312-50v11 Exam Questions - Online Test
312-50v11 Premium VCE File

150 Lectures, 20 Hours
Want to know Exambible 312-50v11 Exam practice test features? Want to lear more about EC-Council Certified Ethical Hacker Exam (CEH v11) certification experience? Study Pinpoint EC-Council 312-50v11 answers to Abreast of the times 312-50v11 questions at Exambible. Gat a success with an absolute guarantee to pass EC-Council 312-50v11 (Certified Ethical Hacker Exam (CEH v11)) test on your first attempt.
Check 312-50v11 free dumps before getting the full version:
NEW QUESTION 1
What is the algorithm used by LM for Windows2000 SAM?
- A. MD4
- B. DES
- C. SHA
- D. SSL
Answer: B
NEW QUESTION 2
Which of the following LM hashes represent a password of less than 8 characters? (Choose two.)
- A. BA810DBA98995F1817306D272A9441BB
- B. 44EFCE164AB921CQAAD3B435B51404EE
- C. 0182BD0BD4444BF836077A718CCDF409
- D. CEC52EB9C8E3455DC2265B23734E0DAC
- E. B757BF5C0D87772FAAD3B435B51404EE
- F. E52CAC67419A9A224A3B108F3FA6CB6D
Answer: BE
NEW QUESTION 3
Which definition among those given below best describes a covert channel?
- A. A server program using a port that is not well known.
- B. Making use of a protocol in a way it is not intended to be used.
- C. It is the multiplexing taking place on a communication link.
- D. It is one of the weak channels used by WEP which makes it insecure
Answer: B
NEW QUESTION 4
Bob, a network administrator at BigUniversity, realized that some students are connecting their notebooks in the wired network to have Internet access. In the university campus, there are many Ethernet ports available for professors and authorized visitors but not for students.
He identified this when the IDS alerted for malware activities in the network. What should Bob do to avoid this problem?
- A. Disable unused ports in the switches
- B. Separate students in a different VLAN
- C. Use the 802.1x protocol
- D. Ask students to use the wireless network
Answer: C
NEW QUESTION 5
You need to deploy a new web-based software package for your organization. The package requires three separate servers and needs to be available on the Internet. What is the recommended architecture in terms of server placement?
- A. All three servers need to be placed internally
- B. A web server facing the Internet, an application server on the internal network, a database server on the internal network
- C. A web server and the database server facing the Internet, an application server on the internal network
- D. All three servers need to face the Internet so that they can communicate between themselves
Answer: B
NEW QUESTION 6
In the field of cryptanalysis, what is meant by a “rubber-hose" attack?
- A. Attempting to decrypt cipher text by making logical assumptions about the contents of the original plain text.
- B. Extraction of cryptographic secrets through coercion or torture.
- C. Forcing the targeted key stream through a hardware-accelerated device such as an ASIC.
- D. A backdoor placed into a cryptographic algorithm by its creator.
Answer: B
NEW QUESTION 7
What is correct about digital signatures?
- A. A digital signature cannot be moved from one signed document to another because it is the hash of the original document encrypted with the private key of the signing party.
- B. Digital signatures may be used in different documents of the same type.
- C. A digital signature cannot be moved from one signed document to another because it is a plain hash of the document content.
- D. Digital signatures are issued once for each user and can be used everywhere until they expire.
Answer: A
NEW QUESTION 8
Peter extracts the SIDs list from Windows 2000 Server machine using the hacking tool "SIDExtractor". Here is the output of the SIDs: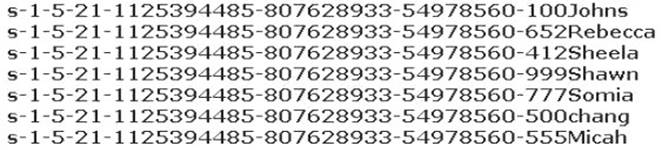
From the above list identify the user account with System Administrator privileges.
- A. John
- B. Rebecca
- C. Sheela
- D. Shawn
- E. Somia
- F. Chang
- G. Micah
Answer: F
NEW QUESTION 9
Which of the following tools can be used for passive OS fingerprinting?
- A. nmap
- B. tcpdump
- C. tracert
- D. ping
Answer: B
NEW QUESTION 10
You are the Network Admin, and you get a complaint that some of the websites are no longer accessible. You try to ping the servers and find them to be reachable. Then you type the IP address and then you try on the browser, and find it to be accessible. But they are not accessible when you try using the URL.
What may be the problem?
- A. Traffic is Blocked on UDP Port 53
- B. Traffic is Blocked on TCP Port 80
- C. Traffic is Blocked on TCP Port 54
- D. Traffic is Blocked on UDP Port 80
Answer: A
NEW QUESTION 11
Email is transmitted across the Internet using the Simple Mail Transport Protocol. SMTP does not encrypt email, leaving the information in the message vulnerable to being read by an unauthorized person. SMTP can upgrade a connection between two mail servers to use TLS. Email transmitted by SMTP over TLS is encrypted. What is the name of the command used by SMTP to transmit email over TLS?
- A. OPPORTUNISTICTLS
- B. UPGRADETLS
- C. FORCETLS
- D. STARTTLS
Answer: D
NEW QUESTION 12
In the field of cryptanalysis, what is meant by a “rubber-hose” attack?
- A. Forcing the targeted keystream through a hardware-accelerated device such as an ASIC.
- B. A backdoor placed into a cryptographic algorithm by its creator.
- C. Extraction of cryptographic secrets through coercion or torture.
- D. Attempting to decrypt ciphertext by making logical assumptions about the contents of the original plaintext.
Answer: C
NEW QUESTION 13
Peter is surfing the internet looking for information about DX Company. Which hacking process is Peter doing?
- A. Scanning
- B. Footprinting
- C. Enumeration
- D. System Hacking
Answer: B
NEW QUESTION 14
Susan has attached to her company's network. She has managed to synchronize her boss's sessions with that of the file server. She then intercepted his traffic destined for the server, changed it the way she wanted to and then placed it on the server in his home directory.
What kind of attack is Susan carrying on?
- A. A sniffing attack
- B. A spoofing attack
- C. A man in the middle attack
- D. A denial of service attack
Answer: C
NEW QUESTION 15
User A is writing a sensitive email message to user B outside the local network. User A has chosen to use PKI to secure his message and ensure only user B can read the sensitive email. At what layer of the OSI layer does the encryption and decryption of the message take place?
- A. Application
- B. Transport
- C. Session
- D. Presentation
Answer: D
NEW QUESTION 16
When analyzing the IDS logs, the system administrator noticed an alert was logged when the external router was accessed from the administrator’s Computer to update the router configuration. What type of an alert is this?
- A. False negative
- B. True negative
- C. True positive
- D. False positive
Answer: D
NEW QUESTION 17
By using a smart card and pin, you are using a two-factor authentication that satisfies
- A. Something you are and something you remember
- B. Something you have and something you know
- C. Something you know and something you are
- D. Something you have and something you are
Answer: B
NEW QUESTION 18
As a Certified Ethical Hacker, you were contracted by a private firm to conduct an external security assessment through penetration testing.
What document describes the specifics of the testing, the associated violations, and essentially protects both the organization’s interest and your liabilities as a tester?
- A. Service Level Agreement
- B. Project Scope
- C. Rules of Engagement
- D. Non-Disclosure Agreement
Answer: C
NEW QUESTION 19
Matthew, a black hat, has managed to open a meterpreter session to one of the kiosk machines in Evil Corp’s lobby. He checks his current SID, which is S-1-5-21-1223352397-1872883824-861252104-501. What needs to happen before Matthew has full administrator access?
- A. He must perform privilege escalation.
- B. He needs to disable antivirus protection.
- C. He needs to gain physical access.
- D. He already has admin privileges, as shown by the “501” at the end of the SID.
Answer: A
NEW QUESTION 20
An Intrusion Detection System (IDS) has alerted the network administrator to a possibly malicious sequence of packets sent to a Web server in the network’s external DMZ. The packet traffic was captured by the IDS and saved to a PCAP file. What type of network tool can be used to determine if these packets are genuinely malicious or simply a false positive?
- A. Protocol analyzer
- B. Network sniffer
- C. Intrusion Prevention System (IPS)
- D. Vulnerability scanner
Answer: A
NEW QUESTION 21
......
Recommend!! Get the Full 312-50v11 dumps in VCE and PDF From Dumps-hub.com, Welcome to Download: https://www.dumps-hub.com/312-50v11-dumps.html (New 254 Q&As Version)
- EC-Council 712-50 Free Practice Questions 2021
- Download 712-50 Braindumps 2021
- All About Certified 312-50v11 Actual Test
- The Improved Guide To ECSAv10 Dumps Questions
- The Secret of EC-Council 312-50v10 dumps
- Most Up-to-date 312-38 Sample Question For EC-Council Network Security Administrator (ENSA) Certification
- Update 312-50v10 Exam Study Guides With New Update Exam Questions
- Top Tips Of Abreast Of The Times 312-50v12 Practice Exam
- A Review Of Highest Quality 312-49v9 Exam Topics
- EC-Council 312-50v9 Study Guides 2021


