CISSP Exam Questions - Online Test
CISSP Premium VCE File

150 Lectures, 20 Hours
We provide cissp all in one which are the best for clearing CISSP test, and to get certified by ISC2 Certified Information Systems Security Professional (CISSP). The cissp bootcamp covers all the knowledge points of the real CISSP exam. Crack your ISC2 CISSP Exam with latest dumps, guaranteed!
Online ISC2 CISSP free dumps demo Below:
NEW QUESTION 1
An internal Service Level Agreement (SLA) covering security is signed by senior managers and is in place. When should compliance to the SLA be reviewed to ensure that a good security posture is being delivered?
- A. As part of the SLA renewal process
- B. Prior to a planned security audit
- C. Immediately after a security breach
- D. At regularly scheduled meetings
Answer: D
NEW QUESTION 2
Which Web Services Security (WS-Security) specification handles the management of security tokens and the underlying policies for granting access? Click on the correct specification in the image below.
Answer:
Explanation: WS-Authorization
Reference: Java Web Services: Up and Running” By Martin Kalin page 228
NEW QUESTION 3
A security compliance manager of a large enterprise wants to reduce the time it takes to perform network, system, and application security compliance audits while increasing quality and effectiveness of the results. What should be implemented to BEST achieve the desired results?
- A. Configuration Management Database (CMDB)
- B. Source code repository
- C. Configuration Management Plan (CMP)
- D. System performance monitoring application
Answer: C
NEW QUESTION 4
Copyright provides protection for which of the following?
- A. Ideas expressed in literary works
- B. A particular expression of an idea
- C. New and non-obvious inventions
- D. Discoveries of natural phenomena
Answer: B
NEW QUESTION 5
An organization decides to implement a partial Public Key Infrastructure (PKI) with only the servers having digital certificates. What is the security benefit of this implementation?
- A. Clients can authenticate themselves to the servers.
- B. Mutual authentication is available between the clients and servers.
- C. Servers are able to issue digital certificates to the client.
- D. Servers can authenticate themselves to the client.
Answer: D
NEW QUESTION 6
When implementing a secure wireless network, which of the following supports authentication and authorization for individual client endpoints?
- A. Temporal Key Integrity Protocol (TKIP)
- B. Wi-Fi Protected Access (WPA) Pre-Shared Key (PSK)
- C. Wi-Fi Protected Access 2 (WPA2) Enterprise
- D. Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP)
Answer: C
NEW QUESTION 7
Which of the following Disaster Recovery (DR) sites is the MOST difficult to test?
- A. Hot site
- B. Cold site
- C. Warm site
- D. Mobile site
Answer: B
NEW QUESTION 8
The birthday attack is MOST effective against which one of the following cipher technologies?
- A. Chaining block encryption
- B. Asymmetric cryptography
- C. Cryptographic hash
- D. Streaming cryptography
Answer: C
NEW QUESTION 9
What is the GREATEST challenge to identifying data leaks?
- A. Available technical tools that enable user activity monitoring.
- B. Documented asset classification policy and clear labeling of assets.
- C. Senior management cooperation in investigating suspicious behavior.
- D. Law enforcement participation to apprehend and interrogate suspects.
Answer: B
NEW QUESTION 10
A company was ranked as high in the following National Institute of Standards and Technology (NIST) functions: Protect, Detect, Respond and Recover. However, a low maturity grade was attributed to the Identify function. In which of the following the controls categories does this company need to improve when analyzing its processes individually?
- A. Asset Management, Business Environment, Governance and Risk Assessment
- B. Access Control, Awareness and Training, Data Security and Maintenance
- C. Anomalies and Events, Security Continuous Monitoring and Detection Processes
- D. Recovery Planning, Improvements and Communications
Answer: A
NEW QUESTION 11
Given the various means to protect physical and logical assets, match the access management area to the technology.
Answer:
Explanation: 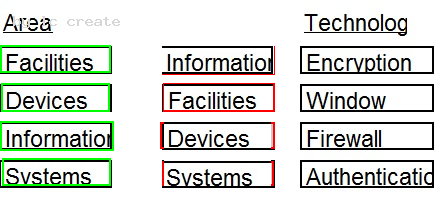
NEW QUESTION 12
When is security personnel involvement in the Systems Development Life Cycle (SDLC) process MOST beneficial?
- A. Testing phase
- B. Development phase
- C. Requirements definition phase
- D. Operations and maintenance phase
Answer: C
NEW QUESTION 13
From a cryptographic perspective, the service of non-repudiation includes which of the following features?
- A. Validity of digital certificates
- B. Validity of the authorization rules
- C. Proof of authenticity of the message
- D. Proof of integrity of the message
Answer: C
NEW QUESTION 14
Which technology is a prerequisite for populating the cloud-based directory in a federated identity solution?
- A. Notification tool
- B. Message queuing tool
- C. Security token tool
- D. Synchronization tool
Answer: C
NEW QUESTION 15
What would be the MOST cost effective solution for a Disaster Recovery (DR) site given that the organization’s systems cannot be unavailable for more than 24 hours?
- A. Warm site
- B. Hot site
- C. Mirror site
- D. Cold site
Answer: A
NEW QUESTION 16
Which one of the following data integrity models assumes a lattice of integrity levels?
- A. Take-Grant
- B. Biba
- C. Harrison-Ruzzo
- D. Bell-LaPadula
Answer: B
NEW QUESTION 17
An organization plan on purchasing a custom software product developed by a small vendor to support its
business model. Which unique consideration should be made part of the contractual agreement potential long-term risks associated with creating this dependency?
- A. A source code escrow clause
- B. Right to request an independent review of the software source code
- C. Due diligence form requesting statements of compliance with security requirements
- D. Access to the technical documentation
Answer: B
P.S. Easily pass CISSP Exam with 653 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader CISSP Dumps: https://www.certleader.com/CISSP-dumps.html (653 New Questions)
- Top Tips Of Improved SSCP Free Exam
- High Quality CISSP-ISSAP Study Guides 2021
- Realistic CISSP Dumps 2021
- The Secret Of ISC2 SSCP Preparation Labs
- All About Vivid SSCP Exam Topics
- Highest Quality CCSP Study Guides 2021
- The Secret Of ISC2 SSCP Exam Prep
- ISC2 CISSP Braindumps 2021
- ISC2 CISSP Exam Dumps 2021
- ISC2 CCSP Exam Dumps 2021


