350-901 Exam Questions - Online Test
350-901 Premium VCE File

150 Lectures, 20 Hours
Proper study guides for Renew Cisco Developing Applications using Cisco Core Platforms & APIs certified begins with Cisco 350-901 preparation products which designed to deliver the Downloadable 350-901 questions by making you pass the 350-901 test at your first time. Try the free 350-901 demo right now.
Also have 350-901 free dumps questions for you:
NEW QUESTION 1
Which two strategies are used to protect personally identifiable information? (Choose two.)
- A. Encrypt data in transit.
- B. Encrypt hash values of data.
- C. Encrypt data at rest.
- D. Only hash usernames and passwords for efficient lookup.
- E. Only encrypt usernames and passwords for efficient lookup.
Answer: AB
NEW QUESTION 2
Refer to the exhibit. This snippet of a script has recently started exiting abnormally with an exception stating “Unexpected HTTP Response code: 429”. Which solution handles rate limiting by the remote API?
- A.

- B.

- C.

- D.
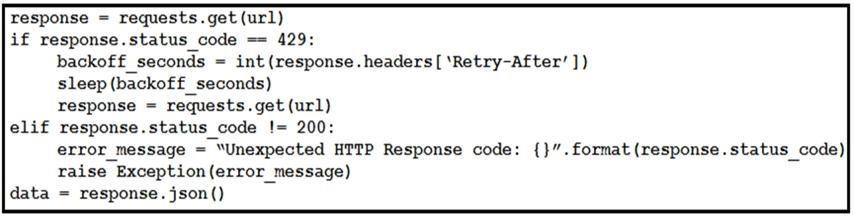
Answer: D
NEW QUESTION 3
A developer needs to configure an environment to orchestrate and configure. Which two tools should be used for each task? (Choose two.)
- A. Puppet for orchestration
- B. Terraform for orchestration
- C. Terraform for configuration
- D. Ansible for orchestration
- E. Ansible for configuration
Answer: BE
NEW QUESTION 4
A heterogeneous network of vendors and device types needs automating for better efficiency and to enable future automated testing. The network consists of switches, routers, firewalls and load balancers from different vendors, however they all support the NETCONF/RESTCONF configuration standards and the YAML models with every feature the business requires. The business is looking for a buy versus build solution because they cannot dedicate engineering resources, and they need configuration diff and rollback functionality from day 1.
Which configuration management for automation tooling is needed for this solution?
- A. Ansible
- B. Ansible and Terraform
- C. NSO
- D. Terraform
- E. Ansible and NSO
Answer: E
NEW QUESTION 5
Which two statements about a stateless application are true? (Choose two.)
- A. Different requests can be processed by different servers.
- B. Requests are based only on information relayed with each request.
- C. Information about earlier requests must be kept and must be accessible.
- D. The same server must be used to process all requests that are linked to the same state.
- E. No state information can be shared across servers.
Answer: AB
NEW QUESTION 6
A network operations team is using the cloud to automate some of their managed customer and branch locations. They require that all of their tooling be ephemeral by design and that the entire automation environment can be recreated without manual commands. Automation code and configuration state will be stored in git for change control and versioning. The engineering high-level plan is to use VMs in a cloud-provider environment then configure open source tooling onto these VMs to poll, test, and configure the remote devices, as well as deploy the tooling itself.
Which configuration management and/or automation tooling is needed for this solution?
- A. Ansible
- B. Ansible and Terraform
- C. NSO
- D. Terraform
- E. Ansible and NSO
Answer: B
NEW QUESTION 7
An application has initiated an OAuth authorization code grant flow to get access to an API resource on behalf of an end user.
Which two parameters are specified in the HTTP request coming back to the application as the end user grants access? (Choose two.)
- A. access token and a refresh token with respective expiration times to access the API resource
- B. access token and expiration time to access the API resource
- C. redirect URI a panel that shows the list of permissions to grant
- D. code that can be exchanged for an access token
- E. state can be used for correlation and security checks
Answer: AB
NEW QUESTION 8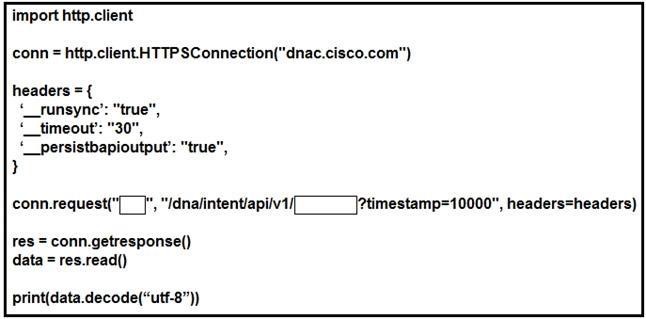
Refer to the exhibit. Which configuration of method and parameter retrieves the health of a laptop connected to the network from Cisco DNA Center?
- A. PUT; network-health;
- B. GET; client-health;
- C. GET; network-device;
- D. POST; network-device;
Answer: C
NEW QUESTION 9
DRAG DROP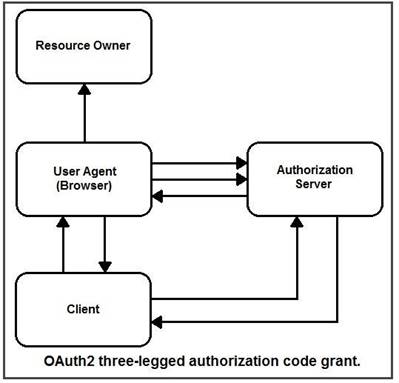
Refer to the exhibit. Drag and drop the steps from the left into the correct order of operation on the right for a successful OAuth2 three-legged authorization code grant flow.
Select and Place: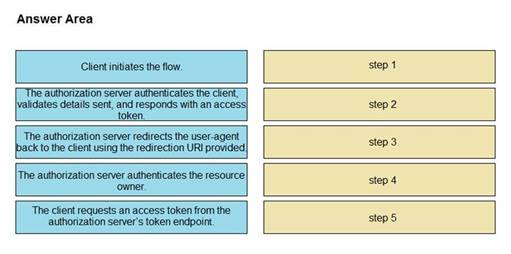
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 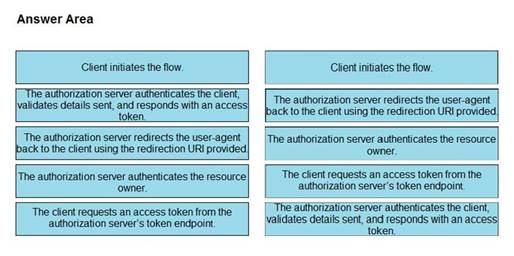
NEW QUESTION 10
Which RFC5988 (Web Linking) relation type is used in the Link header to control pagination in APIs?
- A. rel=”index”
- B. rel=”page”
- C. rel=”next”
- D. rel=”section”
Answer: C
NEW QUESTION 11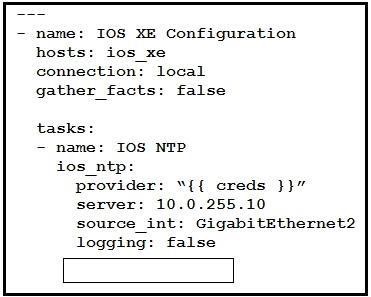
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module creates an NTP server peer?
- A. state: present
- B. state: True
- C. config: present
- D. config: True
Answer: A
NEW QUESTION 12
Into which two areas are AppDynamics APIs categorized? (Choose two.)
- A. application-centric
- B. analytics-events
- C. database-visibility
- D. platform-side
- E. agent-side
Answer: DE
NEW QUESTION 13
Which tow actions must be taken when an observable microservice application is developed? (Choose two.)
- A. Know the state of a single instance of a single service.
- B. Place “try/except” statement in code.
- C. Place log statements in the code.
- D. Use distributed tracing techniques.
- E. Deploy microservice to multiple datacenters.
Answer: BC
NEW QUESTION 14
A developer has created an application based on customer requirements. The customer needs to run the application with the minimum downtime. Which design approach regarding high-availability applications, Recovery Time Objective, and Recovery Point Objective must be taken?
- A. Active/passive results in lower RTO and RP
- B. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
- C. Active/passive results in lower RTO and RP
- D. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
- E. Active/active results in lower RTO and RP
- F. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
- G. Active/active results in lower RTO and RP
- H. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
Answer: A
NEW QUESTION 15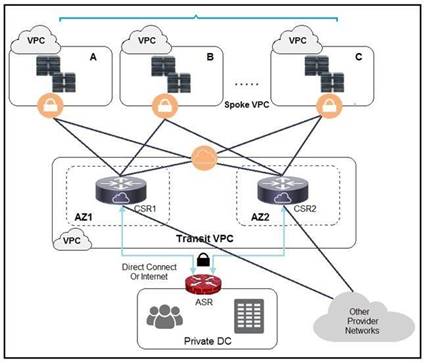
Refer to the exhibit. A company has extended networking from the data center to the cloud through Transit VPC. Which two statements describe the benefits of this approach? (Choose two.)
- A. Dynamic routing combined with multi-AZ- deployment creates a robust network infrastructure.
- B. VPC virtual gateways provide highly available connections to virtual networks.
- C. Dedicated VPC simplifies load balancing by combining internal and external web services.
- D. VPC virtual gateways provide more secure connections to virtual networks.
- E. Dedicated VPC simplifies routing by not combining this service with other shared services.
Answer: BD
NEW QUESTION 16
An organization manages a large cloud-deployed application that employs a microservices architecture. No notable issues occur with downtime because the services of this application are redundantly deployed over three or more data center regions. However, several times a week reports are received about application slowness. The container orchestration logs show faults in a variety of containers that cause them to fail and then spin up brand new.
Which action must be taken to improve the resiliency design of the application while maintaining current scale?
- A. Update the base image of the containers.
- B. Test the execution of the application with another cloud services platform.
- C. Increase the number of containers running per service.
- D. Add consistent “try/catch(exception)” clauses to the code.
Answer: D
NEW QUESTION 17
Where should distributed load balancing occur in a horizontally scalable architecture?
- A. firewall-side/policy load balancing
- B. network-side/central load balancing
- C. service-side/remote load balancing
- D. client-side/local load balancing
Answer: B
NEW QUESTION 18
The UCS Python SDK includes modules for Service Profile template creation. Which two UCS Service Profile template types are supported? (Choose two.)
- A. initial-template
- B. updating-template
- C. abstract-template
- D. attached-template
- E. base-template
Answer: AB
NEW QUESTION 19
A user is receiving a 429 Too Many Requests error. Which scheme is the server employing that causes this error?
- A. rate limiting
- B. time outs
- C. caching
- D. redirection
Answer: A
NEW QUESTION 20
Which snippet presents the correct API call to configure, secure, and enable an SSID using the Meraki API?
- A.

- B.
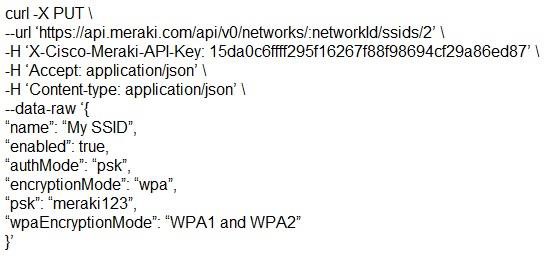
- C.

- D.
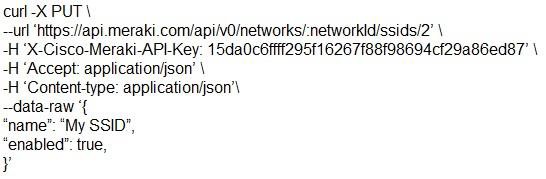
Answer: B
NEW QUESTION 21
......
P.S. Easily pass 350-901 Exam with 0 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy 350-901 Dumps: https://www.2passeasy.com/dumps/350-901/ (0 New Questions)
- What Free 300-075 exam dumps Is?
- The Refresh Guide To 400-101 exam question
- Abreast of the times Cisco 400-101 dumps
- 10 Tips For Improved 300-101 vce
- Most Recent 300-910 Dumps For Implementing DevOps Solutions And Practices Using Cisco Platforms (DEVOPS) Certification
- Down To Date 350-501 Test For Implementing And Operating Cisco Service Provider Network Core Technologies Certification
- Cisco 350-401 Class 2021
- How Many Questions Of 350-201 Practice
- High quality Cisco Additional 650-059 examcollection
- Renew Cisco 300-101 exam


