300-210 Exam Questions - Online Test
300-210 Premium VCE File

150 Lectures, 20 Hours
We provide real 300-210 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Cisco 300-210 Exam quickly & easily. The 300-210 PDF type is available for reading and printing. You can print more and practice many times. With the help of our Cisco 300-210 dumps pdf and vce product and material, you can easily pass the 300-210 exam.
Online 300-210 free questions and answers of New Version:
NEW QUESTION 1
What is the function of the Web Proxy Auto-Discovery protocol?
- A. It enables a web client to discover the URL of a configuration file.
- B. It enables a web client to download a script or configuration file that is named by a URL.
- C. It enables a web client's traffic flows to be redirected in real time.
- D. It enables web clients to dynamically resolve hostname records.
Answer: A
NEW QUESTION 2
With Firepower Threat Defense, which two interface settings are required when configuring a routed interface? (Choose two.)
- A. Speed
- B. Duplex
- C. Media Type
- D. Redundant Interface
- E. EtherChannel
Answer: AB
NEW QUESTION 3
The Web Cache Communication Protocol (WCCP) is a content-routing protocol that can facilitate the redirection of traffic flows in real time. Your organization has deployed WCCP to redirect web traffic that traverses their Cisco Adaptive Security Appliances (ASAs) to their Cisco Web Security Appliances (WSAs).
The simulator will provide access to the graphical user interfaces of one Cisco ASA and one Cisco WSA that are participating in a WCCP service. Not all aspects of the GUIs are implemented in the simulator. The options that have been implemented are sufficient to determine the best answer to each of the questions that are presented.
Your task is to examine the details available in the simulated graphical user interfaces and select the best answer.

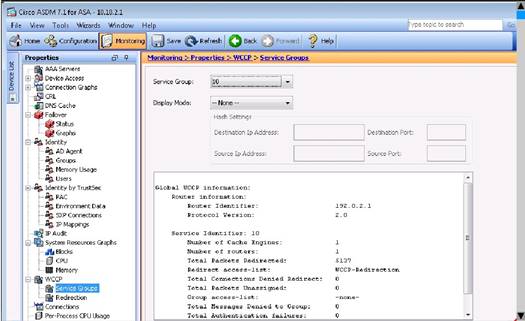
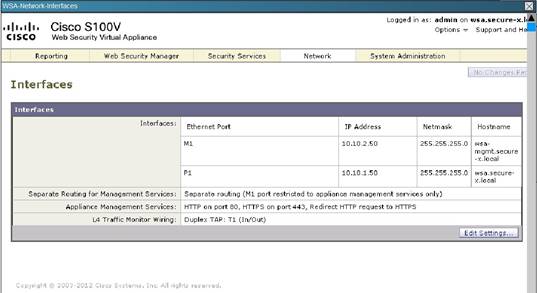
What traffic is not redirected by WCCP?
- A. Traffic destined to public address space
- B. Traffic sent from public address space
- C. Traffic destined to private address space
- D. Traffic sent from private address space
Answer: B
Explanation:
From the screen shot below we see the WCCP-Redirection ACL is applied, so all traffic from the Private IP space to any destination will be redirected.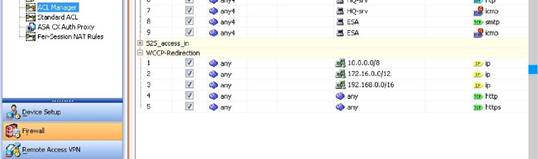
NEW QUESTION 4
Which Cisco technology secures the network through malware filtering, category-based control, and reputation-based control?
- A. Cisco ASA 5500 Series appliances
- B. Cisco remote-access VPNs
- C. Cisco IronPort WSA
- D. Cisco IPS
Answer: C
NEW QUESTION 5
What are three best practices for a Cisco Intrusion Prevention System? (Choose three.)
- A. Checking for new signatures every 4 hours
- B. Checking for new signatures on a staggered schedule
- C. Automatically updating signature packs
- D. Manually updating signature packs
- E. Group tuning of signatures
- F. Single tuning of signatures
Answer: BCE
NEW QUESTION 6
Which two are valid suppression types on a Cisco Next Generation Intrusion Prevention System?
- A. Port
- B. Rule
- C. Source
- D. Application
- E. Protocol
Answer: BC
NEW QUESTION 7
A network administrator noticed all traffic that is redirected to the cisco WSA from ASA firewall is unable to get to the internet in a transparent proxy environment using WCCP.
- A. Ping the WCCP device
- B. Explicity point to the browser to the proxy
- C. Disable WCCP
- D. Check WCCP logs in debug mode to check there are no pending HIA or ISY request
Answer: D
NEW QUESTION 8
Which Cisco ASA SSL VPN feature provides support for PCI compliance by allowing for the validation of two sets of username and password credentials on the SSL VPN login page?
- A. Single Sign-On
- B. Certificate to Profile Mapping
- C. Double Authentication
- D. RSA OTP
Answer: D
NEW QUESTION 9
Which Cisco technology prevents targeted malware attacks, provides data loss prevention and spam protection, and encrypts email?
- A. SBA
- B. secure mobile access
- C. IPv6 DMZ web service
- D. ESA
Answer: D
NEW QUESTION 10
A system administrator wants to know if the email traffic from a remote partner will active special treatment message filters that are created just for them. Which tool on the Cisco Email Security gateway can you use to debug and emulate the flow that a message takes through the work queue?
- A. the trace tool
- B. centralized or local message tracking
- C. the CLI findevent command
- D. the CLI grep command
- E. the message tracker interface
Answer: A
NEW QUESTION 11
Which three statements about threat ratings are true? (Choose three.)
- A. A threat rating is equivalent to a risk rating that has been lowered by an alert rating.
- B. The largest threat rating from all actioned events is added to the risk rating.
- C. The smallest threat rating from all actioned events is subtracted from the risk rating.
- D. The alert rating for deny-attacker-inline is 45.
- E. Unmitigated events do not cause a threat rating modification.
- F. The threat rating for deny-attacker-inline is 50.
Answer: ADE
NEW QUESTION 12
A system administrator wants to know if the email traffic from a remote partner will activate special treatment message filters that are created just for them. Which tool on the Cisco Email Security gateway can you use to debug or emulate the flow that a message takes through the work queue?
- A. the message tracker interface
- B. centralized or local message tracking
- C. the CLI findevent command
- D. the trace tool
- E. the CLI grep command
Answer: D
NEW QUESTION 13
Which settings are required when deploying Cisco IPS in high-availability mode using EtherChannel load balancy?
- A. ECLB IPS appliances must be in on-a-stick mode, ECLB IPS solution maintains state if a sensor goes down, and TCP flow is forced through the same IPS appliance.
- B. ECLB IPS appliances must not be in on-a-stick mode, ECLB IPS solution maintains state if a sensor goes down, and TCP flow is forced through the same IPS appliance flow
- C. ECLB IPS appliances must be in on-a-stick mode, ECLB IPS solution does not maintain state if a sensor goes down, and TCP flow is forced through a different IPS appliance.
- D. ECLB IPS appliances must not be in on-a-stick mode, ECLB IPS solution does not maintain state if a sensor goes down, and TCP flow is forced through a different IPS appliance.
Answer: C
Explanation:
http://www.cisco.com/en/US/products/hw/vpndevc/ps4077/products_configuration_example09186 a0080671a8d.shtml
NEW QUESTION 14
Which action cloud reduce the security of the management interface of the Cisco ESA appliance?
- A. Assign delegated administrator roles to engineers who manage the mail policies.
- B. create a network access list to allow all connections to the management interface
- C. Display a login banner indicating that all appliance use is logged and reviewed
- D. configure a web UI session timeout of 30 minutes for connected users.
Answer: A
NEW QUESTION 15
Which two routing options are valid with cisco firePOWER threat Defense version 6.0?(choose two)
- A. ECMP with up to three equal cost paths across multiple interfaces
- B. BGPv6
- C. BGPv4 with nonstop forwarding
- D. BGPv4 unicast address family
- E. ECMP with up to four equal cost paths
Answer: AD
NEW QUESTION 16
Which option describes how the native VLAN is set up on an IPS sensor when VLAN groups are used in an inline deployment of the sensor?
- A. The sensor looks at the native VLAN setup on the switch to determine the correct native VLAN to use.
- B. The sensor does not care about VLANs.
- C. A default VLAN variable must be associated with each physical interface on the sensor.
- D. There is no way to set this, so you need to tag all traffic.
- E. ISL links are only supported.
Answer: C
NEW QUESTION 17
Which object can be used on a Cisco FirePOWER appliance, but not in an access control policy rule on Cisco FirePOWER services running on a Cisco ASA?
- A. URL
- B. security intelligence
- C. VLAN
- D. geolocation
Answer: C
NEW QUESTION 18
In the predefined URL category filtering configuration page in a cisco WSA, which two actions are valid?
- A. Restrict
- B. Guarantee
- C. Block
- D. Notification
- E. Time based
Answer: AD
NEW QUESTION 19
An engineer manages a Cisco Intrusion Prevention System via IME. A new user must be able to tune signatures, but must not be able to create new users. Which role for the new user is correct?
- A. viewer
- B. service
- C. operator
- D. administrator
Answer: C
Explanation:
http://www.cisco.com/c/en/us/td/docs/security/ips/7-0/command/reference/cmdref/crIntro.html
NEW QUESTION 20
Which policy is used to capture host information on the Cisco Next Generation Intrusion Prevention System?
- A. network discovery
- B. correlation
- C. intrusion
- D. access control
Answer: C
NEW QUESTION 21
What is the function of the Cisco Context Adaptive Scanning Engine in Cisco Hybrid Email Security services?
- A. It uses real-time traffic threat assessment to identify suspicious email senders and messages.
- B. It provides a preventive defense against viruses by scanning messages before they enter the network.
- C. It analyzes message content and attachments to protect an organization's intellectual property.
- D. It protects against blended threats by using human-like logic to review and evaluate traffic.
Answer: D
NEW QUESTION 22
Which redundancy protocol is available for Cisco firepower but is a limitation for the WSA?
- A. VVRP
- B. HSRP
- C. SFRP
- D. GLBR
Answer: C
NEW QUESTION 23
What is a value that Cisco ESA can use for tracing mail flow?
- A. the source IP address
- B. the FQDN of the destination IP address
- C. the destination IP address
- D. the FQDN of the source IP address
Answer: D
NEW QUESTION 24
With Cisco AMP for Endpoints on Windows, which three engines are available in the connector? (Choose three. )
- A. Ethos
- B. Tetra
- C. Annos
- D. Spero
- E. Talos
- F. ClamAV
Answer: ABD
Explanation:
http://www.cisco.com/c/en/us/products/collateral/security/fireamp-private-cloud-virtual-appliance/datasheet-c780.html
NEW QUESTION 25
Which two conditions must you configure in an event action rule to match all IPv4 addresses in the victim range and filter on the complete subsignature range? (Choose two.)
- A. Disable event action override.
- B. Leave the victim address range unspecified.
- C. Set the subsignature ID-range to the default.
- D. Set the deny action percentage to 100.
- E. Set the deny action percentage to 0.
Answer: BC
NEW QUESTION 26
Which two commands are valid URL filtering commands? (Choose two.)
- A. url-server (DMZ) vendor smartfilter host 10.0.1.1
- B. url-server (DMZ) vendor url-filter host 10.0.1.1
- C. url-server (DMZ) vendor n2h2 host 10.0.1.1
- D. url-server (DMZ) vendor CISCO host 10.0.1.1
- E. url-server (DMZ) vendor web host 10.0.1.1
Answer: AC
NEW QUESTION 27
......
P.S. Easily pass 300-210 Exam with 481 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam 300-210 Dumps: https://www.surepassexam.com/300-210-exam-dumps.html (481 New Questions)
- What Free 300-075 exam dumps Is?
- A Review Of Free 300-115 exam
- What Verified 400-051 braindumps Is?
- 10 Tips For Regenerate 300-206 exam question
- All About Exact 300-101 practice test
- The Leading Guide To 300-075 exam
- Update 200-301 Dumps 2021
- Guaranteed CCNP Collaboration 300-070 pdf
- What High Value 350-601 Free Samples Is
- The Secret of Cisco 300-135 examcollection


