NSE4_FGT-7.0 Exam Questions - Online Test
NSE4_FGT-7.0 Premium VCE File

150 Lectures, 20 Hours
It is impossible to pass Fortinet NSE4_FGT-7.0 exam without any help in the short term. Come to Passleader soon and find the most advanced, correct and guaranteed Fortinet NSE4_FGT-7.0 practice questions. You will get a surprising result by our Down to date Fortinet NSE 4 - FortiOS 7.0 practice guides.
Free demo questions for Fortinet NSE4_FGT-7.0 Exam Dumps Below:
NEW QUESTION 1
Which two types of traffic are managed only by the management VDOM? (Choose two.)
- A. FortiGuard web filter queries
- B. PKI
- C. Traffic shaping
- D. DNS
Answer: AD
NEW QUESTION 2
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
- A. The subject field in the server certificate
- B. The serial number in the server certificate
- C. The server name indication (SNI) extension in the client hello message
- D. The subject alternative name (SAN) field in the server certificate
- E. The host field in the HTTP header
Answer: ACD
Explanation:
Reference: https://checkthefirewall.com/blogs/fortinet/ssl-inspection
NEW QUESTION 3
Which statement about the policy ID number of a firewall policy is true?
- A. It is required to modify a firewall policy using the CLI.
- B. It represents the number of objects used in the firewall policy.
- C. It changes when firewall policies are reordered.
- D. It defines the order in which rules are processed.
Answer: A
NEW QUESTION 4
Which two statements are true about collector agent standard access mode? (Choose two.)
- A. Standard mode uses Windows convention-NetBios: Domain\Username.
- B. Standard mode security profiles apply to organizational units (OU).
- C. Standard mode security profiles apply to user groups.
- D. Standard access mode supports nested groups.
Answer: AC
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.0.0/handbook/482937/agent-based-fsso
NEW QUESTION 5
A FortiGate is operating in NAT mode and configured with two virtual LAN (VLAN) sub interfaces added to the physical interface.
Which statements about the VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in different subnets.
- A. The two VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in different subnets.
- B. The two VLAN sub interfaces must have different VLAN IDs.
- C. The two VLAN sub interfaces can have the same VLAN ID, only if they belong to different VDOMs.
- D. The two VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in the same subnet.
Answer: B
Explanation:
FortiGate_Infrastructure_6.0_Study_Guide_v2-Online.pdf –> page 147
“Multiple VLANs can coexist in the same physical interface, provide they have different VLAN ID”
NEW QUESTION 6
Refer to the exhibits to view the firewall policy (Exhibit A) and the antivirus profile (Exhibit B).
Which statement is correct if a user is unable to receive a block replacement message when downloading an infected file for the first time?
- A. The firewall policy performs the full content inspection on the file.
- B. The flow-based inspection is used, which resets the last packet to the user.
- C. The volume of traffic being inspected is too high for this model of FortiGate.
- D. The intrusion prevention security profile needs to be enabled when using flow-based inspection mode.
Answer: B
Explanation:
• "ONLY" If the virus is detected at the "START" of the connection, the IPS engine sends the block replacement message immediately
• When a virus is detected on a TCP session (FIRST TIME), but where "SOME PACKETS" have been already forwarded to the receiver, FortiGate "resets the connection" and does not send the last piece of the file. Although the receiver got most of the file content, the file has been truncated and therefore, can’t be opened. The IPS engine also caches the URL of the infected file, so that if a "SECOND ATTEMPT" to transmit the file is made, the IPS engine will then send a block replacement message to the client instead of scanning the file again.
In flow mode, the FortiGate drops the last packet killing the file. But because of that the block replacement message cannot be displayed. If the file is attempted to download again the block message will be shown.
NEW QUESTION 7
Refer to the exhibit.
According to the certificate values shown in the exhibit, which type of entity was the certificate issued to?
- A. A user
- B. A root CA
- C. A bridge CA
- D. A subordinate
Answer: A
NEW QUESTION 8
An administrator wants to configure timeouts for users. Regardless of the user€™s behavior, the timer should start as soon as the user authenticates and expire after the configured value.
Which timeout option should be configured on FortiGate?
- A. auth-on-demand
- B. soft-timeout
- C. idle-timeout
- D. new-session
- E. hard-timeout
Answer: E
Explanation:
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD37221#:~:text=Hard%20timeout%3A%20User%20
NEW QUESTION 9
What devices form the core of the security fabric?
- A. Two FortiGate devices and one FortiManager device
- B. One FortiGate device and one FortiManager device
- C. Two FortiGate devices and one FortiAnalyzer device
- D. One FortiGate device and one FortiAnalyzer device
Answer: C
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/425100/components
NEW QUESTION 10
Refer to the exhibit to view the application control profile.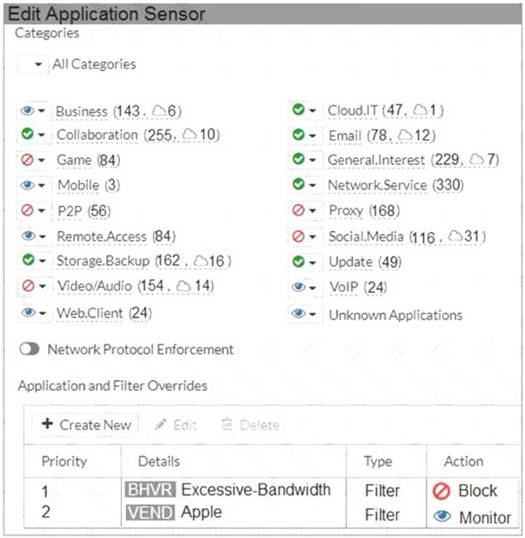
Users who use Apple FaceTime video conferences are unable to set up meetings. In this scenario, which statement is true?
- A. Apple FaceTime belongs to the custom monitored filter.
- B. The category of Apple FaceTime is being monitored.
- C. Apple FaceTime belongs to the custom blocked filter.
- D. The category of Apple FaceTime is being blocked.
Answer: C
NEW QUESTION 11
Refer to the exhibit.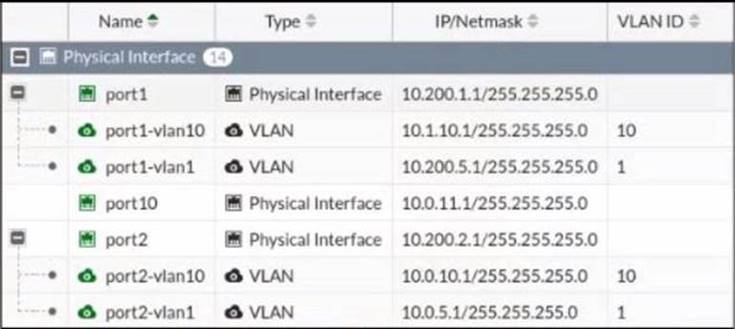
Given the interfaces shown in the exhibit. which two statements are true? (Choose two.)
- A. Traffic between port2 and port2-vlan1 is allowed by default.
- B. port1-vlan10 and port2-vlan10 are part of the same broadcast domain.
- C. port1 is a native VLAN.
- D. port1-vlan and port2-vlan1 can be assigned in the same VDOM or to different VDOMs.
Answer: CD
Explanation:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-rules-about-VLAN-configuration-and-VDOM-interf https://kb.fortinet.com/kb/viewContent.do?externalId=FD30883
NEW QUESTION 12
Which two actions can you perform only from the root FortiGate in a Security Fabric? (Choose two.)
- A. Shut down/reboot a downstream FortiGate device.
- B. Disable FortiAnalyzer logging for a downstream FortiGate device.
- C. Log in to a downstream FortiSwitch device.
- D. Ban or unban compromised hosts.
Answer: AB
NEW QUESTION 13
FortiGate is configured as a policy-based next-generation firewall (NGFW) and is applying web filtering and application control directly on the security policy.
Which two other security profiles can you apply to the security policy? (Choose two.)
- A. Antivirus scanning
- B. File filter
- C. DNS filter
- D. Intrusion prevention
Answer: AD
NEW QUESTION 14
If Internet Service is already selected as Destination in a firewall policy, which other configuration objects can be selected to the Destination field of a firewall policy?
A User or User Group
- A. IP address
- B. No other object can be added
- C. FQDN address
Answer: B
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.2.5/cookbook/179236/using-internet-service-in-policy
NEW QUESTION 15
Which three statements about security associations (SA) in IPsec are correct? (Choose three.)
- A. Phase 2 SAs are used for encrypting and decrypting the data exchanged through the tunnel.
- B. An SA never expires.
- C. A phase 1 SA is bidirectional, while a phase 2 SA is directional.
- D. Phase 2 SA expiration can be time-based, volume-based, or both.
- E. Both the phase 1 SA and phase 2 SA are bidirectional.
Answer: ACD
NEW QUESTION 16
Refer to the exhibit.


The exhibit contains a network diagram, firewall policies, and a firewall address object configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-user2. Remote-user2 is still able to access Webserver.
Which two changes can the administrator make to deny Webserver access for Remote-User2? (Choose two.)
- A. Disable match-vip in the Deny policy.
- B. Set the Destination address as Deny_IP in the Allow-access policy.
- C. Enable match vip in the Deny policy.
- D. Set the Destination address as Web_server in the Deny policy.
Answer: CD
NEW QUESTION 17
......
Thanks for reading the newest NSE4_FGT-7.0 exam dumps! We recommend you to try the PREMIUM Dumps-files.com NSE4_FGT-7.0 dumps in VCE and PDF here: https://www.dumps-files.com/files/NSE4_FGT-7.0/ (172 Q&As Dumps)
- The Secret Of Fortinet NSE5_FAZ-6.4 Training
- The Secret Of Fortinet NSE5_FAZ-6.2 Answers
- Latest Fortinet NSE 5 - FortiClient EMS 7.0 NSE5_FCT-7.0 Pdf
- What Top Quality NSE6_FML-6.2 Questions Pool Is
- how many questions of NSE4-5.4 pdf?
- How Many Questions Of NSE4_FGT-6.4 Training
- Top Tips Of Most Up-to-date NSE7_LED-7.0 Latest Exam
- The Secret Of Fortinet NSE5_FMG-6.0 Exam
- Most Up-to-date NSE4_FGT-7.0 Practice Question For Fortinet NSE 4 - FortiOS 7.0 Certification
- Most Recent NSE4_FGT-6.2 Lab 2021


