300-375 Exam Questions - Online Test
300-375 Premium VCE File

150 Lectures, 20 Hours
Cause all that matters here is passing the Cisco 300-375 exam. Cause all that you need is a high score of 300-375 Securing Cisco Wireless Enterprise Networks exam. The only one thing you need to do is downloading Pass4sure 300-375 exam study guides now. We will not let you down with our money-back guarantee.
Online Cisco 300-375 free dumps demo Below:
NEW QUESTION 1
When implementing secure PCI wireless networks, which two are specific recommendations in the PCI DSS? (Choose two)
- A. Use a minimum 12-character random passphrase with WPA
- B. Segment logging events with other networking devices within the organization.
- C. Use VLAN based segmentation with MAC filters.
- D. Change default settings.
- E. Implement strong wireless authentication
Answer: DE
Explanation:
Wireless networks that are part of the CDE must comply with all PCI DSS requirements. This includes using a firewall (requirement 1.2.3) and making sure that additional rogue wireless devices have not been added to the CDE (requirement 11.1). In addition, PCI DSS compliance for systems that include WLANs as a part of the CDE requires extra attention to WLAN specific technologies and processes such as:
A. Physical security of wireless devices, B. Changing default passwords and settings on wireless devices, C. Logging of wireless access and intrusion prevention, D. Strong wireless authentication and encryption, E. Use of strong cryptography and security protocols, and F. Development and enforcement of wireless usage policies. This section will cover each of these requirements sequentially. https://www.pcisecuritystandards.org/pdfs/PCI_DSS_Wireless_Guidelines.pdf
NEW QUESTION 2
Which EAP method can an AP use to authenticate to the wired network?
- A. EAP-GTC
- B. EAP-MD5
- C. EAP-TLS
- D. EAP-FAST
Answer: C
NEW QUESTION 3
A wireless engineer wants to view how many wIPS alerts have been detected in Cisco Prime. Which tab does the engineer select in the wireless dashboard?
- A. Security
- B. Cleanair
- C. Context Aware
- D. Mesh
Answer: A
NEW QUESTION 4
An engineer is implementing SNMP v3 on a Cisco 5700 Series WLC. Which three commands are the
minimum needed to configure SNMP v3? (Choose three.)
- A. snmp-server enable traps
- B. snmp-server group
- C. snmp-server user
- D. snmp-server community
- E. snmp-server context
- F. snmp-server engineID
Answer: BCF
NEW QUESTION 5
Refer to the exhibit.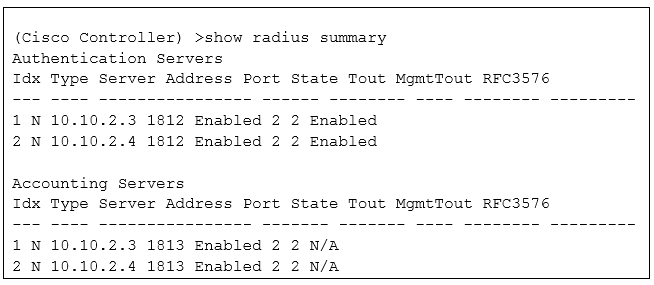
An engineer utilizing ISE as the wireless AAA service noticed that the accounting process on the server at 10.10.2.3 has failed, but authentication process is still functional.
Which ISE nodes receive WLC RADIUS traffic, using the CLI output and assuming the WLAN uses the servers in their indexed order?
- A. authentication to 10.10.2.4, accounting to 10.10.2.3.
- B. authentication to 10.10.2.3, accounting to 10.10.2.3.
- C. authentication to 10.10.2.4, accounting to 10.10.2.4.
- D. authentication to 10.10.2.3, accounting to 10.10.2.4.
Answer: B
NEW QUESTION 6
Clients are failing EAP authentication. A debug shows that an EAPOL start is sent and the clients are then de-authenticated. Which two issues can cause this problem? (Choose two.)
- A. The WLC certificate has changed.
- B. The WLAN is not configured for the correct EAP supplicant type.
- C. The shared secret of the WLC and RADIUS server do not match.
- D. The WLC has not been added to the RADIUS server as a client.
- E. The clients are configured for machine authentication, but the RADIUS server is configured for user authentication.
Answer: CD
NEW QUESTION 7
What are two of the benefits that the Cisco AnyConnect v3.0 provides to the administrator for client WLAN security configuration? (Choose two.)
- A. Provides a reporting mechanism for rouge APs
- B. Prevents a user from adding any WLANs
- C. Hides the complexity of 802.1X and EAP configuration
- D. Supports centralized or distributed client architectures
- E. Provides concurrent wired and wireless connectivity
- F. Allows users to modify but not delete admin-created profiles
Answer: CD
NEW QUESTION 8
After receiving an alert regarding a rogue AP, a network engineer logs into Cisco Prime and looks at the floor map where the AP that detected the rogue is located. The map is synchronized with a mobility services engine that determines the rogue device is actually inside the campus. The engineer determines the rogue to be a security threat and decides to stop it from broadcasting inside the enterprise wireless network. What is the fastest way to disable the rogue?
- A. Go to the location the rogue device is indicated to be and disable the power.
- B. Create an SSID on WLAN controller resembling the SSID of the rogue to spoof it and disable clients from connecting to it.
- C. Classify the rogue as malicious in Cisco Prime.
- D. Update the status of the rogue in Cisco Prime to containe
Answer: C
NEW QUESTION 9
A new MSE with wIPS service has been installed and no alarm information appears to be reaching
the MSE from controllers.
What protocol must be allowed to reach the MSE from the controllers?
- A. NMSP
- B. SOAP/XML
- C. SNMP
- D. CAPWAP
Answer: B
NEW QUESTION 10
An engineer requires authentication for WPA2 that will use fast rekeying to enable clients to roam from one access point to another without going through the controller. Which security option should be configured?
- A. PSK
- B. AES
- C. Cisco Centralized key Management
- D. 802.1x
Answer: C
NEW QUESTION 11
An engineer is configuring EAP-TLS with a client trusting server model and has configured a public root certification authority. Which action does this allow?
- A. specifies a second certification authority to trust
- B. utilizes two subcertification authority servers
- C. creates a PKI infrastructure
- D. validates the AAA server
Answer: D
Explanation:
To support EAP-TLS, the AAA server (for example, Cisco Secure ACS) must have a certificate. Either a public certification authority or a private certification authority can be used to issue the AAA server certificate. The AAA server will trust a client certificate that was issued from the same root
certification authority that issued its certificate.
https://www.cisco.com/en/US/tech/ CK7 22/ CK8 09/technologies_white_paper09186a008009256b.sht ml
NEW QUESTION 12
An engineer is designing a high availability wireless network. What mechanism should be the focus for high availability?
- A. SNR
- B. channel reuse
- C. RSSI
- D. cell overlap
Answer: B
Explanation:
Describe basic RF deployment considerations related to site survey design of data or VoWLAN applications, common RF interference sources such as devices, building material, AP location, and basic RF site survey design related to channel reuse, signal strength, and cell overlap
NEW QUESTION 13
A customer is concerned about DOS attacks from a neighboring facility. Which feature can be enabled to help alleviate these concerns and mitigate DOS attacks on a WLAN?
- A. PMF
- B. peer-to-peer blocking
- C. Cisco Centralized Key Management
- D. split tunnel
Answer: A
NEW QUESTION 14
A wireless engineer want to how many wlPS alerts have been detected in CISCO Prime. Which tab does the engineer select in the windows dashboard?
- A. Security
- B. CleanAir
- C. Context Aware
- D. Mesh
Answer: A
Explanation:
Security Index, including the top security issues Adaptive WIPS Rogue classification graph Rogue containment graph Attacks detected Malicious, unclassified, friendly, and custom rogue APs CleanAir security Adhoc rogues Security https://www.cisco.com/c/en/us/td/docs/net_mgmt/prime/infrastructure/3-
1/user/guide/pi_ug/view-dash.html
NEW QUESTION 15
Which customizable security report on Cisco Prime Infrastructure would show rogue APs detected since a point in time?
- A. New Rogue APs
- B. Rogue AP Events
- C. Rogue APs
- D. Rogue AP Count Summary
- E. Network Summary
Answer: C
NEW QUESTION 16
Regarding the guidelines for using MFP, under what circumstances will a client without Cisco compatible Extensions v5 be able to associate to a WLAN?
- A. The DHCP Required box is unchecked.
- B. AAA override is configured for the WLAN
- C. Client MFP is disabled or optional.
- D. WPA2 is enabled with TKIP or AE
Answer: D
NEW QUESTION 17
Which three methods are valid for guest wireless using web authentication? (Choose three.)
- A. LDAP
- B. SSL
- C. local
- D. TLS
- E. EAP-TLS
- F. RADIUS
Answer: ACF
Explanation:
There are three ways to authenticate users when you use web authentication. Local authentication allows you to authenticate the user in the Cisco WLC. You can also use an external RADIUS server or a LDAP server as a backend database in order to authenticate the users.
https://www.sslshopper.com/ssl-certificate-not-trusted-error.html
NEW QUESTION 18
An engineer is configuring client MFP. What WLAN Layer 2 security must be selected to use client MFP?
- A. Static WEP
- B. CKIP
- C. WPA+WPA2
- D. 802 1x
Answer: C
NEW QUESTION 19
Which two attacks represent a social engineering attack? (Choose two.)
- A. using AirMagnet Wi-Fi Analyzer to search for hidden SSIDs
- B. calling the IT helpdesk and asking for network information
- C. spoofing the MAC address of an employee device
- D. entering a business and posing as IT support staff
Answer: BD
NEW QUESTION 20
Which two statements describe the requirements for EAP-TLS?
- A. It requires client-side and server-side certificates.
- B. It uses PAC on the client.
- C. It requires PKI.
- D. It requires a server side digital certificate on only the RADIUS server
- E. It must use AES for encryption and cannot use TKIP for encryptio
Answer: AB
NEW QUESTION 21
WPA2 Enterprise with 802.1x is being used for clients to authenticate to a wireless network through
an ACS server. For security reasons, the network engineer wants to ensure only PEAP authentication can be used. The engineer sent instructions to clients on how to configure their supplicants, but users are still in the ACS logs authentication using EAP-FAST. Which option describes the most efficient way the engineer can ensure these users cannot access the network unless the correct authentication mechanism is configured?
- A. Enable AAA override on the SSID, gather the usernames of these users, and disable their RADIUS accounts until they make sure they correctly configured their devices.
- B. Enable AAA override on the SSID and configure an access policy in ACS that denies access to the list of MACs that have used EAP-FAST.
- C. Enable AAA override on the SSID and configure an access policy in ACS that allows access only when the EAP authentication method is PEAP.
- D. Enable AAA override on the SSID and configure an access policy in ACS that puts clients that authenticated using EAP-FAST into a quarantine VLAN.
Answer: D
NEW QUESTION 22
Refer to the exhibit.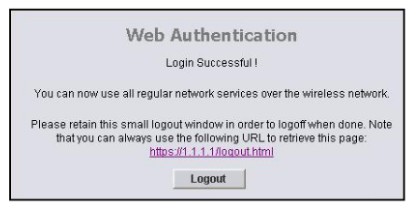
What is the 1.1.1.1 IP address?
- A. the wireless client IP address
- B. the RADIUS server IP address
- C. the controller management IP address
- D. the lightweight IP address
- E. the controller AP-manager IP address
- F. the controller virtual interface IP address
Answer: F
NEW QUESTION 23
Which three properties are used for client profiling of wireless clients? (Choose Three)
- A. MAC OUI
- B. IP Address
- C. HTTP user agent
- D. DHCP
- E. hostname
- F. OS Version
Answer: ACD
NEW QUESTION 24
Which two considerations must a network engineer have when planning for voice over wireless roaming? (Choose two.)
- A. Roaming with only 802.1x authentication requires full reauthentication.
- B. Full reauthentication introduces gaps in a voice conversation.
- C. Roaming occurs when e phone has seen at least four APs.
- D. Roaming occurs when the phone has reached -80 dBs or belo
Answer: AB
NEW QUESTION 25
......
100% Valid and Newest Version 300-375 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/300-375-exam-dumps.html (New 124 Q&As)
- Realistic 642-887 Study Guides 2021
- 10 Tips For Up to date 300-208 practice test
- What Printable 200-125 pdf Is?
- Top Quality CCNP Collaboration 300-075 dumps
- Regenerate 210-455 Braindump 2021
- Abreast of the times 400-051 Exam Study Guides With New Update Exam Questions
- Breathing CCDP 300-320 pdf
- The Latest Guide To 300-101 pdf
- All About Download 300-206 exam question
- All About 100% Guarantee 300-075 vce


