156-215.80 Exam Questions - Online Test
156-215.80 Premium VCE File

150 Lectures, 20 Hours
Act now and download your Check-Point 156-215.80 test today! Do not waste time for the worthless Check-Point 156-215.80 tutorials. Download Rebirth Check-Point Check Point Certified Security Administrator exam with real questions and answers and begin to learn Check-Point 156-215.80 with a classic professional.
Online 156-215.80 free questions and answers of New Version:
NEW QUESTION 1
You are going to upgrade from R77 to R80. Before the upgrade, you want to back up the system so that, if there are any problems, you can easily restore to the old version with all configuration and management files intact. What is the BEST backup method in this scenario?
- A. backup
- B. Database Revision
- C. snapshot
- D. migrate export
Answer: C
Explanation:
2. Snapshot Management
The snapshot creates a binary image of the entire root (lv_current) disk partition. This includes Check Point products, configuration, and operating system.
Starting in R77.10, exporting an image from one machine and importing that image on another machine of the same type is supported.
The log partition is not included in the snapshot. Therefore, any locally stored FireWall logs will not be save
NEW QUESTION 2
You have successfully backed up your Check Point configurations without the OS information. What command would you use to restore this backup?
- A. restore_backup
- B. import backup
- C. cp_merge
- D. migrate import
Answer: A
NEW QUESTION 3
Which of the following is NOT a back up method?
- A. Save backup
- B. System backup
- C. snapshot
- D. Migrate
Answer: A
Explanation:
The built-in Gaia backup procedures:
Snapshot Management
System Backup (and System Restore)
Save/Show Configuration (and Load Configuration)
Check Point provides three different procedures for backing up (and restoring) the operating system and networking parameters on your appliances.
Snapshot (Revert)
Backup (Restore)
upgrade_export (Migrate) References:
NEW QUESTION 4
What must a Security Administrator do to comply with a management requirement to log all traffic accepted through the perimeter Security Gateway?
- A. In Global Properties > Reporting Tools check the box Enable tracking all rules (including rules marked as None in the Track column). Send these logs to a secondary log server for a complete logging histor
- B. Use your normal log server for standard logging for troubleshooting.
- C. Install the View Implicit Rules package using SmartUpdate.
- D. Define two log servers on the R77 Gateway objec
- E. Lof Implied Rules on the first log serve
- F. Enable Log Rule Base on the second log serve
- G. Use SmartReporter to merge the two log server records into the same database for HIPPA log audits.
- H. Check the Log Implied Rules Globally box on the R77 Gateway object.
Answer: A
NEW QUESTION 5
Two administrators Dave and Jon both manage R80 Management as administrators for ABC Corp. Jon logged into the R80 Management and then shortly after Dave logged in to the same server. They are both in the Security Policies view. From the screenshots below, why does Dave not have the rule no.6 in his SmartConsole view even though Jon has it his in his SmartConsole view?
- A. Jon is currently editing rule no.6 but has Published part of his changes.
- B. Dave is currently editing rule no.6 and has marked this rule for deletion.
- C. Dave is currently editing rule no.6 and has deleted it from his Rule Base.
- D. Jon is currently editing rule no.6 but has not yet Published his changes.
Answer: D
Explanation:
When an administrator logs in to the Security Management Server through SmartConsole, a new editing session starts. The changes that the administrator makes during the session are only available to that administrator. Other administrators see a lock icon on object and rules that are being edited. To make changes available to all administrators, and to unlock the objects and rules that are being edited, the administrator must publish the session.
NEW QUESTION 6
The security Gateway is installed on GAiA R80 The default port for the WEB User Interface is ____.
- A. TCP 18211
- B. TCP 257
- C. TCP 4433
- D. TCP 443
Answer: D
NEW QUESTION 7
You work as a security administrator for a large company. CSO of your company has attended a security conference where he has learnt how hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. He wants to make sure that his company has the right protections in place. Check Point has been selected for the security vendor. Which Check Point products protects BEST against malware and zero-day attacks while ensuring quick delivery of safe content to your users?
- A. IPS and Application Control
- B. IPS, anti-virus and anti-bot
- C. IPS, anti-virus and e-mail security
- D. SandBlast
Answer: D
Explanation:
SandBlast Zero-Day Protection
Hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. Zero-day exploit protection from Check Point provides a deeper level of inspection so you can prevent more malware and zero-day attacks, while ensuring quick delivery of safe content to your users.
NEW QUESTION 8
How do you configure an alert in SmartView Monitor?
- A. An alert cannot be configured in SmartView Monitor.
- B. By choosing the Gateway, and Configure Thresholds.
- C. By right-clicking on the Gateway, and selecting Properties.
- D. By right-clicking on the Gateway, and selecting System Information.
Answer: B
NEW QUESTION 9
Which of the following is NOT a valid option when configuring access for Captive Portal?
- A. From the Internet
- B. Through internal interfaces
- C. Through all interfaces
- D. According to the Firewall Policy
Answer: A
NEW QUESTION 10
Where can administrator edit a list of trusted SmartConsole clients in R80?
- A. cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server.
- B. Only using SmartConsole: Manage and Settings > Permissions and Administrators > Advanced > Trusted Clients.
- C. In cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server, in SmartConsole: Manage and Settings>Permissions and Administrators>Advanced>Trusted Clients.
- D. WebUI client logged to Security Management Server, SmartDashboard: Manage and Settings>Permissions and Administrators>Advanced>Trusted Clients, via cpconfig on a Security Gateway.
Answer: C
NEW QUESTION 11
Which method below is NOT one of the ways to communicate using the Management API’s?
- A. Typing API commands using the “mgmt_cli” command
- B. Typing API commands from a dialog box inside the SmartConsole GUI application
- C. Typing API commands using Gaia’s secure shell (clash)19+
- D. Sending API commands over an http connection using web-services
Answer: D
NEW QUESTION 12
Which of the following is NOT an advantage to using multiple LDAP servers?
- A. You achieve a faster access time by placing LDAP servers containing the database at remote sites
- B. Information on a user is hidden, yet distributed across several servers
- C. You achieve compartmentalization by allowing a large number of users to be distributed across several servers
- D. You gain High Availability by replicating the same information on several servers
Answer: B
NEW QUESTION 13
NAT can NOT be configured on which of the following objects?
- A. HTTP Logical Server
- B. Gateway
- C. Address Range
- D. Host
Answer: A
NEW QUESTION 14
Which path below is available only when CoreXL is enabled?
- A. Slow path
- B. Firewall path
- C. Medium path
- D. Accelerated path
Answer: C
NEW QUESTION 15
Ken wants to obtain a configuration lock from other administrator on R80 Security Management Server. He can do this via WebUI or a via CLI. Which command should be use in CLI? Choose the correct answer.
- A. remove database lock
- B. The database feature has one command lock database override.
- C. override database lock
- D. The database feature has two commands: lock database override and unlock databas
- E. Both will work.
Answer: D
Explanation:
Use the database feature to obtain the configuration lock. The database feature has two commands:
lock database [override].
unlock database
The commands do the same thing: obtain the configuration lock from another administrator.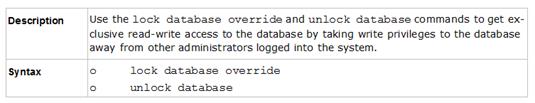
NEW QUESTION 16
Traffic from source 192.168.1.1 is going to www.google.com. The Application Control Blade on the gateway is inspecting the traffic. Assuming acceleration is enable which path is handling the traffic?
- A. Slow Path
- B. Medium Path
- C. Fast Path
- D. Accelerated Path
Answer: A
NEW QUESTION 17
What is the purpose of Captive Portal?
- A. It provides remote access to SmartConsole
- B. It manages user permission in SmartConsole
- C. It authenticates users, allowing them access to the Internet and corporate resources
- D. It authenticates users, allowing them access to the Gaia OS
Answer: C
Explanation:
Captive Portal – a simple method that authenticates users through a web interface before granting them access to Intranet resources. When users try to access a protected resource, they get a web page that
must be filled out to continue.
Reference : https://www.checkpoint.com/products/identity-awareness-software-blade/
NEW QUESTION 18
You have just installed your Gateway and want to analyze the packet size distribution of your traffic with SmartView Monitor.
Unfortunately, you get the message:
“There are no machines that contain Firewall Blade and SmartView Monitor”.
What should you do to analyze the packet size distribution of your traffic? Give the BEST answer.
- A. Purchase the SmartView Monitor license for your Security Management Server.
- B. Enable Monitoring on your Security Management Server.
- C. Purchase the SmartView Monitor license for your Security Gateway.
- D. Enable Monitoring on your Security Gateway.
Answer: D
NEW QUESTION 19
Which of the following uses the same key to decrypt as it does to encrypt?
- A. Asymmetric encryption
- B. Dynamic encryption
- C. Certificate-based encryption
- D. Symmetric encryption
Answer: D
NEW QUESTION 20
You have configured SNX on the Security Gateway. The client connects to the Security Gateway and the user enters the authentication credentials. What must happen after authentication that allows the client to connect to the Security Gateway's VPN domain?
- A. SNX modifies the routing table to forward VPN traffic to the Security Gateway.
- B. An office mode address must be obtained by the client.
- C. The SNX client application must be installed on the client.
- D. Active-X must be allowed on the client.
Answer: A
NEW QUESTION 21
Which option would allow you to make a backup copy of the OS and Check Point configuration, without stopping Check Point processes?
- A. All options stop Check Point processes
- B. backup
- C. migrate export
- D. snapshot
Answer: D
NEW QUESTION 22
What is the benefit of Manual NAT over Automatic NAT?
- A. If you create a new Security Policy, the Manual NAT rules will be transferred to this new policy
- B. There is no benefit since Automatic NAT has in any case higher priority over Manual NAT
- C. You have the full control about the priority of the NAT rules
- D. On IPSO and GAIA Gateways, it is handled in a Stateful manner
Answer: C
NEW QUESTION 23
What is the purpose of the Clean-up Rule?
- A. To log all traffic that is not explicitly allowed or denied in the Rule Base.
- B. To clean up policies found inconsistent with the compliance blade reports.
- C. To remove all rules that could have a conflict with other rules in the database.
- D. To eliminate duplicate log entries in the Security Gateway
Answer: A
NEW QUESTION 24
......
P.S. 2passeasy now are offering 100% pass ensure 156-215.80 dumps! All 156-215.80 exam questions have been updated with correct answers: https://www.2passeasy.com/dumps/156-215.80/ (485 New Questions)
- The Secret Of Check-Point 156-315.80 Latest Exam
- Regenerate 156-215.77 Keys 2021
- Leading 156-315.80 Exam Engine For Check Point Certified Security Expert - R80 Certification
- The Renovate Guide To 156-315.80 Free Practice Questions
- Top Quality Check-Point 156-315.80 Exam Online
- The Secret Of Check-Point 156-315.80 Exam Engine
- Abreast Of The Times 156-315.80 Vce For Check Point Certified Security Expert - R80 Certification
- The Secret Of Check-Point 156-215.80 Free Exam Questions
- Up To Date 156-315.80 Testing Software For Check Point Certified Security Expert - R80 Certification


