PCNSA Exam Questions - Online Test
PCNSA Premium VCE File

150 Lectures, 20 Hours
Your success in Paloalto-Networks PCNSA is our sole target and we develop all our PCNSA braindumps in a way that facilitates the attainment of this target. Not only is our PCNSA study material the best you can find, it is also the most detailed and the most updated. PCNSA Practice Exams for Paloalto-Networks PCNSA are written to the highest standards of technical accuracy.
Free demo questions for Paloalto-Networks PCNSA Exam Dumps Below:
NEW QUESTION 1
DRAG DROP
Match the Palo Alto Networks Security Operating Platform architecture to its description.
Select and Place: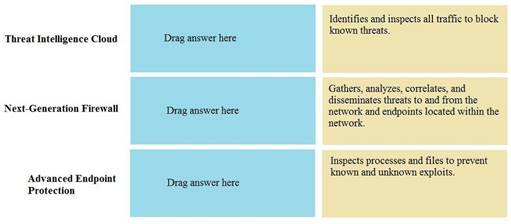
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 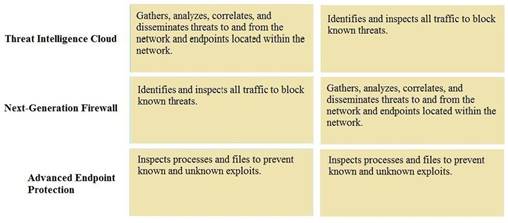
NEW QUESTION 2
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?
- A. branch office traffic
- B. north-south traffic
- C. perimeter traffic
- D. east-west traffic
Answer: D
NEW QUESTION 3
What are two differences between an implicit dependency and an explicit dependency in App- ID? (Choose two.)
- A. An implicit dependency does not require the dependent application to be added in the security policy
- B. An implicit dependency requires the dependent application to be added in the security policy
- C. An explicit dependency does not require the dependent application to be added in the security policy
- D. An explicit dependency requires the dependent application to be added in the security policy
Answer: AD
NEW QUESTION 4
Recently changes were made to the firewall to optimize the policies and the security team wants to see if those changes are helping. What is the quickest way to reset the hit counter to zero in all the security policy rules?
- A. At the CLI enter the command reset rules and press Enter
- B. Highlight a rule and use the Reset Rule Hit Counter > Selected Rules for each rule
- C. Reboot the firewall
- D. Use the Reset Rule Hit Counter > All Rules option
Answer: D
NEW QUESTION 5
Which statement is true regarding a Best Practice Assessment?
- A. The BPA tool can be run only on firewalls
- B. It provides a percentage of adoption for each assessment data
- C. The assessment, guided by an experienced sales engineer, helps determine the areas of greatest risk where you should focus prevention activities
- D. It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture
Answer: B
NEW QUESTION 6
Which interface type is used to monitor traffic and cannot be used to perform traffic shaping?
- A. Layer 2
- B. Tap
- C. Layer 3
- D. Virtual Wire
Answer: B
NEW QUESTION 7
Which two App-ID applications will need to be allowed to use Facebook- chat? (Choose two.)
- A. facebook
- B. facebook-chat
- C. facebook-base
- D. facebook-email
Answer: BC
NEW QUESTION 8
Which two Palo Alto Networks security management tools provide a consolidated creation of policies, centralized management and centralized threat intelligence. (Choose two.)
- A. GlobalProtect
- B. Panorama
- C. Aperture
- D. AutoFocus
Answer: BD
NEW QUESTION 9
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?
- A. Translation Type
- B. Interface
- C. Address Type
- D. IP Address
Answer: A
NEW QUESTION 10
What are three differences between security policies and security profiles? (Choose three.)
- A. Security policies are attached to security profiles
- B. Security profiles are attached to security policies
- C. Security profiles should only be used on allowed traffic
- D. Security profiles are used to block traffic by themselves
- E. Security policies can block or allow traffic
Answer: BCE
NEW QUESTION 11
A security administrator has configured App-ID updates to be automatically downloaded and installed. The company is currently using an application identified by App-ID as SuperApp_base. On a content update notice, Palo Alto Networks is adding new app signatures labeled SuperApp_chat and SuperApp_download, which will be deployed in 30 days. Based on the information, how is the SuperApp traffic affected after the 30 days have passed?
- A. All traffic matching the SuperApp_chat, and SuperApp_download is denied because it no longer matches the SuperApp-base application
- B. No impact because the apps were automatically downloaded and installed
- C. No impact because the firewall automatically adds the rules to the App-ID interface
- D. All traffic matching the SuperApp_base, SuperApp_chat, and SuperApp_download is denied until the security administrator approves the applications
Answer: C
NEW QUESTION 12
An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact a command-and-control (C2) server. Which two security profile components will detect and prevent this threat after the firewall’s signature database has been updated? (Choose two.)
- A. vulnerability protection profile applied to outbound security policies
- B. anti-spyware profile applied to outbound security policies
- C. antivirus profile applied to outbound security policies
- D. URL filtering profile applied to outbound security policies
Answer: BD
NEW QUESTION 13
Which interface does not require a MAC or IP address?
- A. Virtual Wire
- B. Layer3
- C. Layer2
- D. Loopback
Answer: A
NEW QUESTION 14
Which user mapping method could be used to discover user IDs in an environment with multiple Windows domain controllers?
- A. Active Directory monitoring
- B. Windows session monitoring
- C. Windows client probing
- D. domain controller monitoring
Answer: A
NEW QUESTION 15
Which file is used to save the running configuration with a Palo Alto Networks firewall?
- A. running-config.xml
- B. run-config.xml
- C. running-configuration.xml
- D. run-configuratin.xml
Answer: A
NEW QUESTION 16
......
P.S. Allfreedumps.com now are offering 100% pass ensure PCNSA dumps! All PCNSA exam questions have been updated with correct answers: https://www.allfreedumps.com/PCNSA-dumps.html (115 New Questions)


