P2150-870 Exam Questions - Online Test
P2150-870 Premium VCE File

150 Lectures, 20 Hours
Exam Code: P2150-870 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Technical Sales Foundations for IBM Security Intelligence and Analytics V1
Certification Provider: IBM
Free Today! Guaranteed Training- Pass P2150-870 Exam.
Free P2150-870 Demo Online For IBM Certifitcation:
NEW QUESTION 1
Which case shows how approximately 1000 Events per second, using an encrypted channel, can be sent from a private cloud to a QRader processor?
- A. Place an event processor in the private cloud, and forward the events to another event collector.
- B. Place a risk manager appliance in the private cloud, and forward the events to another event collector.
- C. Place a packet capture appliance in the private cloud, and forward the events to a cloud events processor.
- D. Place an event collector in the private cloud, and forward the event to the customers event processor.
Answer: A
NEW QUESTION 2
What is the QRadar 14xx Data Node used for? It is used to:
- A. offload Offense management tasks from a multi-tenant 31 xx appliance.
- B. provide a long term data backup store for 16xx, 17xx, 18xx and 31 xx appliances.
- C. provide additional storage and processing for 16x
- D. 17xx, 18xx and 31 xx appliances.
- E. run complex 'Machine Learning' style applications in the QRadar application framework.
Answer: B
NEW QUESTION 3
Which question(s) con QRadar help customers answer concerning the security of their network?
- A. Who is attacking?
- B. What is being attacked?
- C. What is the security impact?
- D. When are the attacks taking place?
- E. All the above
Answer: D
NEW QUESTION 4
Assuming relevant indexing is enabled, which is the fastest way to search recent data in an ad-hoc manner?
- A. AQL
- B. Quick Filters
- C. Quick Searches
- D. Saved Searches
Answer: C
NEW QUESTION 5
How can QRadar Network Security improve security posture for companies? By using QRadar Network Security, companies can:
- A. implement an application firewall.
- B. perform event monitoring.
- C. perform vulnerability scanning to detect vulnerabilities.
- D. perform application contro
- E. SSL inspection, and disrupt advanced malware
Answer: A
NEW QUESTION 6
What is the least secure of the five transmission types?
- A. Wireless
- B. Fiber Optic
- C. Coaxial Cable
- D. Shielded Twisted Pair
- E. Unshielded Twisted Pair
Answer: C
NEW QUESTION 7
Which metrics are defined for the three virtual appliance system specification (Minimum/Medium/High). (select 4)
- A. NICs
- B. IOPS
- C. Memory
- D. Storage
- E. CPU cores/speed
- F. Maximum Latency
- G. Virtual Networks
Answer: ACEG
NEW QUESTION 8
Which types of software appliance are involved of an events is received by an Event Collector, and the event is then to an Event Processor and causes an Offense to be updated on the Console?
- A. 13xx to 17xx to 31xx
- B. 13xx to 18xxt o 21xx
- C. 13xx to 16xx to 31xx
- D. 15xx to 17xx to 21xx
Answer: C
NEW QUESTION 9
How can assets be used to help in investigations?
- A. As valuable data sources.
- B. Make searching for offenses easier.
- C. Help connect an offense to a device.
- D. Provide external threat intelligence.
Answer: D
NEW QUESTION 10
What would be relevant questions to ask for scoping the environment? (Select 3)
- A. How many data centers do you have?
- B. How many users will be using QRadar?
- C. How many storage networks to you have?
- D. How many QRadar appliances do you want to acquire?
- E. How many log sources do you want to add to the project?
- F. In how many countries do you want to deploy QRadar?
- G. Which compliance extensions do you need to deploy?
Answer: CFG
NEW QUESTION 11
Which is standard on a QRadar on Cloud deployment?
- A. High Availability
- B. Packet analysis
- C. Vulnerability Management
- D. Custom log source development
Answer: B
NEW QUESTION 12
In this diagram, showing the Ariel Search Flow, what is the name of the components as ‘X’, running on the Console?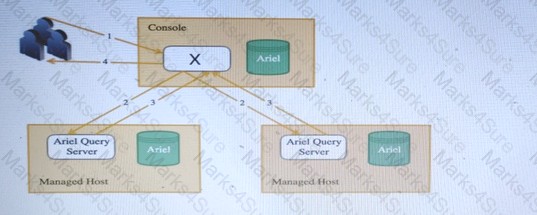
- A. AQL Processor
- B. Ariel Proxy Server
- C. Ariel Query Server
- D. REST -API endpoint
Answer: A
NEW QUESTION 13
Which attributes would contribute to an effective demonstration of QRadar?
- A. Bring a whiteboard since prospect might not have on
- B. Show what each tab of the QRadar interface does.
- C. Show all analysis features on flow dat
- D. Focus on the functions that the prospect asked for
- E. Explain all extension options for add-ons to the prospec
- F. Explain QRadar's architecture and scalability.
- G. Tell a story on how QRadar solves an issue that is relevant to the prospec
- H. Talk about the benefits of QRadar in relation to the prospect's situation.
Answer: C
NEW QUESTION 14
Which is the most common formatused to send event data to a SIEM?
- A. JSON
- B. LEEF
- C. Syslog
- D. NetFlow
Answer: D
NEW QUESTION 15
What are offenses used for?
- A. To track the time spent investigating incidents by an Analyst.
- B. To provide incident statistics based on rule group membership.
- C. To bundle information about a suspicious activity, including events and flows.
- D. To allow the Historical Correlation engine to check for previous occurrences of security incidents
Answer: A
NEW QUESTION 16
An attacker, who has physical access to the premises, has connected a personal laptop to the network in an attempt to sniff traffic and record any clear text passwords. This scenario would be classified as which type of attack?
- A. Fabrication
- B. Interception
- C. Modification
- D. Interruption
Answer: D
NEW QUESTION 17
Which subjects should be covered when first demonstrating QRadar?
- A. 1. The devices QRadar supports.2. How to write rules to detect spear-fishing attacks.3. How much EPS QRadar can handle on a single box.4. Why QRadar should be chosen.
- B. 1. The QRadar add-on
- C. and what problems they solve.2. How QRadar add-ons work.3. How to create a custom extracted property from a custom log source.4. A use case involving different geographies, and its integration to a physical security system (badge reader).
- D. 1. The problem QRadar solves.2. How QRadar works (i.e.. data integration, correlation and offenses).3. Use cases that apply to the client's business.4. QRadar's competitive advantages
- E. 1. The programming languages used to build QRadar.2. The cost per EPS and FPM3. Building a use case in QRadar's rule wizard.4. A POC so client can personally test the product.
Answer: A
NEW QUESTION 18
What are thesystems called which send events to QRadar?
- A. Assets
- B. Firewalls
- C. Log Sources
- D. Data Backups
Answer: D
NEW QUESTION 19
Organizations have too many vulnerabilities to remediate and need to focus on the ones that represent the highest risks.
Which question should the prospect be asked to start a conversation on this topic?
- A. Do you currently use a vulnerability scanner?
- B. Can you show me the server room to see the physical security measures?
- C. Do you like the reports you get out of your current Vulnerability Assessment tool?
- D. How do you currently patch vulnerabilities that are most likely to be exploited first?
Answer: A
NEW QUESTION 20
......
P.S. Certshared now are offering 100% pass ensure P2150-870 dumps! All P2150-870 exam questions have been updated with correct answers: https://www.certshared.com/exam/P2150-870/ (40 New Questions)
- The Renew Guide To 1Y0-204 Free Download
- Top Quality C1000-010 Answers 2021
- The Secret Of IBM C1000-002 Questions Pool
- how many questions of C2010-530 exam dumps?
- All About 100% Guarantee C2010-555 Sample Question
- Top Quality IBM C2090-320 exam dumps
- Update C2010-555 Test Questions For IBM Maximo Asset Management V7.6 Functional Analyst Certification
- How Many Questions Of C9560-503 Braindumps
- Improved C2150-606 Test For IBM Security Guardium V10.0 Administration Certification
- Latest C5050-380 Exam Study Guides With New Update Exam Questions


