ECSAv10 Exam Questions - Online Test
ECSAv10 Premium VCE File

150 Lectures, 20 Hours
We provide real ECSAv10 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass EC-Council ECSAv10 Exam quickly & easily. The ECSAv10 PDF type is available for reading and printing. You can print more and practice many times. With the help of our EC-Council ECSAv10 dumps pdf and vce product and material, you can easily pass the ECSAv10 exam.
Online ECSAv10 free questions and answers of New Version:
NEW QUESTION 1
Which one of the following is a command line tool used for capturing data from the live network and copying those packets to a file?
- A. Wireshark: Capinfos
- B. Wireshark: Tcpdump
- C. Wireshark: Text2pcap
- D. Wireshark: Dumpcap
Answer: D
NEW QUESTION 2
What operating system would respond to the following command?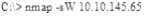
- A. Mac OS X
- B. Windows XP
- C. Windows 95
- D. FreeBSD
Answer: D
NEW QUESTION 3
The Internet is a giant database where people store some of their most private information on the cloud, trusting that the service provider can keep it all safe. Trojans, Viruses, DoS attacks, website defacement, lost computers, accidental publishing, and more have all been sources of major leaks over the last 15 years.
What is the biggest source of data leaks in organizations today?
- A. Weak passwords and lack of identity management
- B. Insufficient IT security budget
- C. Rogue employees and insider attacks
- D. Vulnerabilities, risks, and threats facing Web sites
Answer: C
NEW QUESTION 4
You have compromised a lower-level administrator account on an Active Directory network of a small company in Dallas, Texas. You discover Domain Controllers through enumeration. You connect to one of the Domain Controllers on port 389 using Idp.exe.
What are you trying to accomplish here?
- A. Poison the DNS records with false records
- B. Enumerate MX and A records from DNS
- C. Establish a remote connection to the Domain Controller
- D. Enumerate domain user accounts and built-in groups
Answer: D
NEW QUESTION 5
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides top-level guidance for conducting the penetration testing. Various factors are considered while preparing the scope of ROE which clearly explain the limits associated with the security test.
Which of the following factors is NOT considered while preparing the scope of the Rules of Engagment (ROE)?
- A. A list of employees in the client organization
- B. A list of acceptable testing techniques
- C. Specific IP addresses/ranges to be tested
- D. Points of contact for the penetration testing team
Answer: A
NEW QUESTION 6
Which of the following will not handle routing protocols properly?
- A. “Internet-router-firewall-net architecture”
- B. “Internet-firewall-router-net architecture”
- C. “Internet-firewall -net architecture”
- D. “Internet-firewall/router(edge device)-net architecture”
Answer: B
NEW QUESTION 7
By default, the TFTP server listens on UDP port 69. Which of the following utility reports the port status of target TCP and UDP ports on a local or a remote computer and is used to troubleshoot TCP/IP connectivity issues?
- A. PortQry
- B. Netstat
- C. Telnet
- D. Tracert
Answer: A
NEW QUESTION 8
How many possible sequence number combinations are there in TCP/IP protocol?
- A. 320 billion
- B. 32 million
- C. 4 billion
- D. 1 billion
Answer: C
NEW QUESTION 9
After attending a CEH security seminar, you make a list of changes you would like to perform on your
network to increase its security. One of the first things you change is to switch the Restrict Anonymous setting from 0 to 1 on your servers. This, as you were told, would prevent anonymous users from establishing a null session on the server.
Using User info tool mentioned at the seminar, you succeed in establishing a null session with one of the servers. Why is that?
- A. Restrict Anonymous must be set to "2" for complete security
- B. Restrict Anonymous must be set to "3" for complete security
- C. There is no way to always prevent an anonymous null session from establishing
- D. Restrict Anonymous must be set to "10" for complete security
Answer: A
NEW QUESTION 10
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
- A. Vulnerability Report
- B. Executive Report
- C. Client-side test Report
- D. Host Report
Answer: B
NEW QUESTION 11
George is a senior security analyst working for a state agency in Florida. His state's congress just passed a bill mandating every state agency to undergo a security audit annually. After learning what will be required, George needs to implement an IDS as soon as possible before the first audit occurs.
The state bill requires that an IDS with a "time-based induction machine" be used. What IDS feature must George implement to meet this requirement?
- A. Pattern matching
- B. Statistical-based anomaly detection
- C. Real-time anomaly detection
- D. Signature-based anomaly detection
Answer: C
NEW QUESTION 12
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum.
Different types of Internet Control Message Protocols (ICMPs) are identified by a type and code field.
Which of the following ICMP messages will be generated if the destination port is not reachable?
- A. ICMP Type 11 code 1
- B. ICMP Type 5 code 3
- C. ICMP Type 3 code 2
- D. ICMP Type 3 code 3
Answer: D
NEW QUESTION 13
You work as a penetration tester for Hammond Security Consultants. You are currently working on a contract for the state government of California. Your next step is to initiate a DoS attack on their network. Why would you want to initiate a DoS attack on a system you are testing?
- A. Use attack as a launching point to penetrate deeper into the network
- B. Demonstrate that no system can be protected against DoS attacks
- C. List weak points on their network
- D. Show outdated equipment so it can be replaced
Answer: C
NEW QUESTION 14
You work as an IT security auditor hired by a law firm in Boston to test whether you can gain access to
sensitive information about the company clients. You have rummaged through their trash and found very little information.
You do not want to set off any alarms on their network, so you plan on performing passive foot printing against their Web servers. What tool should you use?
- A. Nmap
- B. Netcraft
- C. Ping sweep
- D. Dig
Answer: B
NEW QUESTION 15
Terri works for a security consulting firm that is currently performing a penetration test on First National Bank in Tokyo. Terri's duties include bypassing firewalls and switches to gain access to the network. Terri sends an IP packet to one of the company's switches with ACK bit and the source address of her machine set.
What is Terri trying to accomplish by sending this IP packet?
- A. Poison the switch's MAC address table by flooding it with ACK bits
- B. Enable tunneling feature on the switch
- C. Trick the switch into thinking it already has a session with Terri's computer
- D. Crash the switch with a DoS attack since switches cannot send ACK bits
Answer: C
NEW QUESTION 16
To locate the firewall, SYN packet is crafted using Hping or any other packet crafter and sent to the firewall. If ICMP unreachable type 13 message (which is an admin prohibited packet) with a source IP address of the access control device is received, then it means which of the following type of firewall is in place?
- A. Circuit level gateway
- B. Stateful multilayer inspection firewall
- C. Packet filter
- D. Application level gateway
Answer: C
NEW QUESTION 17
Timing is an element of port-scanning that can catch one unaware. If scans are taking too long to complete or obvious ports are missing from the scan, various time parameters may need to be adjusted.
Which one of the following scanned timing options in NMAP’s scan is useful across slow WAN links or to hide the scan?
- A. Paranoid
- B. Sneaky
- C. Polite
- D. Normal
Answer: C
NEW QUESTION 18
Which of the following defines the details of services to be provided for the client’s organization and the list of services required for performing the test in the organization?
- A. Draft
- B. Report
- C. Requirement list
- D. Quotation
Answer: D
NEW QUESTION 19
One needs to run “Scan Server Configuration” tool to allow a remote connection to Nessus from the remote Nessus clients. This tool allows the port and bound interface of the Nessus daemon to be configured.
By default, the Nessus daemon listens to connections on which one of the following?
- A. Localhost (127.0.0.1) and port 1241
- B. Localhost (127.0.0.1) and port 1240
- C. Localhost (127.0.0.1) and port 1246
- D. Localhost (127.0.0.0) and port 1243
Answer: A
NEW QUESTION 20
Which one of the following tools of trade is an automated, comprehensive penetration testing product for assessing the specific information security threats to an organization?
- A. Sunbelt Network Security Inspector (SNSI)
- B. CORE Impact
- C. Canvas
- D. Microsoft Baseline Security Analyzer (MBSA)
Answer: C
NEW QUESTION 21
What will the following URL produce in an unpatched IIS Web Server?
- A. Execute a buffer flow in the C: drive of the web server
- B. Insert a Trojan horse into the C: drive of the web server
- C. Directory listing of the C:windowssystem32 folder on the web server
- D. Directory listing of C: drive on the web server
Answer: D
NEW QUESTION 22
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
- A. intitle:"exchange server"
- B. outlook:"search"
- C. locate:"logon page"
- D. allinurl:"exchange/logon.asp"
Answer: D
NEW QUESTION 23
Traffic on which port is unusual for both the TCP and UDP ports?
- A. Port 81
- B. Port 443
- C. Port 0
- D. Port 21
Answer: C
NEW QUESTION 24
ESTION NO: 92
In Linux, /etc/shadow file stores the real password in encrypted format for user’s account with added properties associated with the user’s password.
In the example of a /etc/shadow file below, what does the bold letter string indicate? Vivek: $1$fnffc$GteyHdicpGOfffXX40w#5:13064:0:99999:7
- A. Number of days the user is warned before the expiration date
- B. Minimum number of days required between password changes
- C. Maximum number of days the password is valid
- D. Last password changed
Answer: B
NEW QUESTION 25
TCP/IP provides a broad range of communication protocols for the various applications on the network. The TCP/IP model has four layers with major protocols included within each layer. Which one of the following protocols is used to collect information from all the network devices?
- A. Simple Network Management Protocol (SNMP)
- B. Network File system (NFS)
- C. Internet Control Message Protocol (ICMP)
- D. Transmission Control Protocol (TCP)
Answer: A
NEW QUESTION 26
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack into his former company's network. Since Simon remembers some of the server names, he attempts to run the AXFR and IXFR commands using DIG.
What is Simon trying to accomplish here?
- A. Enumerate all the users in the domain
- B. Perform DNS poisoning
- C. Send DOS commands to crash the DNS servers
- D. Perform a zone transfer
Answer: D
NEW QUESTION 27
The IP protocol was designed for use on a wide variety of transmission links. Although the maximum length of an IP datagram is 64K, most transmission links enforce a smaller maximum packet length limit, called a MTU.
The value of the MTU depends on the type of the transmission link. The design of IP accommodates MTU differences by allowing routers to fragment IP datagrams as necessary. The receiving station is responsible for reassembling the fragments back into the original full size IP datagram.
IP fragmentation involves breaking a datagram into a number of pieces that can be reassembled later. The IP source, destination, identification, total length, and fragment offset fields in the IP header, are used for IP fragmentation and reassembly.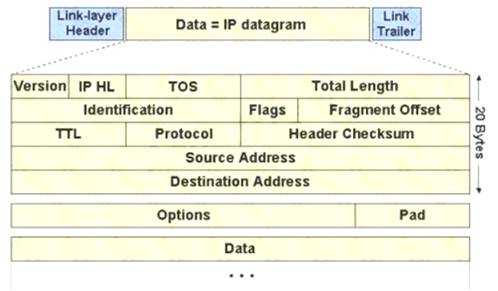
The fragment offset is 13 bits and indicates where a fragment belongs in the original IP datagram. This value is a:
- A. Multiple of four bytes
- B. Multiple of two bytes
- C. Multiple of eight bytes
- D. Multiple of six bytes
Answer: C
NEW QUESTION 28
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
- A. Frame Injection Attack
- B. LDAP Injection Attack
- C. XPath Injection Attack
- D. SOAP Injection Attack
Answer: D
NEW QUESTION 29
......
100% Valid and Newest Version ECSAv10 Questions & Answers shared by Dumps-hub.com, Get Full Dumps HERE: https://www.dumps-hub.com/ECSAv10-dumps.html (New 201 Q&As)
- Top Quality 312-50v9 Dumps 2021
- What Pinpoint 312-85 Actual Exam Is
- Vivid 712-50 Braindumps 2021
- The Improved Guide To ECSAv10 Dumps Questions
- All About High Value 312-50 Free Demo
- The Secret of EC-Council 312-50v10 dumps
- EC-Council 712-50 Braindumps 2021
- how many questions of 312-50v10 pdf?
- A Review Of Highest Quality 312-49v9 Exam Topics
- Validated 312-50v9 Braindumps 2021


