MS-500 Exam Questions - Online Test
MS-500 Premium VCE File

150 Lectures, 20 Hours
Master the MS-500 Microsoft 365 Security Administrator content and be ready for exam day success quickly with this Exambible MS-500 free draindumps. We guarantee it!We make it a reality and give you real MS-500 questions in our Microsoft MS-500 braindumps.Latest 100% VALID Microsoft MS-500 Exam Questions Dumps at below page. You can use our Microsoft MS-500 braindumps and pass your exam.
Microsoft MS-500 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Note: This question is part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that is associated to a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You use Active Directory Federation Services (AD FS) to federate on-premises Active Directory and the tenant. Azure AD Connect has the following settings:
•Source Anchor: objectGUID
•Password Hash Synchronization: Disabled
•Password writeback: Disabled
•Directory extension attribute sync: Disabled
•Azure AD app and attribute filtering: Disabled
•Exchange hybrid deployment: Disabled
•User writeback: Disabled
You need to ensure that you can use leaked credentials detection in Azure AD Identity Protection. Solution: You modify the Azure AD app and attribute filtering settings.
Does that meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 2
You have a Microsoft 365 subscription.
All computers run Windows 10 Enterprise and are managed by using Microsoft Intune. You plan to view only security-related Windows telemetry data.
You need to ensure that only Windows security data is sent to Microsoft. What should you create from the Intune admin center?
- A. a device configuration profile that has device restrictions configured
- B. a device configuration profile that has the Endpoint Protection settings configured
- C. a device configuration policy that has the System Security settings configured
- D. a device compliance policy that has the Device Health settings configured
Answer: A
Explanation:
Reference:
https://docs.microsoft.com/en-us/intune/device-restrictions-windows-10#reporting-and-telemetry
NEW QUESTION 3
HOTSPOT
You are evaluating which devices are compliant in Intune.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 4
HOTSPOT
You have a Microsoft 365 subscription. Auditing is enabled.
A user named User1 is a member of a dynamic security group named Group1. You discover that User1 is no longer a member of Group1.
You need to search the audit log to identify why User1 was removed from Group1.
Which two actions should you use in the search? To answer, select the appropriate activities in the answer area.
NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/search-the-audit-log-in-security-and-compliance
NEW QUESTION 5
You have a Microsoft 365 subscription.
You create an Advanced Threat Protection (ATP) safe attachments policy.
You need to configure the retention duration for the attachments in quarantine. Which type of threat management policy should you create?
- A. Anti-malware
- B. DKIM
- C. Anti-spam
- D. ATP anti-phishing
Answer: A
NEW QUESTION 6
Note: This question is part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that is associated to a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You use Active Directory Federation Services (AD FS) to federate on-premises Active Directory and the tenant. Azure AD Connect has the following settings:
•Source Anchor: objectGUID
•Password Hash Synchronization: Disabled
•Password writeback: Disabled
•Directory extension attribute sync: Disabled
•Azure AD app and attribute filtering: Disabled
•Exchange hybrid deployment: Disabled
•User writeback: Disabled
You need to ensure that you can use leaked credentials detection in Azure AD Identity Protection.
Solution: You modify the Source Anchor settings.
Does that meet the goal?
- A. Yes
- B. No
Answer: B
NEW QUESTION 7
Your network contains an on-premises Active Directory domain. The domain contains servers that
run Windows Server and have advanced auditing enabled.
The security logs of the servers are collected by using a third-party SIEM solution.
You purchase a Microsoft 365 subscription and plan to deploy Azure Advanced Threat Protection (ATP) by using standalone sensors.
You need to ensure that you can detect when sensitive groups are modified and when malicious services are created.
What should you do?
- A. Configure Event Forwarding on the domain controllers
- B. Configure auditing in the Office 365 Security & Compliance center.
- C. Turn on Delayed updates for the Azure ATP sensors.
- D. Enable the Audit account management Group Policy setting for the servers.
Answer: A
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure-advanced-threat-protection/configure-event-forwarding
NEW QUESTION 8
HOTSPOT
You need to recommend an email malware solution that meets the security requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.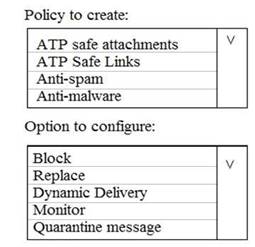
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 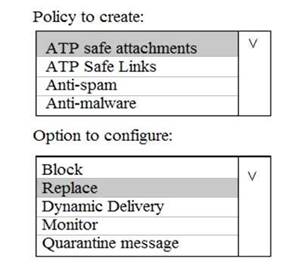
NEW QUESTION 9
You have a Microsoft 365 subscription.
You create and run a content search from the Security & Compliance admin center. You need to download the results of the content search.
What should you obtain first?
- A. an export key
- B. a password
- C. a certificate
- D. a pin
Answer: A
Explanation:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/export-search-results
NEW QUESTION 10
You have a Microsoft 365 subscription that uses a default domain name of fabrikam.com. You create a safe links policy, as shown in the following exhibit.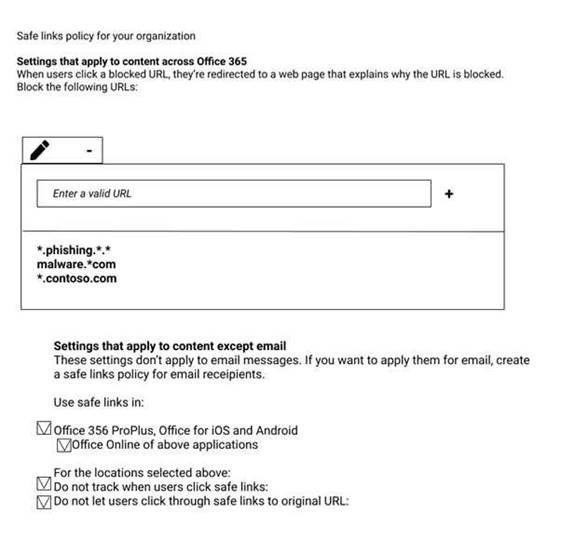
Which URL can a user safely access from Microsoft Word Online?
- A. fabrikam.phishing.fabrikam.com
- B. malware.fabrikam.com
- C. fabrikam.contoso.com
- D. www.malware.fabrikam.com
Answer: D
Explanation:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/set-up-a-custom-blocked-urls-list- wtih-atp
NEW QUESTION 11
HOTSPOT
You have a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. OneDrive stores files that are shared with external users. The files are configured as shown in the following table.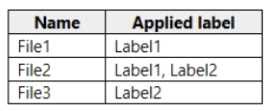
You create a data loss prevention (DLP) policy that applies to the content stored in OneDrive accounts. The policy contains the following three rules:
•Rulel:
•Conditions: Label 1, Detect content that's shared with people outside my organization
•Actions: Restrict access to the content for external users
•User notifications: Notify the user who last modified the content
•User overrides: On
•Priority: 0
•Rule2:
•Conditions: Label 1 or Label2
•Actions: Restrict access to the content
•Priority: 1
•Rule3:
•Conditions: Label2, Detect content that's shared with people outside my organization
•Actions: Restrict access to the content for external users
•User notifications: Notify the user who last modified the content
•User overrides: On
•Priority: 2
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 12
You have a Microsoft 365 subscription.
Yesterday, you created retention labels and published the labels to Microsoft Exchange Online mailboxes.
You need to ensure that the labels will be available for manual assignment as soon as possible. What should you do?
- A. From the Security & Compliance admin center, create a label policy
- B. From Exchange Online PowerShell, run Start-RetentionAutoTagLearning
- C. From Exchange Online PowerShell, run Start-ManagedFolderAssistant
- D. From the Security & Compliance admin center, create a data loss prevention (DLP) policy
Answer: C
NEW QUESTION 13
DRAG DROP
You have a Microsoft 365 E5 subscription.
All computers run Windows 10 and are onboarded to Windows Defender Advanced Threat Protection (Windows Defender ATP).
You create a Windows Defender machine group named MachineGroupl.
You need to enable delegation for the security settings of the computers in MachineGroupl.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.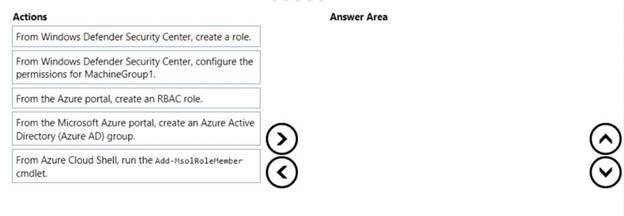
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 14
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in Security & Compliance to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1. You run the Set-AuditConfig -Workload Exchange command.
Does that meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
References:
https://docs.microsoft.com/en-us/powershell/module/exchange/policy-and-compliance-audit/set-auditconfig?view=exchange-ps
NEW QUESTION 15
HOTSPOT
You have the Microsoft conditions shown in the following table.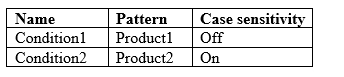
You have the Azure Information Protection labels shown in the following table.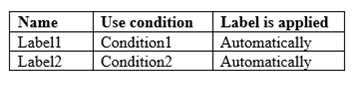
You have the Azure Information Protection policies shown in the following table.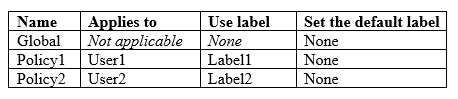
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 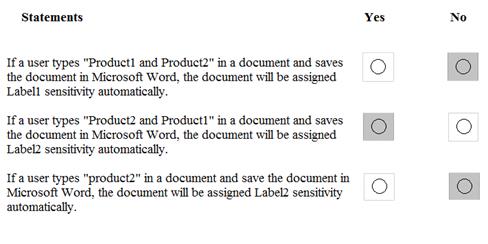
NEW QUESTION 16
You have a Microsoft 365 subscription.
You need to be notified by email whenever an administrator starts an eDiscovery search. What should you do from the Security & Compliance admin center?
- A. From Search & investigation, create a guided search.
- B. From Events, create an event.
- C. From Alerts, create an alert policy.
- D. From Search & Investigation, create an eDiscovery case.
Answer: C
Explanation:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/alert-policies
NEW QUESTION 17
You create a data loss prevention (DLP) policy as shown in the following shown: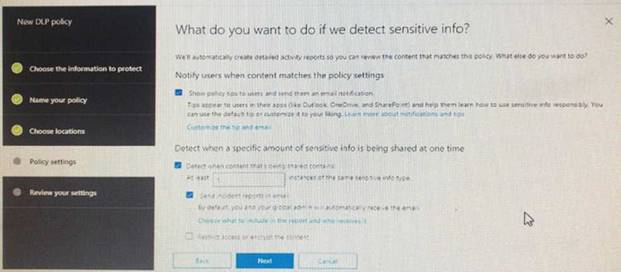
What is the effect of the policy when a user attempts to send an email messages that contains sensitive information?
- A. The user receives a notification and can send the email message
- B. The user receives a notification and cannot send the email message
- C. The email message is sent without a notification
- D. The email message is blocked silently
Answer: A
Explanation:
https://docs.microsoft.com/en-us/office365/securitycompliance/data-loss-prevention-policies
NEW QUESTION 18
Your company has 500 computers.
You plan to protect the computers by using Windows Defender Advanced Threat Protection (Windows
Defender ATP). Twenty of the computers belong to company executives.
You need to recommend a remediation solution that meets the following requirements: Windows Defender ATP administrators must manually approve all remediation for the executives
Remediation must occur automatically for all other users
What should you recommend doing from Windows Defender Security Center?
- A. Configure 20 system exclusions on automation allowed/block lists
- B. Configure two alert notification rules
- C. Download an offboarding package for the computers of the 20 executives
- D. Create two machine groups
Answer: D
Explanation:
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/machine-groupswindows-defender-advanced-threat-protection
NEW QUESTION 19
HOTSPOT
You have a Microsoft 365 subscription. From the Security & Compliance admin center, you create the retention policies shown in the following table.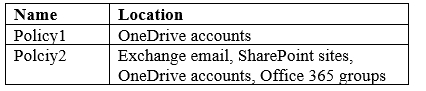
Policy1 if configured as showing in the following exhibit.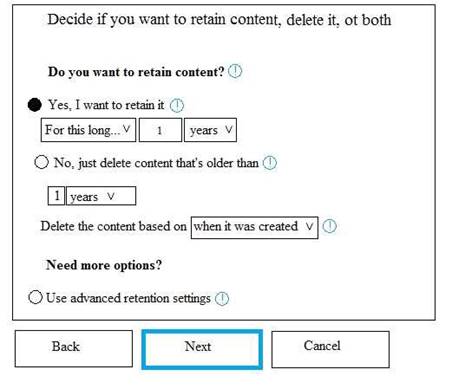
Policy2 is configured as shown in the following exhibit.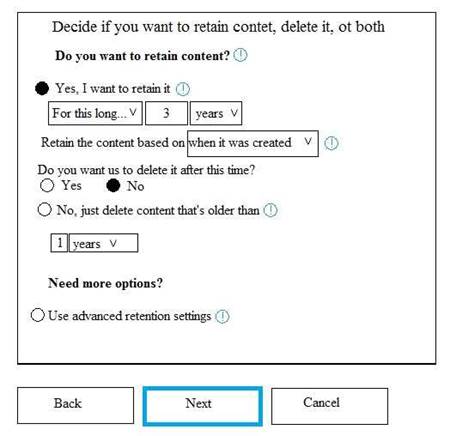
For each of the following statements, select Yes if the statement is true. Otherwise, select No.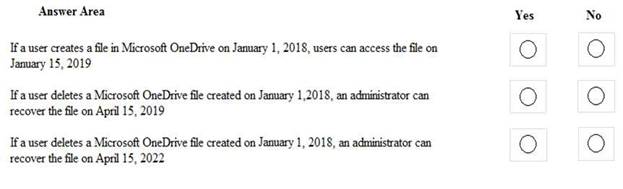
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/retention-policies?redirectSourcePath=%252fen-us%252farticle%252fOverview-of-retention-policies-5e377752-700d-4870-9b6d-12bfc12d2423#the-principles-of-retention-or-what-takes-precedence
NEW QUESTION 20
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises Active Directory domain named contoso.com.
You install and run Azure AD Connect on a server named Server1 that runs Windows Server. You need to view Azure AD Connect events.
You use the Directory Service event log on Server1. Does that meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
References:
https://support.pingidentity.com/s/article/PingOne-How-to-troubleshoot-an-AD-Connect-Instance
NEW QUESTION 21
......
100% Valid and Newest Version MS-500 Questions & Answers shared by Passcertsure, Get Full Dumps HERE: https://www.passcertsure.com/MS-500-test/ (New 114 Q&As)
- Microsoft AZ-302 Torrent 2021
- Microsoft 70-333 Study Guides 2021
- What Tested PL-500 Training Materials Is
- All About Exact 70-461 dumps
- The Updated Guide To 70-535 dumps
- Breathing 70-341 Exam Questions 2021
- Realistic 70-742 Free Practice Questions 2021
- Up to date Microsoft 70-533 pdf
- Down to date Microsoft 70-410 practice test
- Microsoft 70-741 Dumps Questions 2021


