350-201 Exam Questions - Online Test
350-201 Premium VCE File

150 Lectures, 20 Hours
Cause all that matters here is passing the Cisco 350-201 exam. Cause all that you need is a high score of 350-201 Performing CyberOps Using Core Security Technologies (CBRCOR) exam. The only one thing you need to do is downloading Pass4sure 350-201 exam study guides now. We will not let you down with our money-back guarantee.
Also have 350-201 free dumps questions for you:
NEW QUESTION 1
A security analyst receives an escalation regarding an unidentified connection on the Accounting A1 server within a monitored zone. The analyst pulls the logs and discovers that a Powershell process and a WMI tool process were started on the server after the connection was established and that a PE format file was created in the system directory. What is the next step the analyst should take?
- A. Isolate the server and perform forensic analysis of the file to determine the type and vector of a possible attack
- B. Identify the server owner through the CMDB and contact the owner to determine if these were planned and identifiable activities
- C. Review the server backup and identify server content and data criticality to assess the intrusion risk
- D. Perform behavioral analysis of the processes on an isolated workstation and perform cleaning procedures if the file is malicious
Answer: C
NEW QUESTION 2
Refer to the exhibit.
At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
- A. exploitation
- B. actions on objectives
- C. delivery
- D. reconnaissance
Answer: C
NEW QUESTION 3
The incident response team was notified of detected malware. The team identified the infected hosts, removed the malware, restored the functionality and data of infected systems, and planned a company meeting to improve the incident handling capability. Which step was missed according to the NIST incident handling guide?
- A. Contain the malware
- B. Install IPS software
- C. Determine the escalation path
- D. Perform vulnerability assessment
Answer: D
NEW QUESTION 4
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during the phases on the right.
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 5
A security expert is investigating a breach that resulted in a $32 million loss from customer accounts. Hackers were able to steal API keys and two-factor codes due to a vulnerability that was introduced in a new code a few weeks before the attack. Which step was missed that would have prevented this breach?
- A. use of the Nmap tool to identify the vulnerability when the new code was deployed
- B. implementation of a firewall and intrusion detection system
- C. implementation of an endpoint protection system
- D. use of SecDevOps to detect the vulnerability during development
Answer: D
NEW QUESTION 6
A threat actor used a phishing email to deliver a file with an embedded macro. The file was opened, and a remote code execution attack occurred in a company’s infrastructure. Which steps should an engineer take at the recovery stage?
- A. Determine the systems involved and deploy available patches
- B. Analyze event logs and restrict network access
- C. Review access lists and require users to increase password complexity
- D. Identify the attack vector and update the IDS signature list
Answer: B
NEW QUESTION 7
Drag and drop the telemetry-related considerations from the left onto their cloud service models on the right.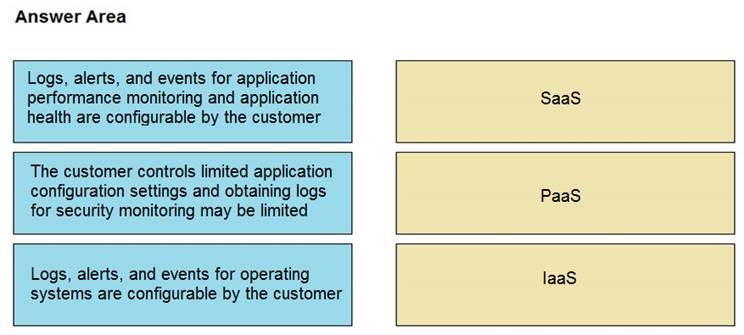
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
Refer to the exhibit.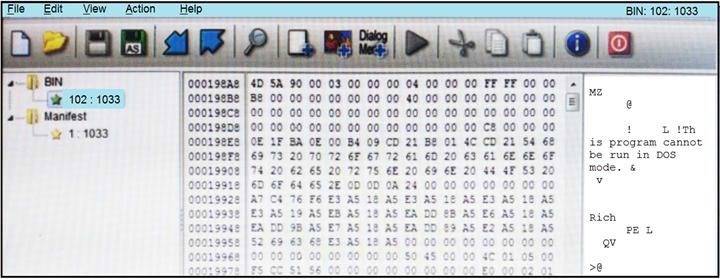
An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?
- A. a DOS MZ executable format
- B. a MS-DOS executable archive
- C. an archived malware
- D. a Windows executable file
Answer: D
NEW QUESTION 9
Refer to the exhibit.
Cisco Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE detects the threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a Quarantine VLAN using Adaptive Network Control policy. Which telemetry feeds were correlated with SMC to identify the malware?
- A. NetFlow and event data
- B. event data and syslog data
- C. SNMP and syslog data
- D. NetFlow and SNMP
Answer: B
NEW QUESTION 10
A security architect is working in a processing center and must implement a DLP solution to detect and prevent any type of copy and paste attempts of sensitive data within unapproved applications and removable devices. Which technical architecture must be used?
- A. DLP for data in motion
- B. DLP for removable data
- C. DLP for data in use
- D. DLP for data at rest
Answer: C
NEW QUESTION 11
Refer to the exhibit.
IDS is producing an increased amount of false positive events about brute force attempts on the organization’s mail server. How should the Snort rule be modified to improve performance?
- A. Block list of internal IPs from the rule
- B. Change the rule content match to case sensitive
- C. Set the rule to track the source IP
- D. Tune the count and seconds threshold of the rule
Answer: B
NEW QUESTION 12
What is the HTTP response code when the REST API information requested by the authenticated user cannot be found?
- A. 401B.-402C.403D.404E.405
Answer: A
NEW QUESTION 13
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services. Which security threat should be mitigated first?
- A. aligning access control policies
- B. exfiltration during data transfer
- C. attack using default accounts
- D. data exposure from backups
Answer: B
NEW QUESTION 14
Refer to the exhibit.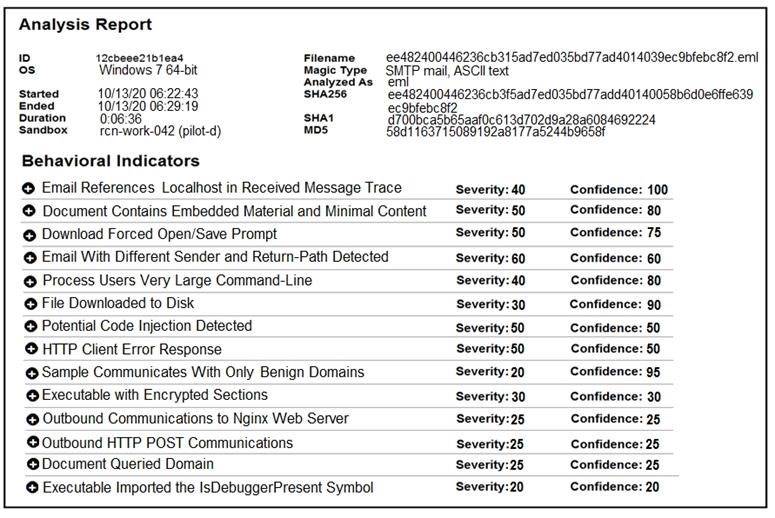
Cisco Advanced Malware Protection installed on an end-user desktop automatically submitted a low prevalence file to the Threat Grid analysis engine. What should be concluded from this report?
- A. Threat scores are high, malicious ransomware has been detected, and files have been modified
- B. Threat scores are low, malicious ransomware has been detected, and files have been modified
- C. Threat scores are high, malicious activity is detected, but files have not been modified
- D. Threat scores are low and no malicious file activity is detected
Answer: B
NEW QUESTION 15
Refer to the exhibit.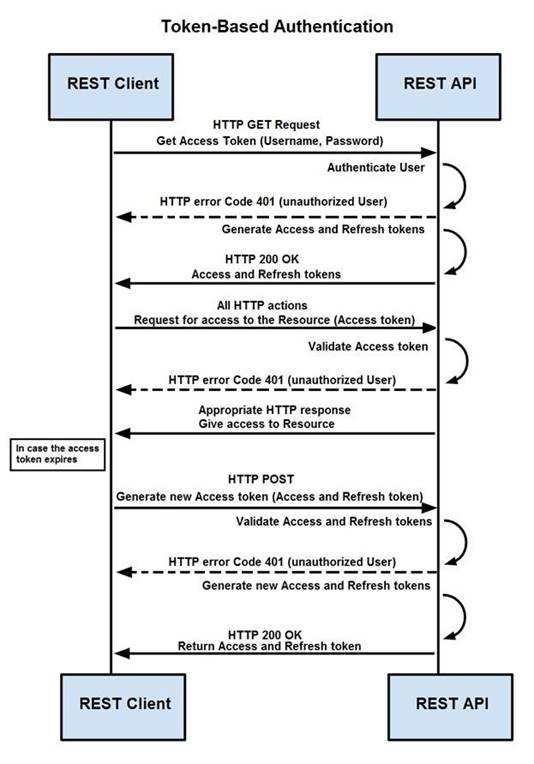
How are tokens authenticated when the REST API on a device is accessed from a REST API client?
- A. The token is obtained by providing a passwor
- B. The REST client requests access to a resource using the access toke
- C. The REST API validates the access token and gives access to the resource.
- D. The token is obtained by providing a passwor
- E. The REST API requests access to a resource using the access token, validates the access token, and gives access to the resource.
- F. The token is obtained before providing a passwor
- G. The REST API provides resource access, refreshes tokens, and returns them to the REST clien
- H. The REST client requests access to a resource using theaccess token.
- I. The token is obtained before providing a passwor
- J. The REST client provides access to a resource using the access toke
- K. The REST API encrypts the access token and gives access to the resource.
Answer: D
NEW QUESTION 16
Refer to the exhibit.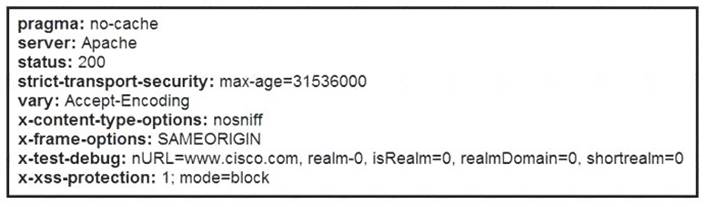
Where does it signify that a page will be stopped from loading when a scripting attack is detected?
- A. x-frame-options
- B. x-content-type-options
- C. x-xss-protection
- D. x-test-debug
Answer: C
NEW QUESTION 17
What is a limitation of cyber security risk insurance?
- A. It does not cover the costs to restore stolen identities as a result of a cyber attack
- B. It does not cover the costs to hire forensics experts to analyze the cyber attack
- C. It does not cover the costs of damage done by third parties as a result of a cyber attack
- D. It does not cover the costs to hire a public relations company to help deal with a cyber attack
Answer: A
NEW QUESTION 18
An organization is using a PKI management server and a SOAR platform to manage the certificate lifecycle. The SOAR platform queries a certificate management tool to check all endpoints for SSL certificates that have either expired or are nearing expiration. Engineers are struggling to manage problematic certificates outside of PKI management since deploying certificates and tracking them requires searching server owners manually. Which action will improve workflow automation?
- A. Implement a new workflow within SOAR to create tickets in the incident response system, assign problematic certificate update requests to server owners, and register change requests.
- B. Integrate a PKI solution within SOAR to create certificates within the SOAR engines to track, update, and monitor problematic certificates.
- C. Implement a new workflow for SOAR to fetch a report of assets that are outside of the PKI zone, sort assets by certification management leads and automate alerts that updates are needed.
- D. Integrate a SOAR solution with Active Directory to pull server owner details from the AD and send an automated email for problematic certificates requesting updates.
Answer: C
NEW QUESTION 19
A malware outbreak is detected by the SIEM and is confirmed as a true positive. The incident response team follows the playbook to mitigate the threat. What is the first action for the incident response team?
- A. Assess the network for unexpected behavior
- B. Isolate critical hosts from the network
- C. Patch detected vulnerabilities from critical hosts
- D. Perform analysis based on the established risk factors
Answer: B
NEW QUESTION 20
Refer to the exhibit.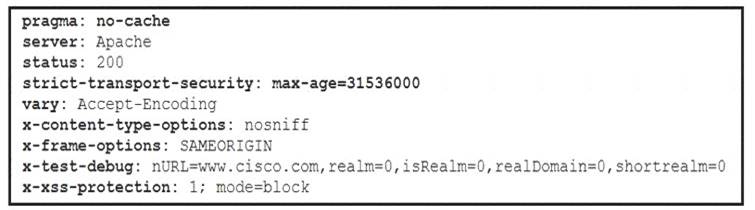
Where are the browser page rendering permissions displayed?
- A. x-frame-options
- B. x-xss-protection
- C. x-content-type-options
- D. x-test-debug
Answer: C
NEW QUESTION 21
......
P.S. Easily pass 350-201 Exam with 139 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy 350-201 Dumps: https://www.2passeasy.com/dumps/350-201/ (139 New Questions)
- 100% Guarantee 300-420 Faq 2021
- A Review Of Guaranteed 300-075 exam
- Renew Cisco 300-320 pdf
- Cisco 300-170 Questions 2021
- All About Breathing 642-035 braindumps
- Guaranteed CCNP Collaboration 300-070 pdf
- A Review Of Pinpoint 300-075 exam dumps
- Avant-garde 300-625 Practice For Implementing Cisco Storage Area Networking (DCSAN) Certification
- Latest 300-465 Training Materials 2021
- Downloadable 400-151 Dumps 2021


