/ to validate that the new identity is working.
Answer: B
NEW QUESTION 5
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two.)
- A. Patch for cross-site scripting.
- B. Perform backups to the private cloud.
- C. Protect against input validation and character escapes in the endpoint.
- D. Install a spam and virus email filter.
- E. Protect systems with an up-to-date antimalware program.
Answer: DE
NEW QUESTION 6
What are two list types within AMP for Endpoints Outbreak Control? (Choose two.)
- A. blocked ports
- B. simple custom detections
- C. command and control
- D. allowed applications
- E. URL
Answer: BD
Explanation:
Reference: https://docs.amp.cisco.com/en/A4E/AMP%20for%20Endpoints%20User%20Guide.pdf chapter 2
NEW QUESTION 7
Which two capabilities does TAXII support? (Choose two.)
- A. exchange
- B. pull messaging
- C. binding
- D. correlation
- E. mitigating
Answer: BC
NEW QUESTION 8
Which benefit does endpoint security provide the overall security posture of an organization?
- A. It streamlines the incident response process to automatically perform digital forensics on the endpoint.
- B. It allows the organization to mitigate web-based attacks as long as the user is active in the domain.
- C. It allows the organization to detect and respond to threats at the edge of the network.
- D. It allows the organization to detect and mitigate threats that the perimeter security devices do not detect.
Answer: D
NEW QUESTION 9
DRAG DROP
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2 instance in Amazon Web Services.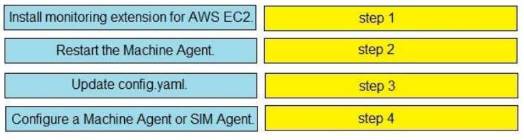
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 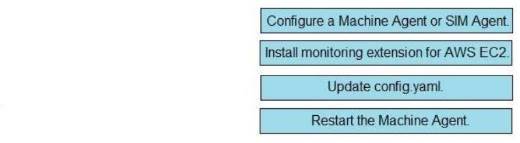
NEW QUESTION 10
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
- A. transparent
- B. redirection
- C. forward
- D. proxy gateway
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/117940-qa-wsa-00.html
NEW QUESTION 11
DRAG DROP
Drag and drop the capabilities from the left onto the correct technologies on the right.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 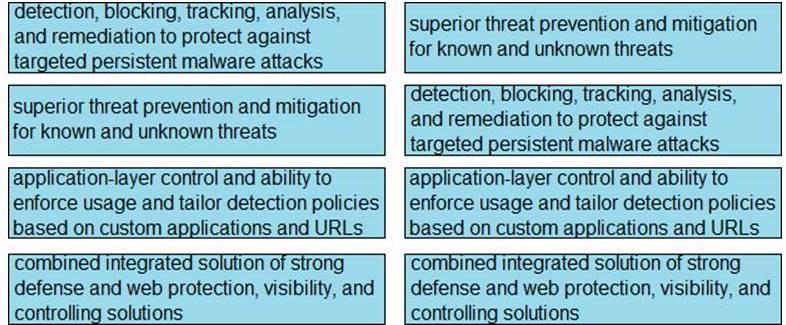
NEW QUESTION 12
Which Talos reputation center allows you to track the reputation of IP addresses for email and web traffic?
- A. IP Blacklist Center
- B. File Reputation Center
- C. AMP Reputation Center
- D. IP and Domain Reputation Center
Answer: D
NEW QUESTION 13
What is a characteristic of traffic storm control behavior?
- A. Traffic storm control drops all broadcast and multicast traffic if the combined traffic exceeds the level within the interval.
- B. Traffic storm control cannot determine if the packet is unicast or broadcast.
- C. Traffic storm control monitors incoming traffic levels over a 10-second traffic storm control interval.
- D. Traffic storm control uses the Individual/Group bit in the packet source address to determine if the packet is unicast or broadcast.
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/routers/7600/ios/12-1E/configuration/guide/storm.html
NEW QUESTION 14
Which two conditions are prerequisites for stateful failover for IPsec? (Choose two.)
- A. Only the IKE configuration that is set up on the active device must be duplicated on the standby device; the IPsec configuration is copied automatically.
- B. The active and standby devices can run different versions of the Cisco IOS software but must be the same type of device.
- C. The IPsec configuration that is set up on the active device must be duplicated on the standby device.
- D. Only the IPsec configuration that is set up on the active device must be duplicated on the standby device; the IKE configuration is copied automatically.
- E. The active and standby devices must run the same version of the Cisco IOS software and must be the same type of device.
Answer: BC
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_vpnav/configuration/15-mt/sec-vpn-availability-15-mt-book/sec-state-fail-ipsec.html
NEW QUESTION 15
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic. Where must the ASA be added on the Cisco UC Manager platform?
- A. Certificate Trust List
- B. Endpoint Trust List
- C. Enterprise Proxy Service
- D. Secured Collaboration Proxy
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/special/unified-communications/guide/unified-comm/unified-comm-tlsproxy.html
NEW QUESTION 16
When wired 802.1X authentication is implemented, which two components are required? (Choose two.)
- A. authentication server: Cisco Identity Service Engine
- B. supplicant: Cisco AnyConnect ISE Posture module
- C. authenticator: Cisco Catalyst switch
- D. authenticator: Cisco Identity Services Engine
- E. authentication server: Cisco Prime Infrastructure
Answer: AC
Explanation:
Reference: https://www.lookingpoint.com/blog/ise-series-802.1x
NEW QUESTION 17
DRAG DROP
Drag and drop the Firepower Next Generation Intrustion Prevention System detectors from the left onto the correct definitions on the right.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/detecting_specific_threats.html
NEW QUESTION 18
DRAG DROP
Drag and drop the descriptions from the left onto the correct protocol versions on the right.
[MISSING]
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
[MISSING]
NEW QUESTION 19
Which two request of REST API are valid on the Cisco ASA Platform? (Choose two.)
- A. put
- B. options
- C. get
- D. push
- E. connect
Answer: AC
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/api/qsg-asa-api.html
NEW QUESTION 20
Which technology is used to improve web traffic performance by proxy caching?
- A. WSA
- B. Firepower
- C. FireSIGHT
- D. ASA
Answer: A
NEW QUESTION 21
Which VPN technology can support a multivendor environment and secure traffic between sites?
- A. SSL VPN
- B. GET VPN
- C. FlexVPN
- D. DMVPN
Answer: C
Explanation:
Reference: https://www.cisco.com/c/en/us/products/collateral/routers/asr-1000-series-aggregation-services-routers/data_sheet_c78-704277.html
NEW QUESTION 22
An MDM provides which two advantages to an organization with regards to device management? (Choose two.)
- A. asset inventory management
- B. allowed application management
- C. Active Directory group policy management
- D. network device management
- E. critical device management
Answer: AB
NEW QUESTION 23
......
Recommend!! Get the Full 350-701 dumps in VCE and PDF From Certshared, Welcome to Download: https://www.certshared.com/exam/350-701/ (New 102 Q&As Version)
- A Review Of Free 300-075 dumps
- Printable Cisco 700-905 Brain Dumps Online
- A Review Of Highest Quality 300-075 pdf
- All About Highest Quality 400-051 exam dumps
- Downloadable 640-692 Practice Exam 2021
- Real CCNA Routing and Switching 200-105 exam dumps
- All About High value 300-070 examcollection
- The Secret of Cisco 300-208 examcollection
- A Review Of Actual 400-051 dumps
- Up To Date Cisco Networking: On-Premise And Cloud Solutions 500-560 Practice Question


