SC-100 Exam Questions - Online Test
SC-100 Premium VCE File

150 Lectures, 20 Hours
Actualtests SC-100 Questions are updated and all SC-100 answers are verified by experts. Once you have completely prepared with our SC-100 exam prep kits you will be ready for the real SC-100 exam without a problem. We have Up to the minute Microsoft SC-100 dumps study guide. PASSED SC-100 First attempt! Here What I Did.
Check SC-100 free dumps before getting the full version:
NEW QUESTION 1
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions that allow traffic from the Front Door service tags. Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 2
You have an Azure subscription that contains several storage accounts. The storage accounts are accessed by legacy applications that are authenticated by using access keys.
You need to recommend a solution to prevent new applications from obtaining the access keys of the storage accounts. The solution must minimize the impact on the legacy applications.
What should you include in the recommendation?
- A. Apply read-only locks on the storage accounts.
- B. Set the AllowSharcdKeyAccess property to false.
- C. Set the AllowBlobPublicAcccss property to false.
- D. Configure automated key rotation.
Answer: A
NEW QUESTION 3
You have Microsoft Defender for Cloud assigned to Azure management groups. You have a Microsoft Sentinel deployment.
During the triage of alerts, you require additional information about the security events, including suggestions for remediation. Which two components can you use to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. workload protections in Defender for Cloud
- B. threat intelligence reports in Defender for Cloud
- C. Microsoft Sentinel notebooks
- D. Microsoft Sentinel threat intelligence workbooks
Answer: A
NEW QUESTION 4
You have a hybrid cloud infrastructure.
You plan to deploy the Azure applications shown in the following table.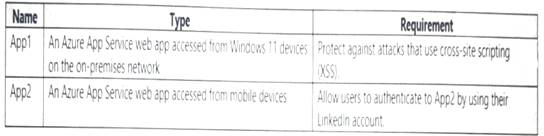
What should you use to meet the requirement of each app? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 5
Your company has a third-party security information and event management (SIEM) solution that uses Splunk and Microsoft Sentinel. You plan to integrate Microsoft Sentinel with Splunk.
You need to recommend a solution to send security events from Microsoft Sentinel to Splunk. What should you include in the recommendation?
- A. Azure Event Hubs
- B. Azure Data Factor
- C. a Microsoft Sentinel workbook
- D. a Microsoft Sentinel data connector
Answer: C
NEW QUESTION 6
You are planning the security requirements for Azure Cosmos DB Core (SQL) API accounts. You need to recommend a solution to audit all users that access the data in the Azure Cosmos DB accounts. Which two configurations should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A. Enable Microsoft Defender for Cosmos DB.
- B. Send the Azure Active Directory (Azure AD) sign-in logs to a Log Analytics workspace.
- C. Disable local authentication for Azure Cosmos DB.
- D. Enable Microsoft Defender for Identity.
- E. Send the Azure Cosmos DB logs to a Log Analytics workspace.
Answer: AD
NEW QUESTION 7
Your company is developing a serverless application in Azure that will have the architecture shown in the following exhibit.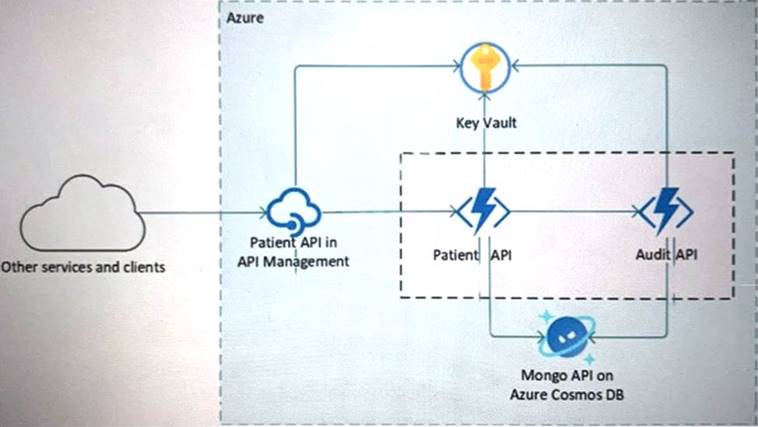
You need to recommend a solution to isolate the compute components on an Azure virtual network. What should you include in the recommendation?
- A. Azure Active Directory (Azure AD) enterprise applications
- B. an Azure App Service Environment (ASE)
- C. Azure service endpoints
- D. an Azure Active Directory (Azure AD) application proxy
Answer: B
NEW QUESTION 8
Your on-premises network contains an e-commerce web app that was developed in Angular and Node.js. The web app uses a MongoDB database You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.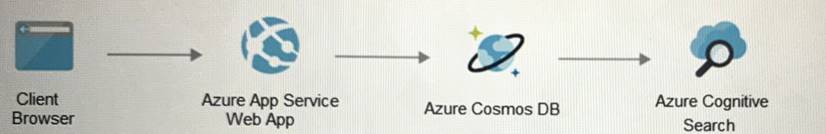
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model.
Solution: You recommend implementing Azure Application Gateway with Azure Web Application Firewall (WAF). Does this meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 9
Your company has a Microsoft 365 E5 subscription, an Azure subscription, on-premises applications, and Active Directory Domain Services (AD DSV You need to recommend an identity security strategy that meets the following requirements:
• Ensures that customers can use their Facebook credentials to authenticate to an Azure App Service website
• Ensures that partner companies can access Microsoft SharePoint Online sites for the project to which they are assigned
The solution must minimize the need to deploy additional infrastructure components. What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 10
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains a Microsoft Sentinel workspace. Microsoft Sentinel data connectors are configured for Microsoft 365, Microsoft 365 Defender, Defender for Cloud, and Azure.
You plan to deploy Azure virtual machines that will run Windows Server.
You need to enable extended detection and response (EDR) and security orchestration, automation, and response (SOAR) capabilities for Microsoft Sentinel.
How should you recommend enabling each capability? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 11
You need to design a solution to provide administrators with secure remote access to the virtual machines. The solution must meet the following requirements:
• Prevent the need to enable ports 3389 and 22 from the internet.
• Only provide permission to connect the virtual machines when required.
• Ensure that administrators use the Azure portal to connect to the virtual machines.
Which two actions should you include in the solution? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A. Enable Azure Active Directory (Azure AD) Privileged Identity Management (PIM) roles as virtual machine contributors.
- B. Configure Azure VPN Gateway.
- C. Enable Just Enough Administration (JEA).
- D. Enable just-in-time (JIT) VM access.
- E. Configure Azure Bastion.
Answer: CE
NEW QUESTION 12
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend configuring gateway-required virtual network integration. Does this meet the goal?
- A. Yes
- B. No
Answer: A
NEW QUESTION 13
Your company has a Microsoft 365 E5 subscription.
The Chief Compliance Officer plans to enhance privacy management in the working environment. You need to recommend a solution to enhance the privacy management. The solution must meet the following requirements:
• Identify unused personal data and empower users to make smart data handling decisions.
• Provide users with notifications and guidance when a user sends personal data in Microsoft Teams.
• Provide users with recommendations to mitigate privacy risks. What should you include in the recommendation?
- A. Microsoft Viva Insights
- B. Advanced eDiscovery
- C. Privacy Risk Management in Microsoft Priva
- D. communication compliance in insider risk management
Answer: A
NEW QUESTION 14
Your company is developing a modern application that will run as an Azure App Service web app. You plan to perform threat modeling to identify potential security issues by using the Microsoft Threat Modeling Tool.
Which type of diagram should you create?
- A. dataflow
- B. system flow
- C. process flow
- D. network flow
Answer: C
NEW QUESTION 15
Your company plans to deploy several Azure App Service web apps. The web apps will be deployed to the West Europe Azure region. The web apps will be accessed only by customers in Europe and the United States.
You need to recommend a solution to prevent malicious bots from scanning the web apps for vulnerabilities. The solution must minimize the attach surface.
What should you include in the recommendation?
- A. Azure Firewall Premium
- B. Azure Application Gateway Web Application Firewall (WAF)
- C. network security groups (NSGs)
- D. Azure Traffic Manager and application security groups
Answer: D
NEW QUESTION 16
......
Recommend!! Get the Full SC-100 dumps in VCE and PDF From Allfreedumps.com, Welcome to Download: https://www.allfreedumps.com/SC-100-dumps.html (New 105 Q&As Version)
- Microsoft 70-743 Exam Dumps 2021
- What Top Quality 70-535 exam Is?
- Practical 70-742 Exam Dumps 2021
- Abreast Of The Times SC-300 Exam Answers For Microsoft Identity And Access Administrator Certification
- What Vivid 70-410 vce Is?
- Replace 70-412 Exam Study Guides With New Update Exam Questions
- Verified AZ-203 Study Guides 2021
- Approved AZ-300 Bundle 2021
- Up to the minute 70-494 Exam Study Guides With New Update Exam Questions
- What Real AZ-720 Study Guide Is


