NSE8 Exam Questions - Online Test
NSE8 Premium VCE File

150 Lectures, 20 Hours
It is impossible to pass Fortinet NSE8 exam without any help in the short term. Come to us soon and find the most advanced, correct and guaranteed . You will get a surprising result by our .
Free NSE8 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
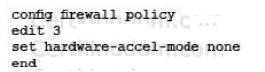
Your NOC contracts the security team due to a problem with a new application flow. You are instructed to disable hardware acceleration for the policy shown in the exhibit for troubleshooting purposes.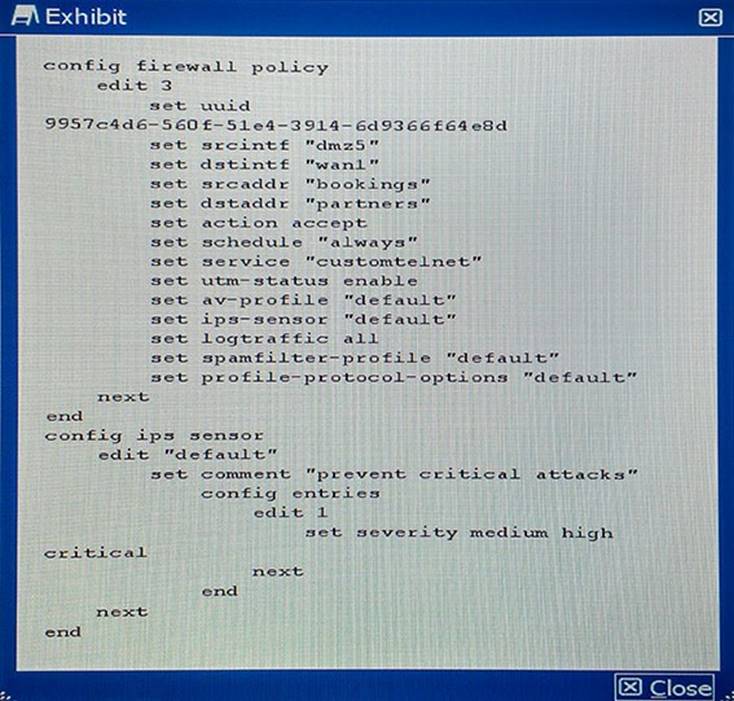
Which command will disable hardware acceleration for the new application policy?
- A.
- B.

- C.

- D.

Answer: D
Explanation: References:
http://docs.fortinet.com/uploaded/files/1607/fortigate-hardware-accel-50.pdf
NEW QUESTION 2
You have replaced an explicit proxy Web filter with a FortiGate. The human resources department requires that all URLs be logged. Users are reporting that their browsers are now indicating certificate errors as shown in the exhibit.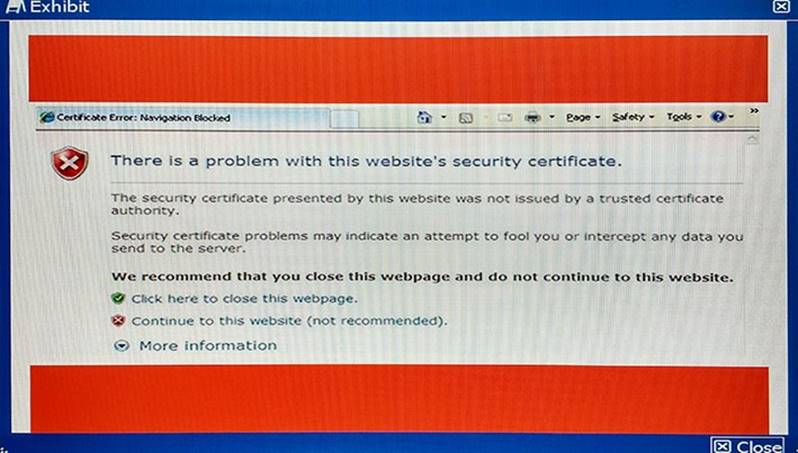
Which step is a valid solution to the problem?
- A. Make sure that the affected users’ browsers are no longer set to use the explicit proxy.
- B. Import the FortiGate’s SSL CA certificate into the Web browsers.
- C. Change the Web filter policies on the FortiGate to only do certificate inspection.
- D. Make a Group Policy to install the FortiGate’s SSL certificate as a trusted host certificate on the Web browser.
Answer: D
Explanation: For https traffic inspection, client machine should install fortigate’s ssl certificate
NEW QUESTION 3
A customer just bought an additional FortiGate device and plans to use their existing load balancer to distribute traffic across two FortiGate units participating on a BGP network serving different neighbors. The customer has mixed traffic of IPv4 and IPv6 TCP, UDP, and ICMP. The two FortiGate devices shown in the exhibit should be redundant to each other so that the NAT session and active session tables will synchronize and fail over to the unit that is still operating without any loss of data if one of the units fail.
Which high availability solution would you implement?
- A. FortiGate Cluster Protocol (FGCP)
- B. Fortinet redundant UTM protocol (FRUP)
- C. FortiGate Session Life Support Protocol (FGSP)
- D. Virtual Router Redundancy Protocol (VRRP)
Answer: A
Explanation: References:
http://docs.fortinet.com/uploaded/files/1074/fortigate-ha-40-mr2.pdf
NEW QUESTION 4
FortiGate1 has a gateway-to-gateway IPsec VPN to FortiGate2. The entire IKE negotiation between FortiGate1 and FortiGate2 is on UDP port 500. A PC on FortuGate2’s local area network is sending continuous ping requests over the VPN tunnel to a PC of FortiGate1’s local area network. No other traffic is sent over the tunnel.
Which statement is true on this scenario?
- A. FortiGate1 sends an R-U-THERE packet every 300 seconds while ping traffic is flowing.
- B. FortiGate1 sends an R-U-THERE packet if pings stop for 300 seconds and no IKE packet is received during this period.
- C. FortiGate1 sends an R-U-THERE packet if pings stop for 60 seconds and no IKE packet is received during this period.
- D. FortiGate1 sends an R-U-THERE packet every 60 seconds while ping traffic is flowing.
Answer: C
Explanation: References: http://kb.fortinet.com/kb/documentLink.do?externalID=FD35337
NEW QUESTION 5
Referring to the command output shown in the exhibit, how many hosts are connected to the FortiGate?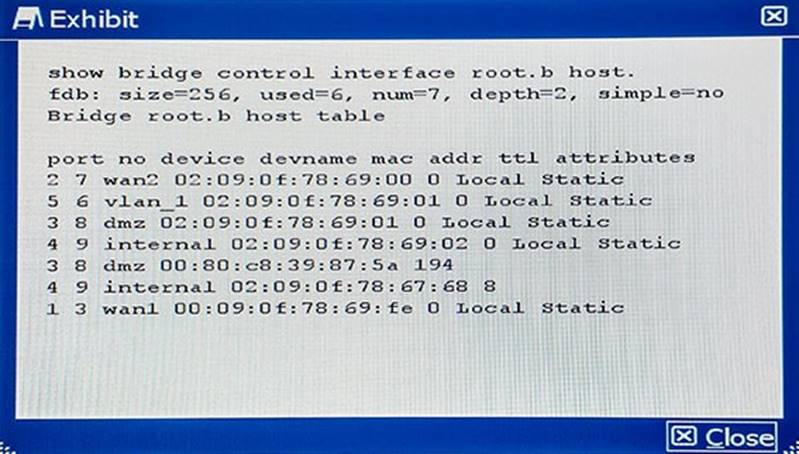
- A. 7
- B. 6
- C. 2
- D. 256
Answer: B
Explanation: References:
http://cookbook.fortinet.com/troubleshooting-fortigate-installation/
NEW QUESTION 6
You must establish a BGP peering with a service provider. The provider has supplied you with BGP peering parameters and you performed the basic configuration shown in the exhibit on your FortiGate unit. You notice that your peering session is not coming up.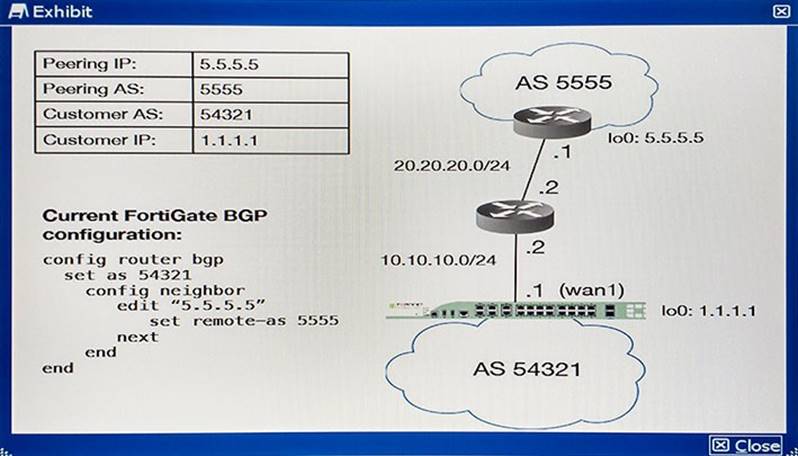
Which three missing configuration statements are needed to make this configuration functional? (Choose three.)
- A.
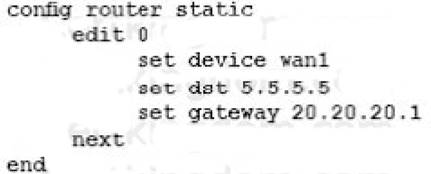
- B.

- C.

- D.
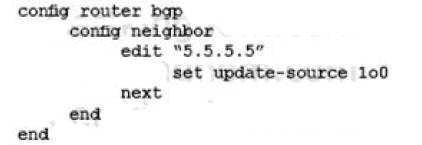
- E.

Answer: CDE
NEW QUESTION 7
You are asked to design a secure solution using Fortinet products for a company. The company recently has Web servers that were exploited and defaced. The customer has also experienced Denial or Service due to SYN Flood attacks. Taking this into consideration, the customer’s solution should have the following requirements:
- management requires network-based content filtering with man-in-the-middle inspection
- the customer has no existing public key infrastructure but requires centralized certificate management
- users are tracked by their active directory username without installing any software on their hosts
- Web servers that have been exploited need to be protected from the OWASP Top 10
- notification of high volume SYN Flood attacks when a threshold has been triggered Which three solutions satisfy these requirements? (Choose three.)
- A. FortiGate
- B. FortiClient
- C. FortiWeb
- D. FortiAuthenticator
- E. FortiDDOS
Answer: ACE
NEW QUESTION 8
You notice that memory usage is high and FortiGate has entered conserve mode. You want FortiGate’s IPS engine to focus only on exploits and attacks that are applicable to your specific network.
Which two steps would you take to reduce RAM usage without weakening security? (Choose two.)
- A. Configure IPS to pass files that are larger than a specific threshold, instead of buffering and scanning them.
- B. Reduce the size of the signature three (filters) that FortiGate must search by disabling scans for applications and OS stacks that do not exist on your network.
- C. Disable application control for protocols that are not used on your network.
- D. Disable IPS for traffic destined for the FortiGate itself.
Answer: BD
NEW QUESTION 9
The SECOPS team in your company has started a new project to store all logging data in a disaster recovery center. All FortiGates will log to a secondary FortiAnalyzer and establish a TCP session to send logs to the syslog server.
Which two configurations will achieve this goal? (Choose two.)
- A.
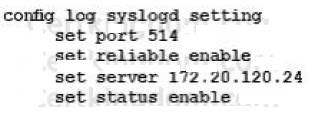
- B.
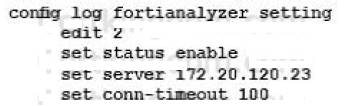
- C.
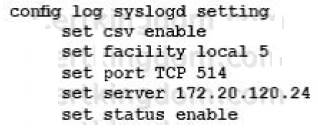
- D.

Answer: AC
Explanation: https://forum.fortinet.com/tm.aspx?m=122848
NEW QUESTION 10
A café offers free Wi-Fi. Customers’ portable electronic devices often do not have antivirus software installed and may be hosting worms without their knowledge. You must protect all customers from any other customers’ infected devices that join the same SSID.
Which step meets the requirement?
- A. Enable deep SSH inspection with antivirus and IPS.
- B. Use a captive portal to redirect unsecured connections such as HTTP and SMTP to their secured equivalents, preventing worms on infected clients from tampering with other customer traffic.
- C. Use WPA2 encryption and configure a policy on FortiGate to block all traffic between clients.
- D. Use WPA2 encryption, and enable “Block Intra-SSID Traffic”.
Answer: B
NEW QUESTION 11
Your marketing department uncompressed and executed a file that the whole department received using Skype.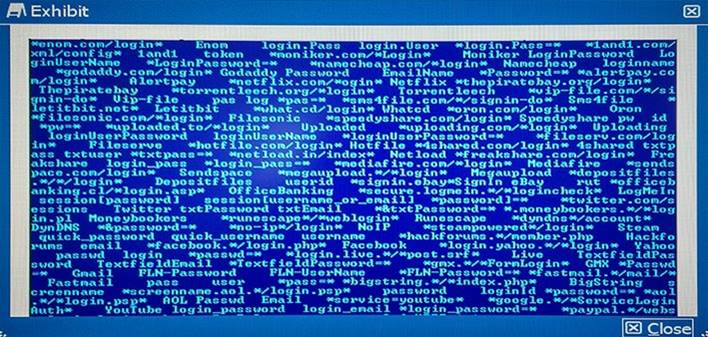
Reviewing the exhibit, which two details do you determine from your initial analysis of the payload?
- A. The payload contains strings that the malware is monitoring to harvest credentials.
- B. This is a type of Trojan that will download and pirate movies using your Netflix credentials.
- C. This type of threat of a DDoS attack using instant messaging to send e-mails to further spread the infection.
- D. This threat payload is uploading private user videos which are then used to extort Bitcoin payments.
Answer: B
NEW QUESTION 12
A customer wants to install a FortiSandbox device to identify suspicious files received by an e-mail server. All the incoming e-mail traffic to the e-mail server uses the SMTPS protocol.
Which three solutions would be implemented? (Choose three.)
- A. FortiGate device in transparent mode sending the suspicious files to the FortiSandbox
- B. FortiSandbox in sniffer input mode
- C. FortiMail device in gateway mode using the built-in MTA and sending the suspicious files to the FortiSandbox
- D. FortiMail device in transparent mode acting as an SMTP proxy sending the suspicious files to the FortiSandbox
- E. FortiGate device in NAT mode sending the suspicious files to the FortiSandbox
Answer: BCE
Explanation: References: http://kb.fortinet.com/kb/documentLink.do?externalID=FD34371
NEW QUESTION 13
The exhibit shows an LDAP server configuration in a FortiGate device.
The LDAP user, John Smith, has the following LDAP attributes: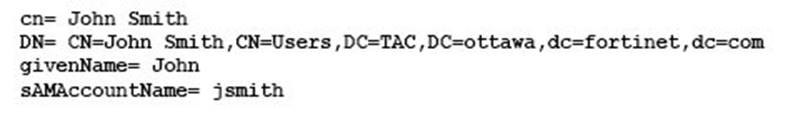
John Smith’s LDAP password is ABC123.
Which CLI command should you use to test the LDAP authentication using John Smith’s credentials?
- A. diagnose test authserver ldap Lab jsmith ABC123
- B. diagnose test authserver ldap-direct Lab jsmith ABC123
- C. diagnose test authserver ldap Lab ‘John Smith’ ABC123
- D. diagnose test authserver ldap-direct Lab john ABC123
Answer: A
Explanation: References: https://forum.fortinet.com/tm.aspx?m=119178
NEW QUESTION 14
Which three configuration scenarios will result in an IPsec negotiation failure between two FortiGate devices? (Choose three.)
- A. mismatched phase 2 selectors
- B. mismatched Anti-Replay configuration
- C. mismatched Perfect Forward Secrecy
- D. failed Dead Peer Detection negotiation
- E. mismatched IKE version
Answer: ACE
Explanation: In IPsec negotiations, Perfect Forward Secrecy (PFS) ensures that each new cryptographic key is unrelated to any previous key. Either enable or disable PFS on both the tunnel peers; otherwise, the LAN-to-LAN (L2L) IPsec tunnel is not established
NEW QUESTION 15
A customer wants to implement a RADIUS Single Sign On (RSSO) solution for multiple FortiGate devices. The customer’s network already includes a RADIUS server that can generate the logon and logoff accounting records. However, the RADIUS server can send those records to only one destination.
What should the customer do to overcome this limitation?
- A. Send the RADIUS records to an LDAP server and add the LDAP server to the FortiGate configuration.
- B. Send the RADIUS records to an RSSO Collector Agent.
- C. Send the RADIUS records to one of the FortiGate devices, which can replicate them to the other FortiGate units.
- D. Use the RADIUS accounting proxy feature available in FortiAuthenticator devices.
Answer: B
Explanation: References:
http://docs.fortinet.com/uploaded/files/1937/fortigate-authentication-52.pdf
NEW QUESTION 16
An administrator wants to assign static IP addresses to users connecting tunnel-mode SSL VPN. Each SSL VPN user must always get the same unique IP address which is never assigned to any other user.
Which solution accomplishes this task?
- A. TACACS+ authentication with an attribute-value (AV) pair containing each user’s IP address.
- B. RADIUS authentication with each user’s IP address stored in a Vendor Specific Attribute (VSA).
- C. LDAP authentication with an LDAP attribute containing each user’s IP address.
- D. FSSO authentication with an LDAP attribute containing each user’s IP address.
Answer: D
NEW QUESTION 17
Which command detects where a routing path is broken?
- A. exec traceroute <destination>
- B. exec route ping <destination>
- C. diag route null
- D. diag debug route <destination>
Answer: A
Recommend!! Get the Full NSE8 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/NSE8/ (New 65 Q&As Version)
- Latest Fortinet NSE 5 - FortiClient EMS 7.0 NSE5_FCT-7.0 Pdf
- How Many Questions Of FortiADC Brain Dumps
- Avant-garde NSE4 Class 2021
- Precise NSE4_FGT-6.0 Testing Bible 2021
- How Many Questions Of NSE5_FMG-6.4 Test
- Most Recent NSE4_FGT-6.2 Lab 2021
- The Secret Of Fortinet NSE5_FMG-6.0 Exam
- Validated Fortinet NSE4-5.4 exam question
- A Review Of Highest Quality NSE7_OTS-6.4 Brain Dumps
- Update Fortinet Network Security Expert 8 Written Exam (810) NSE8_810 Pdf Exam


