98-367 Exam Questions - Online Test
98-367 Premium VCE File

150 Lectures, 20 Hours
Want to know Pass4sure 98-367 Exam practice test features? Want to lear more about Microsoft MTA Security Fundamentals Practice Test certification experience? Study Verified Microsoft 98-367 answers to Update 98-367 questions at Pass4sure. Gat a success with an absolute guarantee to pass Microsoft 98-367 (MTA Security Fundamentals Practice Test) test on your first attempt.
NEW QUESTION 1
Bridging is a process of sending packets from source to destination on OSI layer 3.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
- A. Routing
- B. Switching
- C. Repeating
- D. No change is needed.
Answer: A
NEW QUESTION 2
Humongous Insurance is an online healthcare insurance company. During an annual security audit a security firm tests the strength of the company's password policy and suggests that Humongous Insurance implement password history policy.
What is the likely reason that the security firm suggests this?
- A. Past passwords were easily cracked by the brute force method.
- B. Past passwords of users contained dictionary words.
- C. Previous password breaches involved use of past passwords.
- D. Past passwords lacked complexity and special characters.
Answer: B
NEW QUESTION 3
The client computers on your network are stable and do not need any new features. Which is a benefit of applying operating system updates to these clients?
- A. Keep the software licensed
- B. Keep the server ports available
- C. Update the hardware firewall
- D. Close existing vulnerabilities
Answer: D
NEW QUESTION 4
You are an intern at Wide World Importers and help manage 1000 workstations. All the workstations are members of an Active Domain.
You need to push out an internal certificate to Internet Explorer on all workstations. What is the quickest method to do this?
- A. Local policy
- B. Logon script
- C. Windows Update
- D. Group policy
Answer: A
NEW QUESTION 5
HOTSPOT
Alice sends her password to the game server in plaintext. Chuck is able to observe her password as shown in the following image:
Use the drop-down menus to select the answer choice that completes each statement.
Each correct selection is worth one point.
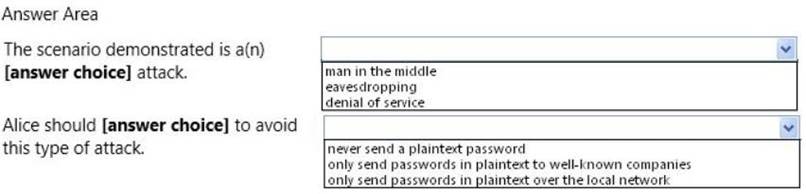
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 6
What does NAT do?
- A. It encrypts and authenticates IP packets.
- B. It provides caching and reduces network traffic.
- C. It translates public IP addresses to private addresses and vice versa.
- D. It analyzes incoming and outgoing traffic packets.
Answer: C
Explanation:
Reference: http://en.wikipedia.org/wiki/Network_address_translation
NEW QUESTION 7
The primary purpose of Network Access Protection (NAP) is to prevent:
- A. Loss of data from client computers on a network.
- B. Non-compliant systems from connecting to a network.
- C. Users on a network from installing software.
- D. Unauthorized users from accessing a network.
Answer: B
Explanation:
NAP enforces health policies by inspecting and assessing the health of client computers, restricting network access when client computers are noncompliant with health policy, and remediating noncompliant client computers to bring them into compliance with health policy before they are granted full network access. NAP enforces health policies on client computers that are attempting to connect to a network; NAP also provides ongoing health compliance enforcement while a client computer is connected to a network. Reference: http://technet.microsoft.com/en-us/library/cc754378(v=ws.10).aspx
NEW QUESTION 8
Account lockout policies are used to prevent which type of security attack?
- A. Brute force attacks
- B. Users sharing passwords
- C. Social engineering
- D. Passwords being reused immediately
Answer: A
NEW QUESTION 9
An attorney hires you to increase the wireless network security for the law firm's office. The office has a very basic network, with just a modem and a router.
Which of these security modes offers the highest security?
- A. WPA-Personal
- B. WEP
- C. WPA2-Personal
- D. WPA-Enterprise
Answer: C
NEW QUESTION 10
Many Internet sites that you visit require a user name and password. How should you secure these passwords?
- A. Save them to a text file
- B. Enable session caching
- C. Configure the browser to save passwords
- D. Save them to an encrypted file
- E. Reuse the same password
Answer: D
NEW QUESTION 11
The purpose of a digital certificate is to verify that a:
- A. Public key belongs to a sender.
- B. Computer is virus-free.
- C. Private key belongs to a sender.
- D. Digital document is complete.
Answer: A
Explanation:
In cryptography, a public key certificate (also known as a digital certificate or identity certificate) is an electronic document that uses a digital signature to bind a public key with an identity.
NEW QUESTION 12
E-mail spoofing:
- A. Forwards e-mail messages to all contacts
- B. Copies e-mail messages sent from a specific user
- C. Obscures the true e-mail sender
- D. Modifies e-mail routing logs
Answer: C
Explanation:
Reference: http://www.microsoft.com/mscorp/safety/technologies/senderid/technology.mspx
NEW QUESTION 13
Keeping a server updated:
- A. Maximizes network efficiency
- B. Fixes security holes
- C. Speeds up folder access
- D. Synchronizes the server
Answer: B
NEW QUESTION 14
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 15
Password history policies are used to prevent:
- A. Brute force attacks
- B. Users from sharing passwords
- C. Social engineering
- D. Passwords from being reused immediately
Answer: D
Explanation:
This security setting determines the number of unique new passwords that have to be associated with a user account before an old password can be reused. The value must be between 0 and 24 passwords.
This policy enables administrators to enhance security by ensuring that old passwords are not reused continually.
Reference: http://technet.microsoft.com/en-us/library/cc758950(v=ws.10).aspx
NEW QUESTION 16
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.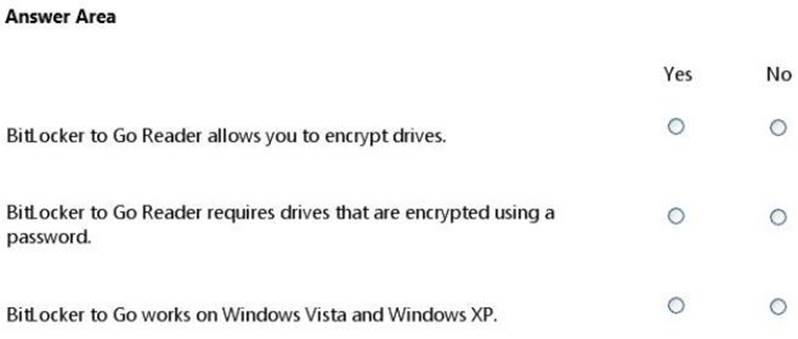
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 17
What is a common method for password collection?
- A. Email attachments
- B. Back door intrusions
- C. SQL Injection
- D. Network sniffers
Answer: D
NEW QUESTION 18
The Active Directory controls, enforces, and assigns security policies and access rights for all users.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
- A. NTFS permissions
- B. User Account Control
- C. Registry
- D. No change is needed
Answer: D
NEW QUESTION 19
The Graphic Design Institute hires you to help them set up a server for their 20-person team.
As a general practice of hardening the server, you start by performing which two tasks? (Choose two.)
- A. Disable the guest account.
- B. Rename the admin account.
- C. Remove the account lockout policy.
- D. Format partitions with FAT32.
Answer: AB
NEW QUESTION 20
What is an example of non-propagating malicious code?
- A. A back door
- B. A hoax
- C. A Trojan horse
- D. A worm
Answer: A
NEW QUESTION 21
Which type of firewall allows for inspection of all characteristics of a packet?
- A. NAT
- B. Stateful
- C. Stateless
- D. Windows Defender
Answer: B
Explanation:
Reference: http://en.wikipedia.org/wiki/Stateful_firewall
NEW QUESTION 22
What is the standard or basic collection of NTFS permissions?
- A. Read and execute, read, write, full control, modify, list folder contents
- B. Change permissions, read permissions, write permissions
- C. Read attributes, list folder/read data, traverse folder/execute file
- D. Create files/write data, create folders/append data, take ownership
Answer: A
Explanation:
Reference: http://technet.microsoft.com/en-us/library/bb727008.aspx
NEW QUESTION 23
......
P.S. Dumpscollection now are offering 100% pass ensure 98-367 dumps! All 98-367 exam questions have been updated with correct answers: http://www.dumpscollection.net/dumps/98-367/ (163 New Questions)
- The Most recent Guide To 70-535 practice test
- Microsoft 70-774 Dumps 2021
- Far Out AZ-104 Free Demo 2021
- Replace Microsoft 70-410 exam question
- Far out Microsoft 70-410 exam dumps
- Microsoft AZ-301 Dumps Questions 2021
- 10 Tips For Far out 70-410 exam dumps
- Download AZ-100 Dumps Questions 2021
- The Updated Guide To AZ-303 Dump
- 10 Tips For Most up-to-date 70-462 braindumps


